Air France-KLM supports passenger travel, cargo, and aircraft maintenance across Air France, KLM, and Transavia. That complexity and scale shows up in its IT department as well:
- Hundreds of product teams
- Multiple cloud providers, along with private infrastructure
- Strict compliance requirements
At HashiConf, the Air France-KLM Group shared how it reworked its infrastructure automation to better match the pace and scale of its business. This was a brownfield cloud migration showing what’s possible after you already have automation in place and start running into limits around scale, cost, and governance. Terraform Enterprise and Vault Enterprise became central to that next phase.
This post breaks down how Air France-KLM rethought security, compliance, and automation using Terraform, Vault, and Ansible so their platform team could scale infrastructure without scaling complexity and ballooning their costs. It also takes a deep look at how they switched from a compliance-by-construction approach to compliance-by-guardrails with policy as code. Finally, you’ll see their automation platform in action with a demo from the talk.
»AirFrance-KLM’s transformation at a glance
Trajce Golomeov, an Automation Technical Architect for Air France–KLM, outlined his company’s transformation succinctly — showcasing a broad range of benefits gained across security, reliability, agility, FinOps, and more:
| Metric | Before | After |
| Provisioning time | Hours to days | Minutes |
| Environment drift | High | Near-zero |
| Security integration | Added later | Embedded by design |
| FinOps | Static, always-on resources with no scaling flexibility | Dynamic scaling and cost optimization |
| Cloud adoption | Ad hoc, inconsistent | Managed, policy-driven |
| Productivity | Time spent on repetitive tasks | Focus on high-value work |
| Quality | Frequent errors, lack of standardization | Reduced errors, standardized processes, lower time to market |
The chart summarizes a hard-earned journey that took a significant amount of time and ingenuity. Reducing provisioning time and support requests was the first big benefit…
»Reducing errors and deploy time through automation
The first benefit everyone receives from a Terraform transformation is speed. Provisioning sometimes took days at AirFrance-KLM, but with Terraform and infrastructure as code, they reduced that down to minutes. Terraform automation also addressed a persistent operational pain point: manual setup errors.
Trajce shared an example:
“I can give you an example. Simply by automating the creation of Terraform workspaces, configuring them with the desired parameters for the product team — including their access tokens — we have reduced errors and support requests by more than 70%. Whether those issues were related to typos, naming conventions, team names, or similar factors, automation just simply took them off the table.”
— Trajce Golomeov, Automation Technical Architect, Air France–KLM
By standardizing workspace creation and configuration, platform teams eliminated an entire class of human error while improving developer experience and velocity.
»Scale without scaling platform cost
Once AirFrance-KLM adopted Terraform Enterprise, it was able to scale quickly:
- From 4,000 to 7,200 Terraform workspaces in one year
- 90+ modules managed in a private Terraform module registry
- Support for 450+ teams using Terraform Enterprise
That scale would not be sustainable without automation and standardized governance. The payoff is measurable, including cost efficiency:
“Terraform’s declarative model, vast ecosystem, and multi-cloud capabilities matched our automation goals, enabling us to deliver infrastructure faster, with higher consistency and lower operational risk. Vault addressed the growing importance of secure, dynamic secrets management in a hybrid environment, helping us stay compliant and build trust in our automation processes. Together, they offered a new automation model — one that reduced engineering bottlenecks, reduced time to market, and allowed us to scale services without scaling costs. … Through infrastructure as code, we avoid tens of thousands of cloud costs per week.”
— Trajce Golomeov, Automation Technical Architect, Air France–KLM
And there’s even more cost savings yet to be realized since not all teams at AirFrance-KLM have adopted Terraform yet.
»From compliance-by-construction to compliance-by-guardrails
One of the most important shifts in Air France-KLM’s automation journey wasn’t just adopting Terraform — it was changing where and how compliance is enforced.
»Compliance-by-construction
Before Terraform, Air France-KLM already operated a mature, secure automation platform built around a large internal service catalog.
The platform offered 350+ pre-approved services.
-
Each service was:
-
Secure by default
-
Compliant by default
-
Designed to meet specific regulatory and organizational requirements
-
Compliance logic was embedded directly into each service.
-
The catalog covered:
-
IaaS and PaaS services
-
Networking and database provisioning
-
Cluster deployment
-
Operational tasks such as DNS, account provisioning, and server management
-
This model gave the organization strong control and reliability; however:
- There were significant downsides:
- 350+ is an eye-watering number of services to maintain
- Every new service or variation required custom engineering
- The catalog became large, complex, and expensive at scale
- Lack of flexibility slowed down product teams that needed a service that didn’t precisely fit the menu of options
- This strategy placed a huge burden on the platform team to create more and more new pre-approved services
»Terraform Enterprise enabled a shift in strategy
As Air France-KLM accelerated its move to cloud native infrastructure and hybrid/multi-cloud operations, the team questioned whether this service-centric model could scale technically and economically.
When adopting Terraform Enterprise, they saw an opportunity to change their approach:
-
A declarative infrastructure as code model
-
Broad multi-cloud support
-
The ability to standardize workflows across Google Cloud, Microsoft Azure, and private SDDC environments
-
A path to reduce engineering bottlenecks without reducing governance
Rather than re-implementing hundreds of tightly scoped services as inflexible, compliant modules in Terraform, the team made a deliberate architectural shift.
»Compliance-by-guardrails
With Terraform Enterprise, Air France-KLM decoupled compliance from individual service definitions and moved it into centralized policy as code guardrails.
-
Former catalog services were transformed into more generic, reusable Terraform modules
-
Compliance logic was:
-
Centralized, and therefore centrally manageable
-
Expressed as policy as code
-
Applied consistently across all Terraform workspaces and modules
-
-
Policy logic guardrails enforce:
-
Naming conventions
-
Required configuration parameters
-
Organizational and regulatory constraints
-
-
Policies are automatically enforced broadly across infrastructure, regardless of cloud provider or module
This approach changed how teams consume infrastructure in three ways:
-
Platform teams no longer need to encode every compliance rule into every service
-
Product teams gain flexibility without bypassing governance
-
Compliance becomes a shared, automated safety net, not a manual gate
“We now offer more generic Terraform modules to developers thanks to the policy as code guardrails and naming conventions. Rules are enforced automatically, allowing developers to use those modules widely and easily without sacrificing compliance or consistency. So teams can use them anywhere, anytime, on any cloud provider, and stay compliant without even thinking about it.”
— Trajce Golomeov, Automation Technical Architect, Air France–KLM
This shift is what made it possible for Air France-KLM to scale Terraform adoption to thousands of workspaces and hundreds of teams — without scaling platform cost or compliance risk.
»A tightly integrated Terraform, Vault, and Ansible workflow
Once Air France-KLM had Terraform Enterprise in place, it had a platform foundation on which it could integrate with Vault Enterprise and Ansible for a single automation workflow spanning infrastructure, security, and post-provisioning configuration.
At a high level:
-
Terraform Enterprise is the core infrastructure as code engine
-
Workflows are triggered either through:
-
GitHub Actions in CI/CD pipelines, or
-
Consumption from an internal service catalog
-
-
Vault provides authentication and short-lived credentials
-
Ansible Automation Platform handles post-provisioning configuration
“Tools like Terraform, Ansible, and Vault aren’t just powerful on their own. Together they create a fully integrated workflow that bridges infrastructure, security, and configuration. With this stack, we can deploy any service — whether it’s a self-managed or cloud native component — across any environment, public or private. It’s secure, reliable, and fast to deploy. But more importantly, it removes friction. There is no more time wasted opening tickets or waiting on other teams for tooling or access.”
— Trajce Golomeov, Automation Technical Architect, Air France–KLM
This workflow supports provisioning across Google Cloud, Microsoft Azure, and a private software-defined datacenter (SDDC) without hard-coded secrets or long-lived credentials (Learn why we need short-lived credentials in infrastructure).
»Demo: A secure automation platform with Terraform, Vault, and Ansible
The second half of AirFrance-KLM's presentation walks through the tightly integrated workflow mentioned above. At a high level, the embedded demo video below covers:
-
Terraform workflows secured with Vault
-
GitHub Actions authenticate to Vault using JWT
-
Vault validates team identity and issues short-lived Terraform tokens
-
Terraform deploys cloud resources without static credentials
-
-
Post-provisioning with Ansible and Vault
-
Machine (technical) accounts replace human or static local accounts
-
Vault issues dynamic credentials with a short TTL (time-to-live)
-
SSH access is secured using Vault’s SSH client signer
-
Passwords are rotated automatically and written back to LDAP
-
-
Application secrets management
-
Dedicated Vault namespaces are allocated per team
-
Terraform automates namespace creation and configuration
-
Applications authenticate using AppRole
-
Human access uses LDAP authentication
-
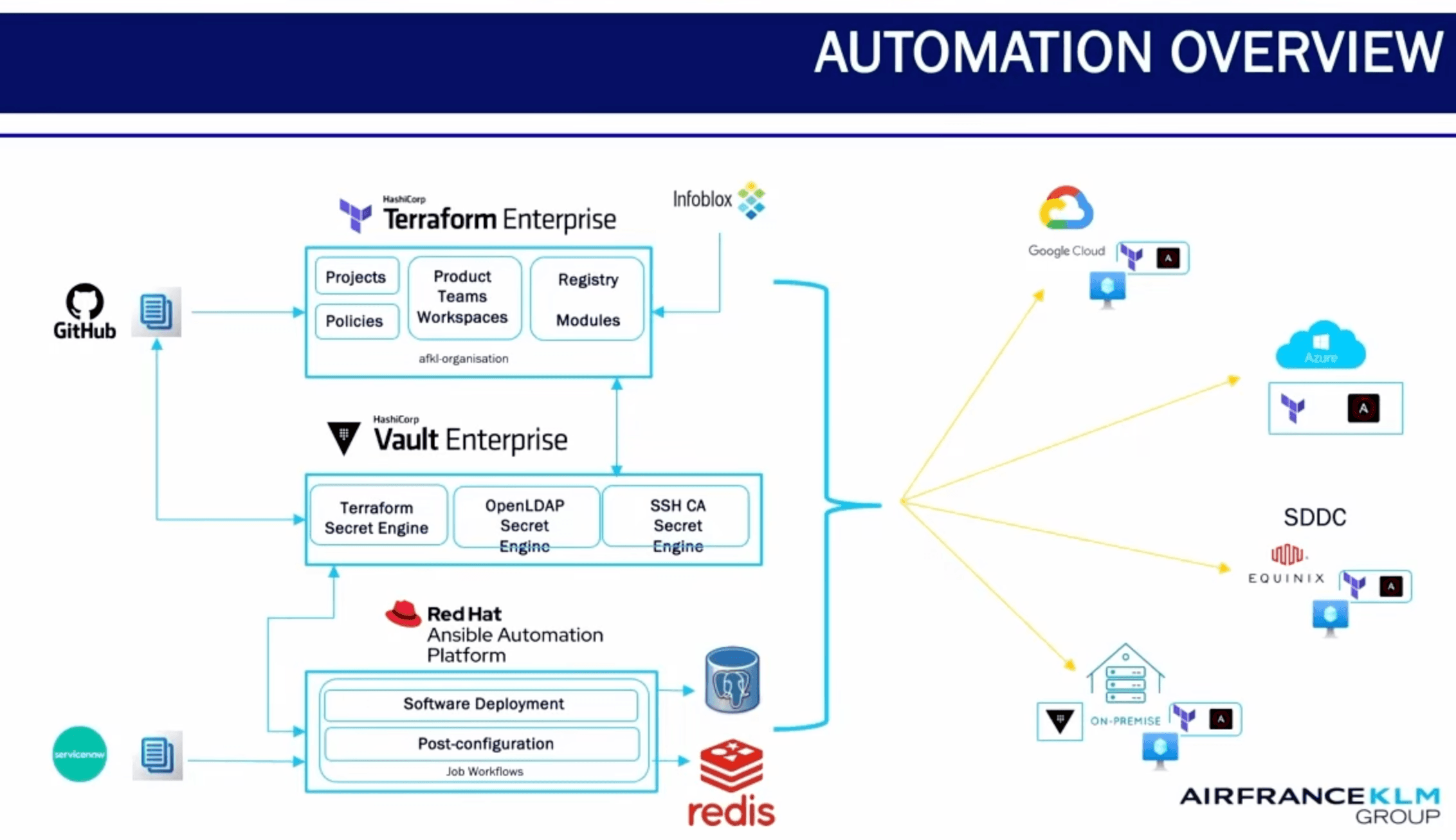
AirFrance-KLM's automation architecture.
The key thing to notice is how security at AirFrance-KLM is embedded directly into the automation flow, rather than layered on afterward.
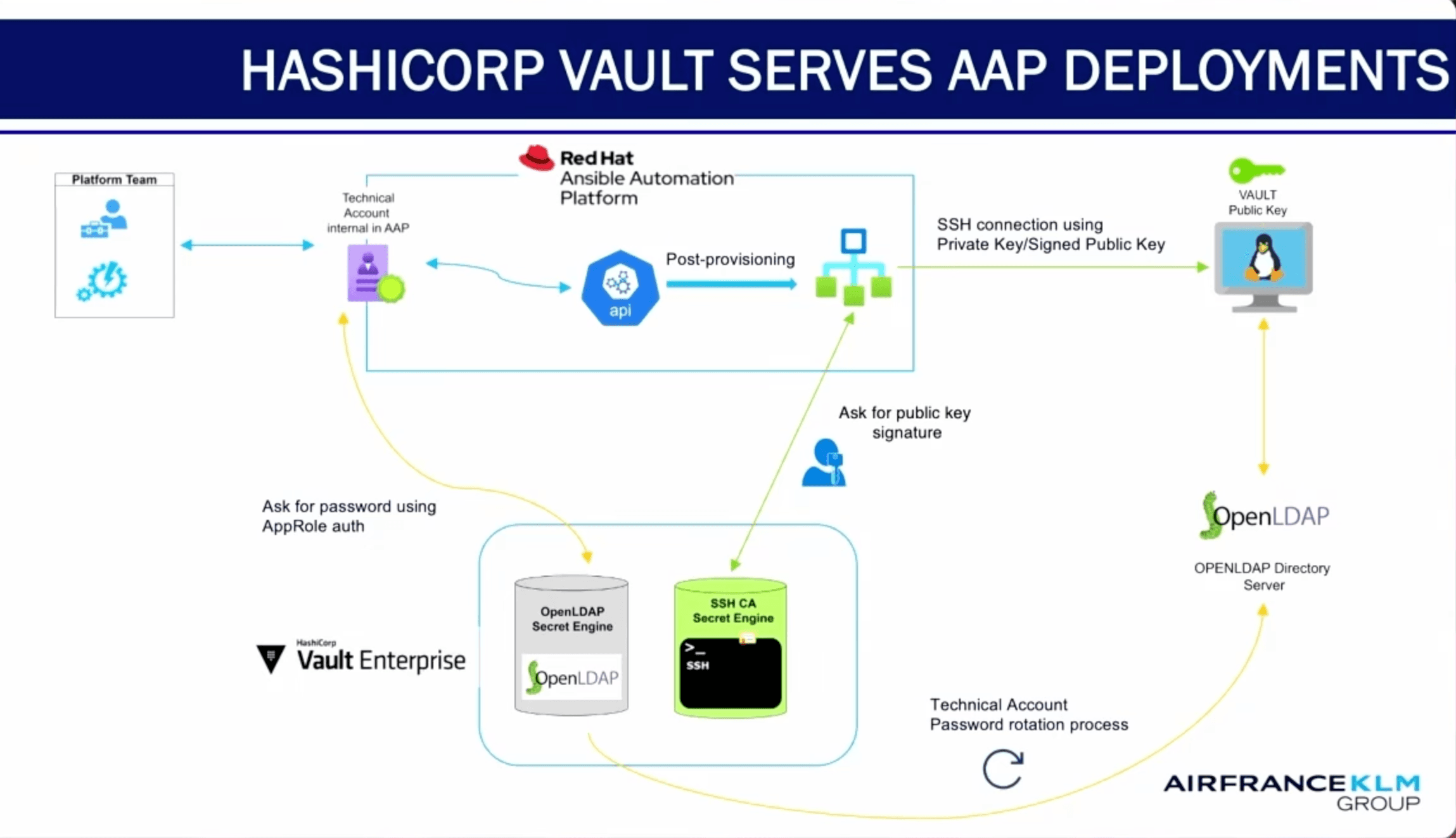
HashiCorp Vault workflow for serving Ansible Automation Platform (AAP) deployments.
Watch the demo starting at this linked timestamp.
»Scale your infrastructure, security, and governance
AirFrance-KLM’s story offers a practical use case for treating automation as a unified platform (not a collection of disjointed tools) that spans provisioning, access, secrets management, post-installation configuration, and ongoing operations. For platform teams dealing with scale, compliance requirements, and growing cloud spend, the lessons here are less about specific products and more about how automation choices compound over time.
This story also proves that speed and security aren't mutually exclusive. With the right infrastructure foundation, you can have both. Learn to adopt the same philosophies that AirFrance-KLM did by reading our guide: Deliver innovation at scale with The Infrastructure Cloud.
Watch AirFrance-KLM’s full session and demo below: