Organizations running workloads in AWS often need a secure, reliable way to manage secrets and encryption keys. At the same time, teams want to minimize operational overhead, avoid public endpoints, and reduce the complexity of multi-account or multi-region networking.
With HCP Vault Dedicated and AWS PrivateLink, customers can now combine a fully managed Vault service with private network connectivity. This makes it easier for applications to securely access secrets without the risks and operational burden of managing infrastructure or exposing sensitive traffic to the public internet.
»HCP Vault + AWS PrivateLink integration benefits
Organizations increasingly need secure, reliable access to secrets and encryption keys. But building and operating Vault clusters yourself, or maintaining complicated multi-account networking, adds significant operational burden, cost, and risk.
HCP Vault Dedicated removes this burden by delivering Vault as a fully managed service. HashiCorp handles cluster provisioning, patching, scaling, updates, monitoring, and high availability.
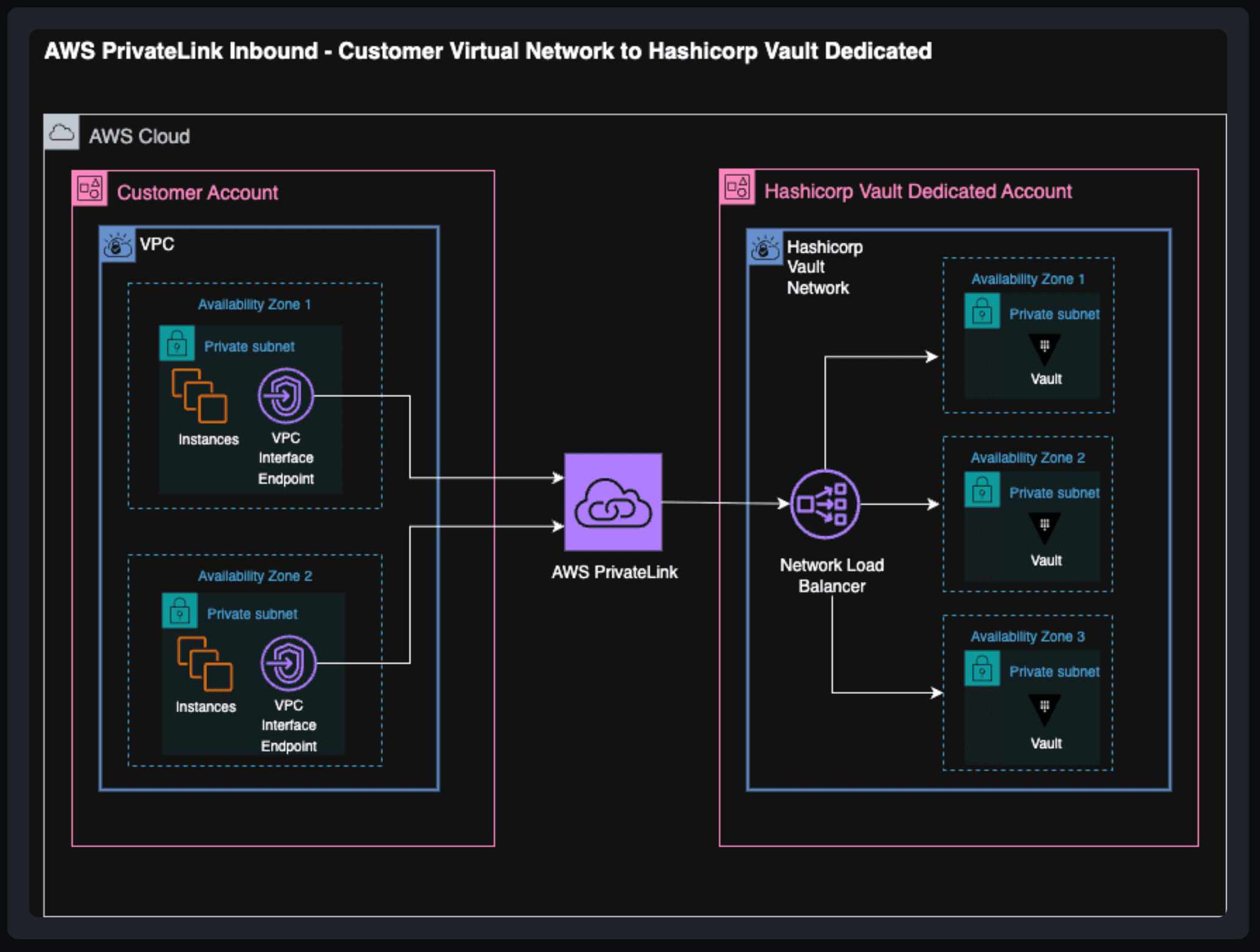
With the addition of AWS PrivateLink, customers now gain private, internal network access to their managed Vault clusters, without public endpoints or operating any Vault infrastructure themselves.
This combination results in:
- Higher security through fully private connectivity
- Less operational overhead - Vault infrastructure is managed for you
- Simplified networking without peering or overlapping CIDR (Classless Inter-Domain Routing) issues
- Faster onboarding for apps and teams
- A clean security posture aligned to regulated environments
Before AWS PrivateLink, connecting workloads across AWS accounts or regions to a central Vault cluster often required peering, transit gateways, and careful routing management — each potentially adding complexity and time to deploy.
AWS PrivateLink simplifies this process and, by extension, simplifies multi-account and multi-region workloads. With AWS PrivateLink, customers can:
- Use a simple interface VPC endpoint to connect privately to Vault
- Avoid VPC peering and transit gateway setup
- Avoid CIDR overlap issues entirely
- Connect from multiple accounts, VPCs, or regions
- Keep all Vault traffic on AWS’s private backbone
This gives organizations more options to ensure traffic between your AWS VPCs and HCP Vault remains private. It also helps teams align with best practices for scalable, multi-account landing zones or regionalized application architectures.
»A Terraform workflow with HCP Vault and AWS PrivateLink
Many organizations rely on Terraform to automate provisioning of their network (e.g. VPCs), secrets, compute (e.g. Kubernetes clusters), and databases. Those workloads need secure, reliable access to secrets from day one.
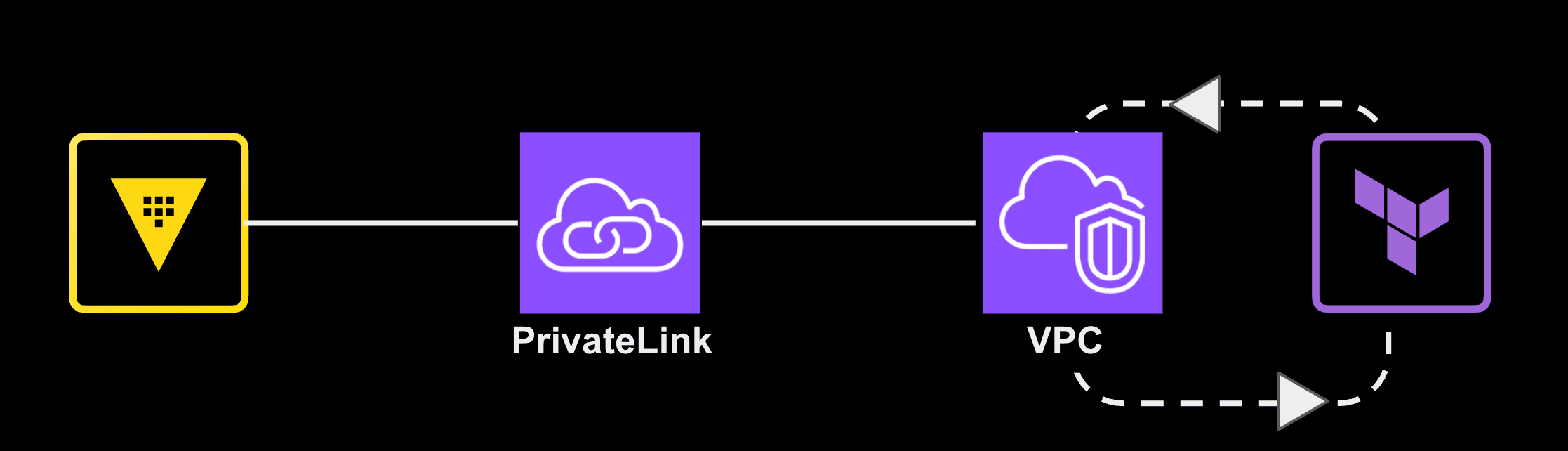
With AWS PrivateLink in place, infrastructure created by Terraform inside a customer’s VPC can automatically and securely authenticate to Vault using AWS’s private backbone, without public endpoints or custom routing.
This creates a streamlined workflow:
- Terraform provisions AWS infrastructure (VPCs, subnets, compute, EKS clusters).
- Terraform establishes application identities (IAM roles, IRSA, service accounts).
- Applications use those identities to authenticate to Vault through AWS PrivateLink.
- Vault, fully managed by HashiCorp, handles secrets, tokens, and encryption keys.
No public access. No NAT gateways. No VPNs. No Vault servers to operate. Just secure, automated access from Terraform-provisioned apps to a private Vault endpoint.
This integrated pattern helps platform teams standardize security across AWS accounts and regions while reducing operational overhead.
»Secure identity workflows for Terraform-provisioned apps
Here’s a more detailed outline of the streamlined workflow that was summarized in the previous section, along with the benefits of each step:
1. Terraform creates IAM roles or IRSA mappings for your applications.
- Each application gets a unique, auditable identity.
- This eliminates shared credentials and reduces the risk of secrets sprawl.
2. Applications inherit their AWS identity automatically.
- No manual configuration is needed to assign permissions or inject credentials.
- Identity is tied to the application environment itself, improving traceability and compliance.
3. Applications authenticate privately via AWS PrivateLink.
- All Vault traffic stays on AWS’s private network, with no exposure to the public internet.
- Reduces attack surface and simplifies networking because there’s no need for VPNs, NAT gateways, or potentially complex peering configurations.
4. Vault issues short-lived, scoped secrets and tokens.
- Applications only get the credentials they need, for the duration they need them.
- This minimizes the blast radius in case of compromise and ensures policies are automatically enforced.
This architecture is easy to scale, ideal for multi-account organizations, and aligned to enterprises that need strong security controls with minimal overhead.
Overall: End-to-end automation from infrastructure to secrets.
- Terraform provisions infrastructure and identities.
- PrivateLink ensures secure connectivity.
- Vault handles secrets issuance and lifecycle.
- Developers and DevOps teams don’t need to manually configure or rotate credentials.
Key advantages of this approach include:
- Stronger security posture: Secrets never traverse the public internet, identities are auditable, and short-lived credentials reduce risk.
- Operational simplicity: Platform teams don’t need to manage Vault servers, configure networking manually, or rotate long-lived secrets.
- Consistency across environments: Terraform ensures reproducible, policy-compliant infrastructure and identity setup across accounts and regions.
- Developer productivity: Developers can access secrets programmatically without managing credentials or waiting for manual approvals.
- Compliance-ready: Private connectivity and identity-based access make it easier to meet regulatory or internal security standards.
By linking infrastructure provisioning, identity management, private authentication, and secrets delivery, this approach creates a secure, automated, and scalable best-practice workflow for cloud-native applications.
»Getting started
As organizations continue scaling their AWS workloads, integrating HCP Vault Dedicated with AWS PrivateLink offers a straightforward, secure, and fully managed path to delivering secrets privately to any application, in any account or region. If you’re ready to deepen your understanding or start implementing this pattern, explore our detailed architectural guidance on cross-region and multi-account connectivity. To begin setting up PrivateLink with your own HCP Vault environment, follow the step-by-step configuration guide in the HCP documentation.








