For years, the role of SecOps has been defined by control, by gates, approvals, and hard boundaries. The rise of AI-assisted coding has reshaped the development lifecycle. Speed and automation now define how software is built, often outpacing the reach of traditional controls. AI is now rewriting the rules of software creation, making development faster, but also exposing how fragile traditional controls have become.
To traditional security teams, this looks like unpredictable terrain, with an attack surface that shifts with every new tool and workflow.
The following strategies outline how teams are transforming security from a control mechanism into a driver of speed, confidence, and innovation:
»Strategy 1: Bring security closer to developer workflows
Today, code is generated in seconds, developers building across time zones, and teams sharing snippets across Slack, Confluence and dozens of other digital surfaces. In this environment, exposures don’t just appear in repositories, they surface in conversation threads, code suggestions, and automated pipelines long before they ever reach production.
Traditional models of security scanning at commit can’t keep pace with modern development velocity. To truly protect sensitive data, security scanning, especially secret scanning, needs to start earlier in the development lifecycle and closer to the developer’s daily workflow.
This evolution isn’t just about running scans sooner, it’s about creating fast feedback loops that catch issues as they emerge and guide developers in real time. When checks happen in the IDE or pre-commit hooks, developers can detect and remediate exposed secrets the moment they’re introduced, without waiting for a CI/CD gate or security review. This highly integrated workflow automation identifies and resolves exposures continuously, turning security into a natural part of development rather than an external audit.
When visibility lives inside the tools developers already use, security shifts from reactive review to continuous, proactive assurance. Every workflow becomes an opportunity to surface risks in context and correct them immediately, reducing exposure without slowing delivery. The result is adaptive guardrails that provide context and strengthen security where it actually gets built.
»Strategy 2: Replace enforcement with enablement
The difference between friction and acceleration often comes down to when and how security appears in the development process. Two simple scenarios show how timing and context can redefine a developer’s entire experience with security.
Scenario 1: When a developer commits code containing what appears to be a hard-coded secret, the CI/CD pipeline immediately identifies that a security violation has been detected, which pauses development work. Frustration builds as engineers troubleshoot and determine the next step. Security, once again, becomes the blocker in the delivery chain.
Scenario 2: When the same issue is identified earlier, directly within the IDE, a prompt alerts the developer that a potential secret has been detected. The developer is guided to remediate the issue and then continue working without interruption.
These two outcomes represent more than a workflow difference, they reveal a shift in philosophy. The first model treats security as an external gate, enforcing compliance after coding is finished. The second treats it as an integrated design principle, guiding coding decisions as they happen.
When security works in real time alongside development, it transforms from oversight to enablement. The organizations that thrive will be those that design systems where the secure path is also the fastest and easiest to follow.
»Strategy 3: Design for continuous visibility and learning
The most successful organizations are building three complementary layers of defense and empowerment:
Guidance at the point of work. IDE-level feedback, contextual documentation, and actionable suggestions that teach without interrupting.
Visibility across the ecosystem. Continuous monitoring that validates exposures, assesses risk, and delivers actionable insights, without slowing down productivity.
Centralized secrets management: A unified vault that secures, manages, and rotates secrets across environments, ensuring every credential, token, and API key remains protected from creation to deployment.
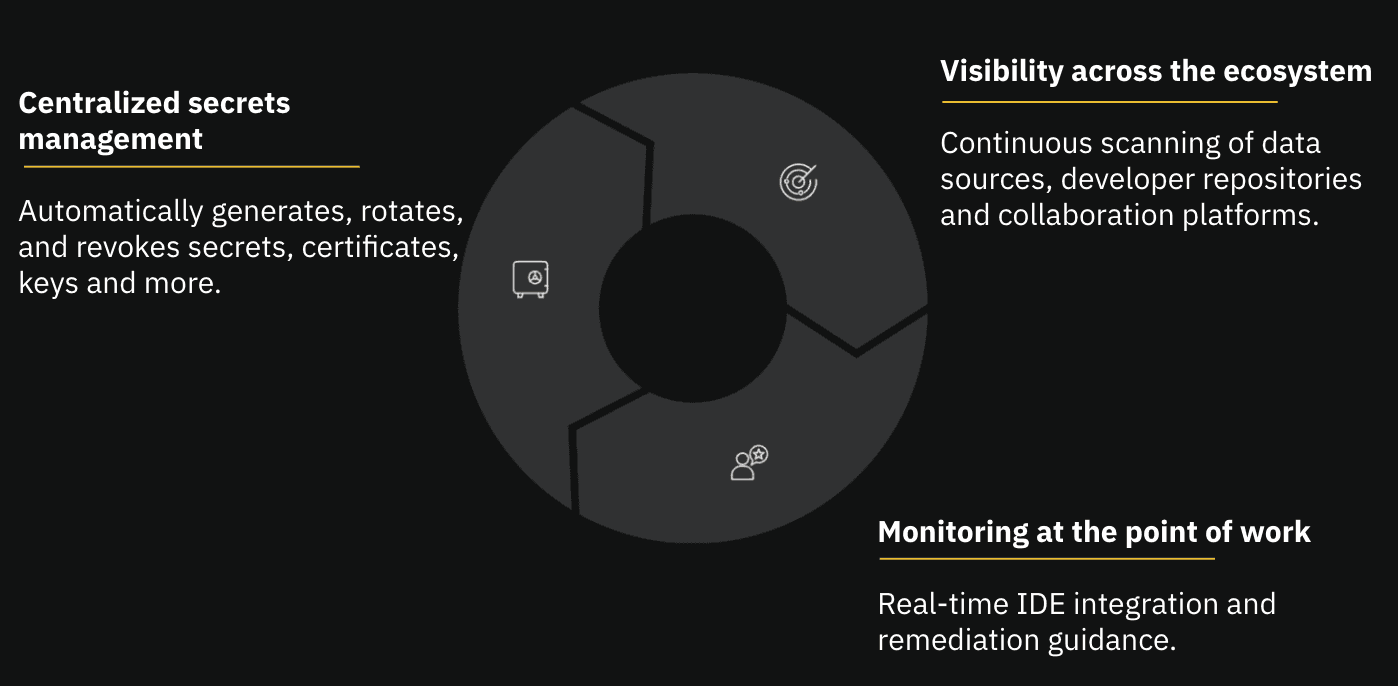
Together, these layers form a secrets management system that scales with development velocity rather than against it. By connecting real-time developer guidance with continuous monitoring and centralized management, SecOps can accelerate secure-by-default behavior across teams. This empowers Developers to stay productive, and security teams to gain the visibility, context, and trust they’ve long been missing.
»Building a security strategy that moves at the speed of development
Security is strongest when it moves with development, not after it. Early feedback is less expensive and less disruptive.
As AI and automation continue to accelerate development, security must evolve with equal speed and proximity. When real-time guidance and continuous visibility become part of the creative process itself, prevention happens naturally. It builds a partnership with SecOps and a foundation for faster, safer, and more resilient software delivery.
Start your free HCP Vault Radar trial and set up the HCP Vault Radar VS Code extension to bring security into your developer workflows.
Interested in learning more about Vault Radar? Check out our webinar series.
What’s the business case for Vault Radar? Read our eBook: The cost of secret sprawl: And how to stop it.







