Security Lifecycle Management
How are you securing identities, secrets, and access at scale?
Security Lifecycle Management (SLM) is how The Infrastructure Cloud secures the resources that underpin your applications. It unifies secrets management, identity-based access, encryption, and automated policy enforcement into one consistent model that spans all environments. Now security and compliance teams can protect sensitive data, enforce zero trust principles, and reduce risk while developers and operators innovate faster.
Inspect
Gain visibility into secrets, identities, and access to close security gaps.
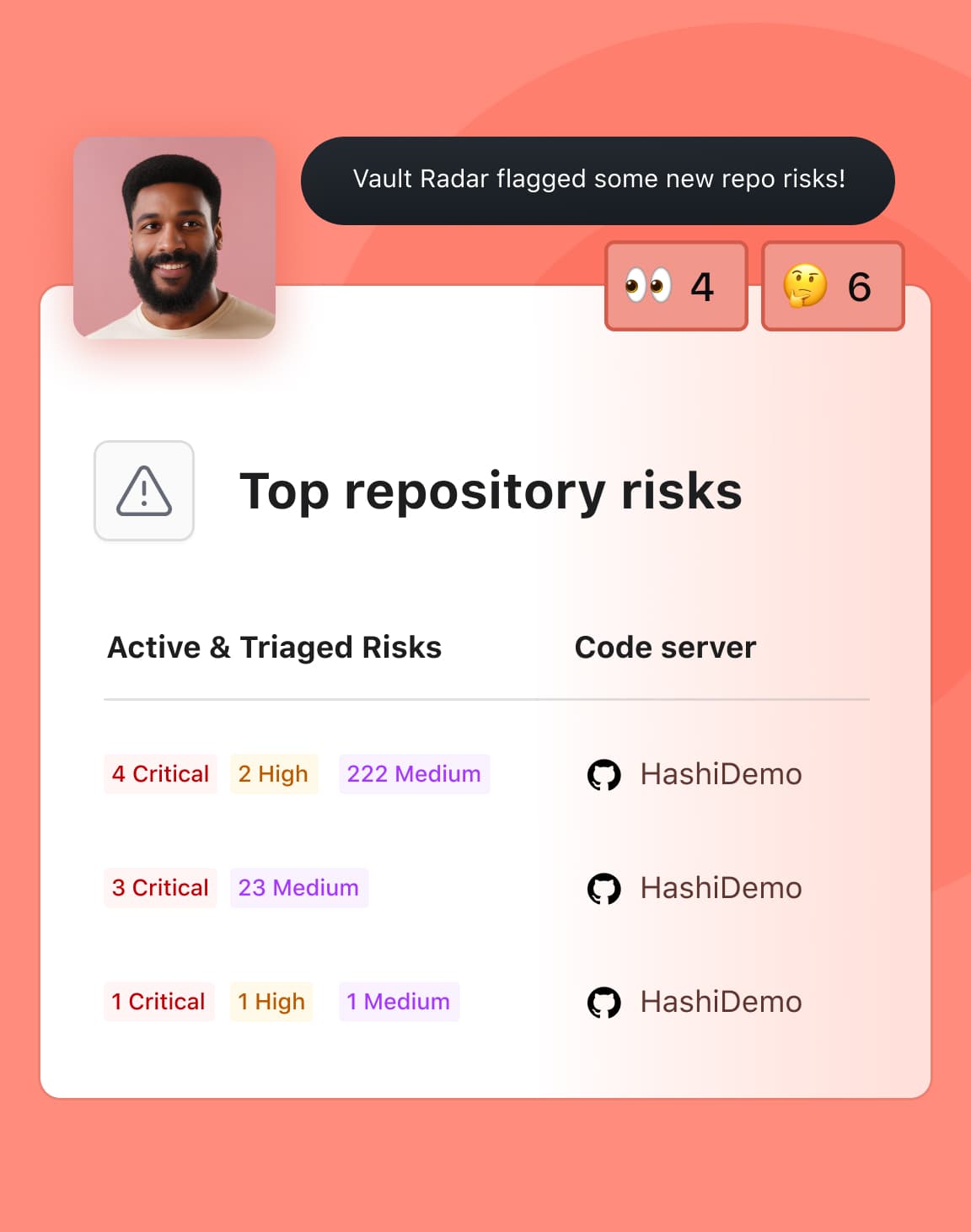
Scan developer repositories to identify exposed secrets and prioritize remediation based on risk
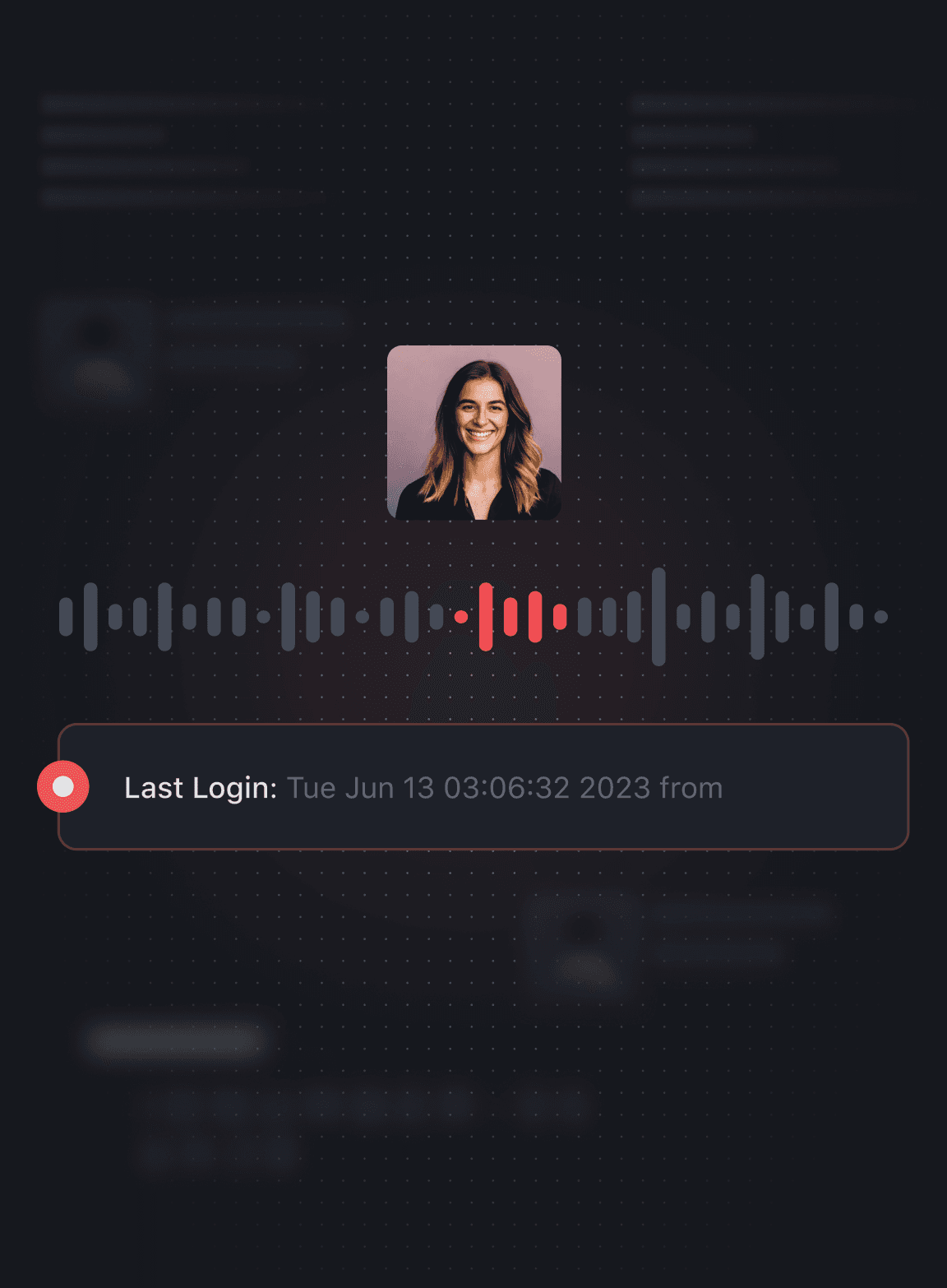
Maintain audit logs for all secrets and privileged system access
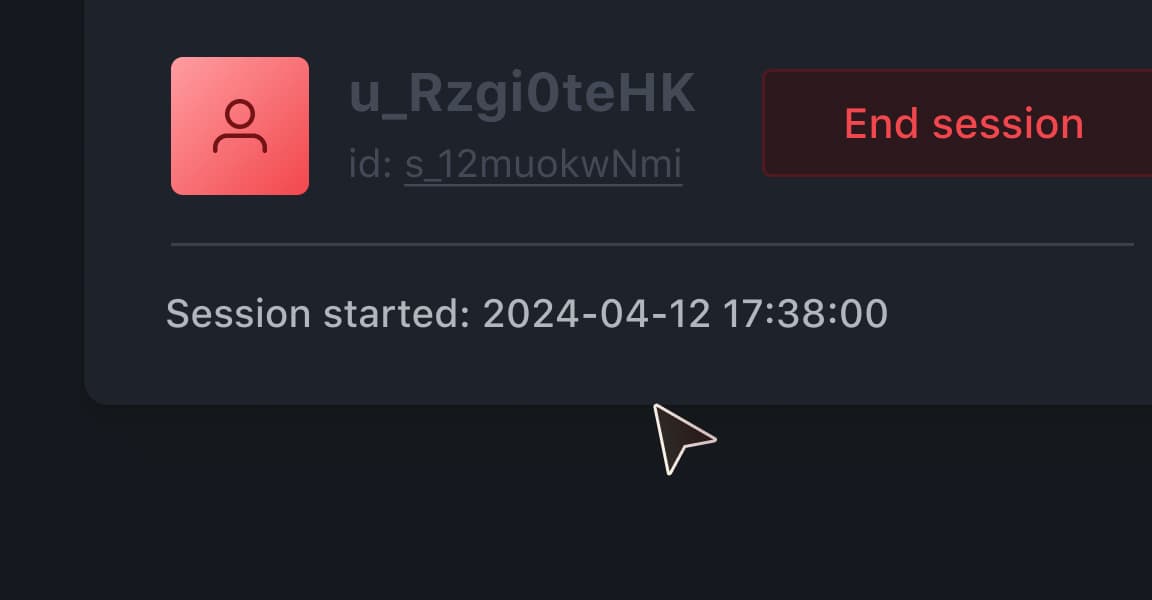
Monitor all privileged access sessions to production environments with the option to terminate as needed
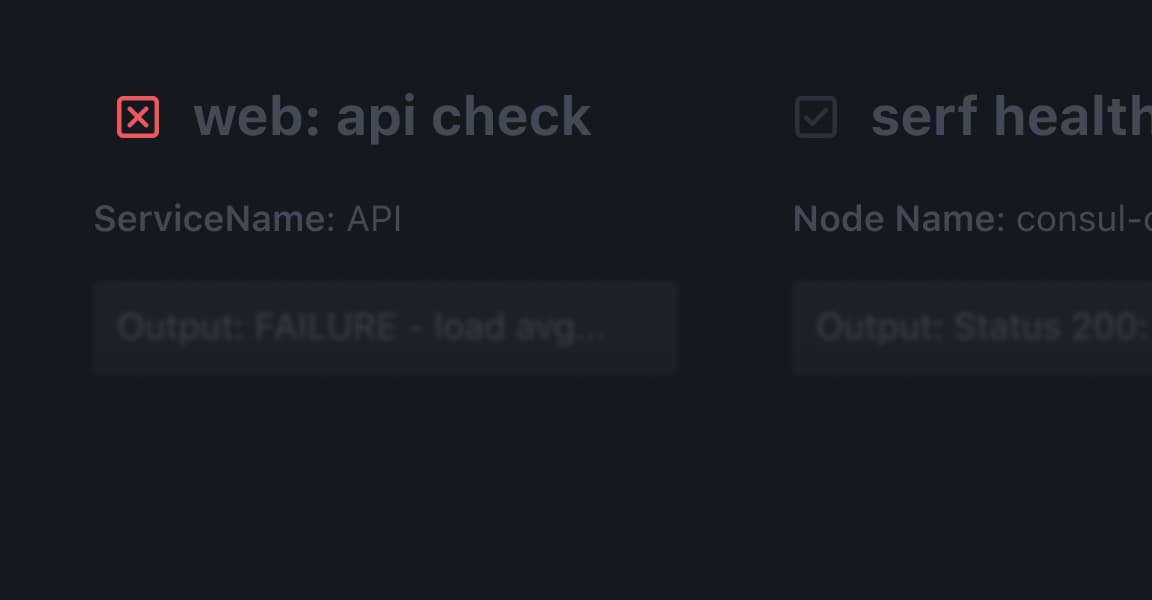
Access a real-time directory of all services and their health status with multi-cloud and multi-platform service registry
Protect
Safeguard identities and credentials with lifecycle management and policy controls.

Securely store secrets, certificates, and keys

Automatically rotate or create just-in-time dynamic credentials for machines and users

Define policies for access levels based on machine, user, and service identity

Record and audit all access points to sensitive applications
Govern
Ensure ongoing compliance and consistent policy enforcement across environments.

Automatically rotate credentials based on policy

Identify drift in security policy and remediate
Revoke access automatically when digital entities are decommissioned
Audit and enforce policies across multi-cloud and hybrid systems at scale
Secure secrets, certificates, keys, and more
HashiCorp Vault helps platform and security teams eliminate secret sprawl by centrally storing, accessing, rotating, and distributing secrets. Once consolidated, these secrets — including tokens, passwords, certificates, and encryption keys — can be tightly managed with consistent policies and automation.
- Identity-based securityUse trusted identities to automate access to secrets, data, and applications.
- Security system of recordCentrally store and protect secrets across clouds and applications.
- Lifecycle managementGain a complete view of your credentials for proper oversight, rotation, and expiry.
Find unmanaged secrets and get them under control
HCP Vault Radar helps platform, DevOps, and security teams tackle the risk of secret exposure by detecting unmanaged and leaked secrets across developer tools, repositories, and collaboration platforms. With automated scanning and prioritized remediation, teams can quickly discover sensitive data, bring it under centralized management, and reduce the risk of breach.
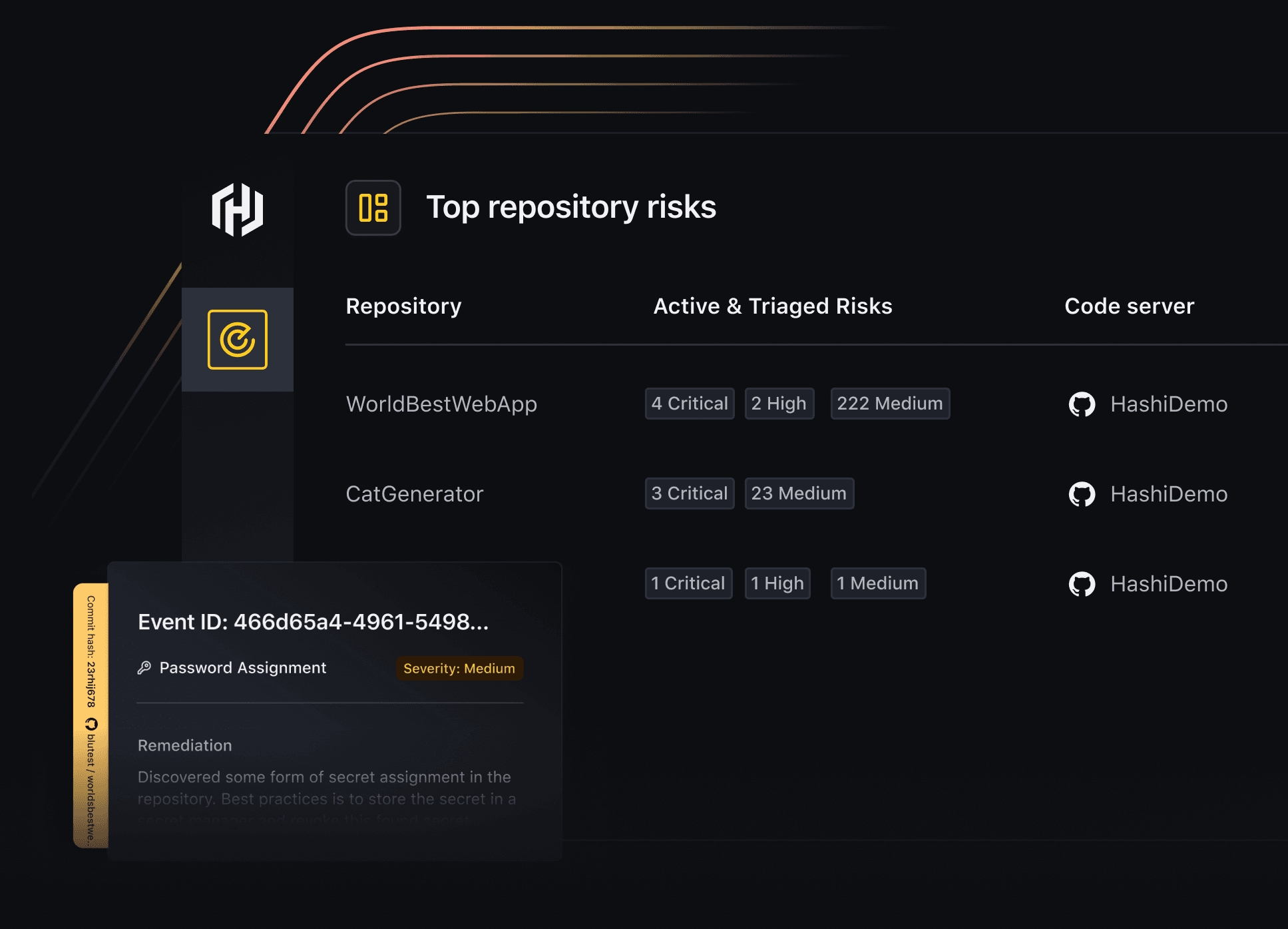
- Discover unmanaged secretsUse 300+ detection algorithms to uncover usernames, passwords, API keys, and tokens in Git repositories, CI/CD pipelines, and collaboration platforms.
- Remediate leaked secretsImport exposed secrets into Vault and follow customized remediation guidance to prioritize and resolve the most critical vulnerabilities.
- Secure sensitive dataOnce discovered, seamlessly migrate sensitive data into Vault for lifecycle management, automated rotation, and secure distribution.
Standardize secure remote access
Built for cloud, modern privileged access management from HashiCorp Boundary uses identity-driven controls to secure user access across dynamic environments.

- Service-based authorizationUse trusted identity to enforce zero trust service access based on user roles.
- Automated workflowsManage access for end users and administrators with passwordless credential injection and automated target discovery.
- Reduce risk exposureReplace long-lived credentials with dynamic secrets and just-in-time credentials using Vault.
Connect services securely with built-in discovery and networking
HashiCorp Consul provides identity-based service networking for service discovery, secure communication, and network automation across multiple cloud and runtime environments.
- Multi-platform service discoveryCreate a source of truth and real-time directory for tracking and routing services.
- Global service mesh and API gatewaySecure service-to-service connectivity and centralize traffic management.
- Networking infrastructure automationReduce misconfigurations and manual ticketing for dynamic IPs.
What happens when you start automating security?
SLM gives teams a central place to standardize security without compromising speed, so sensitive data stays safe wherever it lives.
Accelerate delivery and innovation
Automate security guardrails so teams can move faster with confidence by centralizing secrets and proactively monitoring for exposed credentials and misconfigurations.
A unified operating model for the cloud
Security Lifecycle Management is only half of The Infrastructure Cloud, working hand-in-hand with Infrastructure Lifecycle Management to unify how you manage and secure hybrid cloud environments. ILM provisions and manages infrastructure, while SLM secures, audits, and governs it — all across the application value chain.

Zero trust identity management for the AI era
Download the KuppingerCole report to learn how HashiCorp brings least-privilege, identity-based access and policy controls to non-human identity management across hybrid and multi-cloud environments.