Standardize secure remote access
Connect users and manage access across any environment with identity-based security.
Trusted by leading organizations
Identity-based controls to connect users
Built for cloud, modern privileged access management from HashiCorp Boundary uses identity-driven controls to secure user access across dynamic environments.
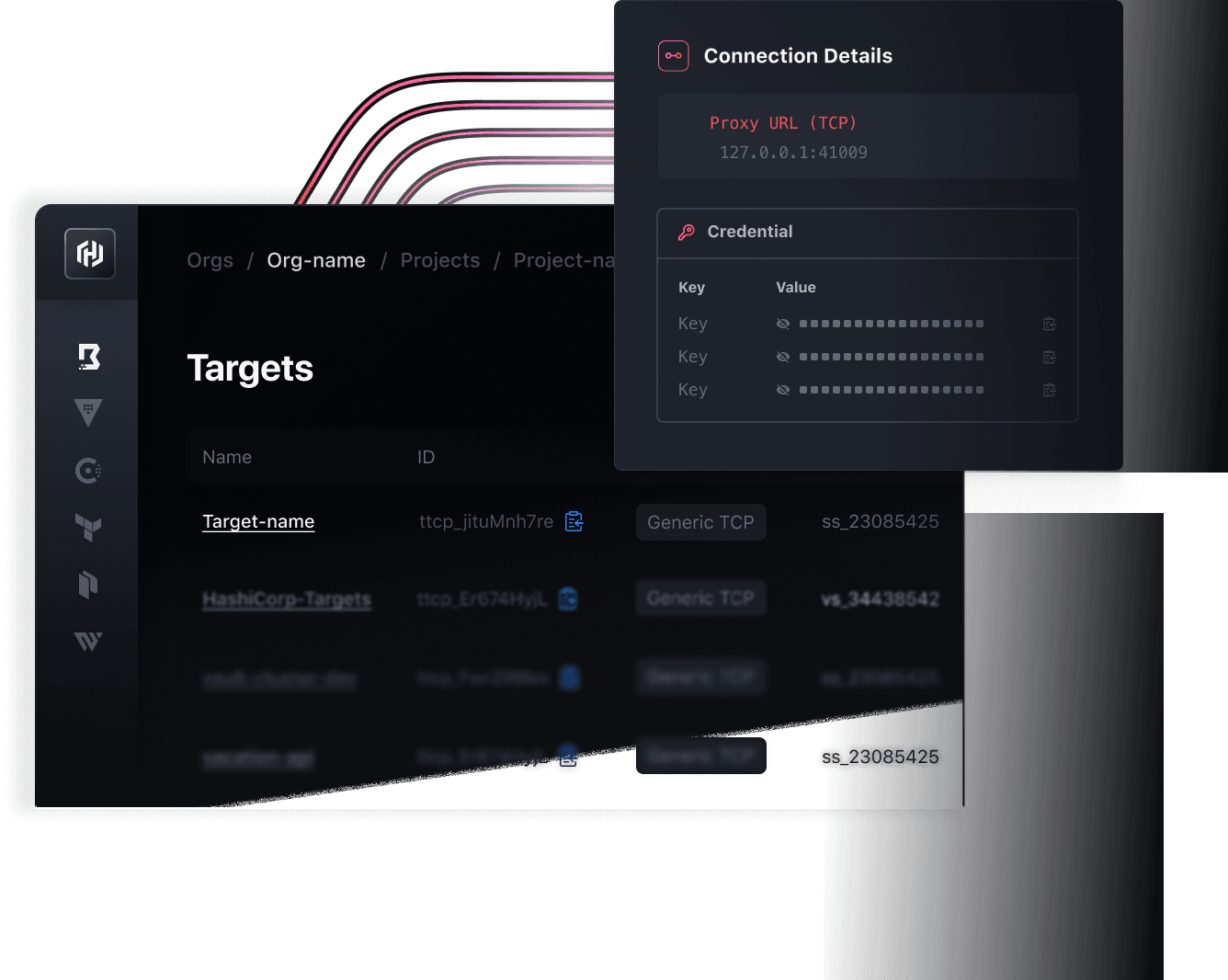
- Authenticate and authorizeUse trusted identity providers for single sign-on access and authorization based on roles and logical services.
- ConnectConnect to dynamic infrastructure like virtual machines, Kubernetes, and databases.
- AccessProvide users with least-privileged access to networks, permissions, and credentials.
Make the secure path, the easy path
Keep secrets safe
Secure access with trusted identities and just-in-time credentials. Use Boundary to inject credentials directly into sessions for passwordless access, so users never see or handle secrets.
Move faster, manage less
No more juggling manual workflows or switching between tools. Help internal teams move faster by automating access to systems and resources, with streamlined onboarding for new or changed infrastructure.
Simplify infrastructure at scale
Say goodbye to bastion hosts and VPNs. Use Boundary to scale infrastructure with dynamic access management across clouds, users, and systems.
From securing the perimeter to authenticating access
With the shift to cloud and hybrid infrastructure, companies no longer manage static IT estates with trusted perimeters. Instead, networks and IP addresses can’t be trusted, and every application and user could pose a threat within the perimeter.
- Identity-based accessAuthenticate every user and authorize access.
- Auto-discoveryAutomatically onboard new services.
- Session managementGive users time-bound, least-privileged access.
- ComplianceEnhance compliance with auditable records and recorded sessions.
Extend Boundary across your IT environment
Integrate trusted identity providers like Okta, Ping, and Microsoft Entra ID to authenticate into Boundary. Use dynamic host catalogs to automatically discover and maintain an updated inventory of resources and services.
Take control of your security estate
Trust no one. Instead, use identity-based controls to inspect, protect, and govern the lifecycle of your secrets, users, machines, services, and data.
Secure remote user access with Boundary
Boundary simplifies secure user access management. Get started for free and let HashiCorp manage Boundary in the cloud. Or explore our self-managed offering to deploy Boundary in your own environment.