Identity security is no longer just about people. Non-human identities (NHIs) now outnumber humans by 25-50x and have become one of the most important elements of modern cloud security.
Every application, microservice, automation pipeline, and AI workflow depends on machine-generated credentials to function. These identities outnumber human ones many times over, and they operate across clouds, runtimes, and delivery pipelines at speeds that traditional identity systems were never designed to support. And when those identities are unmanaged or scattered across tools and codebases, organizations face significant operational and security risks.
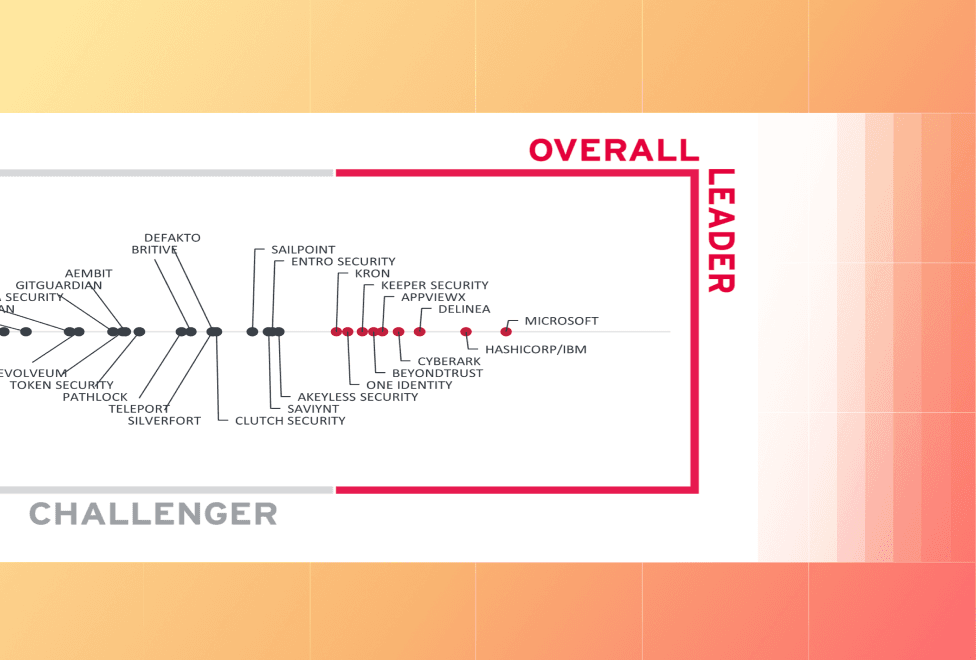
Given the importance of NHIs, we’re honored to share that HashiCorp, an IBM Company, has been named an Overall Leader in the 2025 KuppingerCole Leadership Compass for Non-Human Identities Management.
All of this aligns with what we hear from customers every day. The scale of NHIs is growing rapidly and they are struggling to gain clarity and control over their growing identity footprint. In this post, we’ll dive into the state of NHI access management and provide some tips on how you can address these challenges.
»KuppingerCole 2025 Leadership Compass
The 2025 KuppingerCole Leadership Compass for Non-Human Identities Management evaluated vendors based on product capabilities, innovation, and market presence. HashiCorp, an IBM Company, was named a leader in all 4 categories: Overall Leader, Product Leader, Innovation Leader, and Market Leader, reflecting the strength of the combined HashiCorp and IBM solution and our continued investment in securing NHIs across the entire lifecycle and in any environment.
»The state of non-human identity
Modern infrastructure creates machine identities constantly. A single deployment pipeline can generate dozens of secrets, tokens, and temporary credentials as part of build, test, and runtime activities. Multiply that by hundreds of services and several cloud providers, and the identity surface quickly balloons past anything that can be managed manually.
Several trends shape the current state of NHI security:
-
Non-human identities far exceed human identities. Hybrid cloud, microservices, and distributed applications generate identities automatically and continuously.
-
Agentic AI is introducing a new category of autonomous non-human actors. AI agents can call APIs, launch jobs, modify configurations, and trigger workflows completely on their own. Each action requires authenticated machine-level access, creating an entirely new layer of ephemeral, fast-moving identities that must be governed just as rigorously as any other workload.
-
Credentials remain static or unmanaged. Hard-coded secrets, duplicated credentials, abandoned tokens, and service accounts without clear ownership continue to pose risk across pipelines and cloud environments.
-
Traditional PAM approaches struggle with dynamic workloads. Systems built for human access do not issue short-lived credentials easily, and they do not fit naturally into automated CI/CD or infrastructure as code workflows.
-
Hybrid and multi-cloud environments contribute to identity fragmentation. Each cloud has its own identity model, and without a central governance layer, organizations struggle to enforce consistent access policies across environments.
The common theme is clear: as systems become more autonomous, distributed, and AI driven, the number of identities and the velocity at which they operate keep increasing. Security teams need a way to keep up.
»How HashiCorp, an IBM Company addresses non-human identity
HashiCorp provides customers with a modern zero-trust security architecture, centered on consistent, identity-based workflows that secure every interaction between workloads, services, and systems. This includes cloud and on-premises environments, human and NHIs, and both static and highly ephemeral systems.
»HashiCorp Vault
Vault provides centralized secrets management with identity-based, policy-enforced credential issuance. It eliminates static credentials by issuing short-lived dynamic secrets with automatic rotation and revocation. This fits naturally with automated delivery pipelines, service-to-service communication, and AI-driven workloads.
»HCP Vault Radar
Vault Radar finds unmanaged or leaked secrets across source code, CI/CD pipelines, and collaboration tools, helping teams close the loop on the most common sources of identity-related risk. Once secrets are found and triaged, Vault Radar can also import these secrets into Vault for full lifecycle control.
»HashiCorp Boundary
Boundary shifts infrastructure access away from networks and toward identity. Instead of distributing SSH keys or relying on VPNs, Boundary grants access to sensitive resources based on identity and policy, then retrieves short-lived credentials from Vault at the moment of connection. This benefits both human operators and automated systems that need governed access to databases, servers, or containers.
»IBM Verify
IBM Verify delivers a unified IAM platform that secures both human and non-human identities across hybrid and multi-cloud environments. When paired with HashiCorp Vault and Boundary, organizations gain end-to-end identity control — from strong user authentication and AI-driven risk detection, to automated secrets management and identity-based infrastructure access. This integrated approach eliminates static credentials, governs workload and service access, and provides a consistent zero trust security model for users, APIs, pipelines, and cloud resources.
»IBM Guardium
Guardium extends this protection to sensitive data. It discovers, classifies, encrypts, and monitors data access patterns, complementing Vault’s identity and secrets management at the workload layer.
Together, Vault, Radar, Boundary, Verify, and Guardium help organizations unify identity security across humans, machines, services, and AI systems.
»Securing the future of identity
NHIs have become foundational to how modern applications operate, and their growth is accelerating with agentic AI, automated pipelines, and multi-cloud architectures. As environments become more dynamic, organizations need identity controls that work consistently across people, services, workloads, and the infrastructure that supports them.
The combined capabilities of HashiCorp and IBM deliver exactly that. With Vault, Boundary, Vault Radar, Verify, and Guardium, organizations gain unified control of secrets, access, identity verification, and data protection, spanning static credentials, ephemeral machine identities, and AI-driven systems.
This protection extends beyond runtime security into the broader infrastructure lifecycle. Terraform and Packer embed identity governance directly into provisioning workflows, ensuring that NHIs created during build, deploy, and operate phases are governed with the same rigor as they are in the runtime security systems. Together, these Infrastructure and Security Lifecycle Management capabilities create a consistent, automation-friendly security layer across the entire ecosystem.
As part of IBM, HashiCorp is expanding this integrated approach even further to support the next era of cloud and AI operations.
If you want to explore the full analysis, you can download the 2025 KuppingerCole Leadership Compass for Non-Human Identities Management here: