Many Terraform users still rely on static credentials (API keys, passwords, certificates, etc.) to authenticate workloads with cloud providers (AWS, Google Cloud, Azure). However, relying on this practice poses both operational and security challenges. Managing static, long-lived credentials does not scale well without tedious and time-consuming manual intervention. Additionally, users set credentials as workspace variables or variable sets in Terraform, adding additional complexity to their authentication process.
This practice of manually securing static secrets only increases the likelihood of secrets leakage and secrets sprawl, in which credentials end up scattered across multiple databases, clouds, and applications.
HashiCorp Vault provides a secure and centralized repository for storing these secrets, eliminating the need to hardcode them within Terraform configurations. Vault also provides management and control over identity access management (IAM) policies that applications need to work with other applications and services. Using an API-first approach to authenticate all requests, Vault provides secure access only to authorized resources.
One of the key features that Vault offers HCP Terraform users is Vault-backed dynamic credentials. This feature provides a workflow to auto-generate and revoke secrets/credentials when they are no longer needed.
This blog will explain why securing your infrastructure with dynamic secrets through Vault-backed dynamic credentials is the most secure way to use Terraform and why it should be the new standard for your security roadmap.
»What are Vault-backed dynamic credentials?
Vault-backed dynamic credentials are temporary, time-bound, and unique to each Terraform workload. When you adopt HashiCorp Vault as your secrets manager, Vault’s secrets engines can connect with HCP Terraform and Terraform Enterprise’s dynamic provider credentials feature to generate and manage dynamic credentials directly from Vault.
The dynamic provider credentials feature automatically generates the API keys you need to access and build infrastructure for AWS, Microsoft Azure, and Google Cloud. It does this just-in-time with each provisioning run for one-time use. These dynamic credentials do not require manual rotation or revocation when they are no longer needed.
By making credentials unique and used for one run only, teams drastically reduce the chance that they might be found by attackers, and eliminate the chance of long-term malicious access.
»Standards-based
Drilling down into the security details of this feature, Vault-backed dynamic credentials strongly protect access workflows during infrastructure provisioning by leveraging workload identity and the OpenID Connect (OIDC) standard. Before provisioning, operators must first configure Terraform as a trusted identity provider with Vault (or their cloud infrastructure providers in the case of basic dynamic provider credentials). HCP Terraform or Terraform Enterprise then generate a signed identity token for every workload to obtain single-run credentials that are injected into the run environment. This exchange happens automatically for the supported providers by adding a few simple environment variables to the workspace.
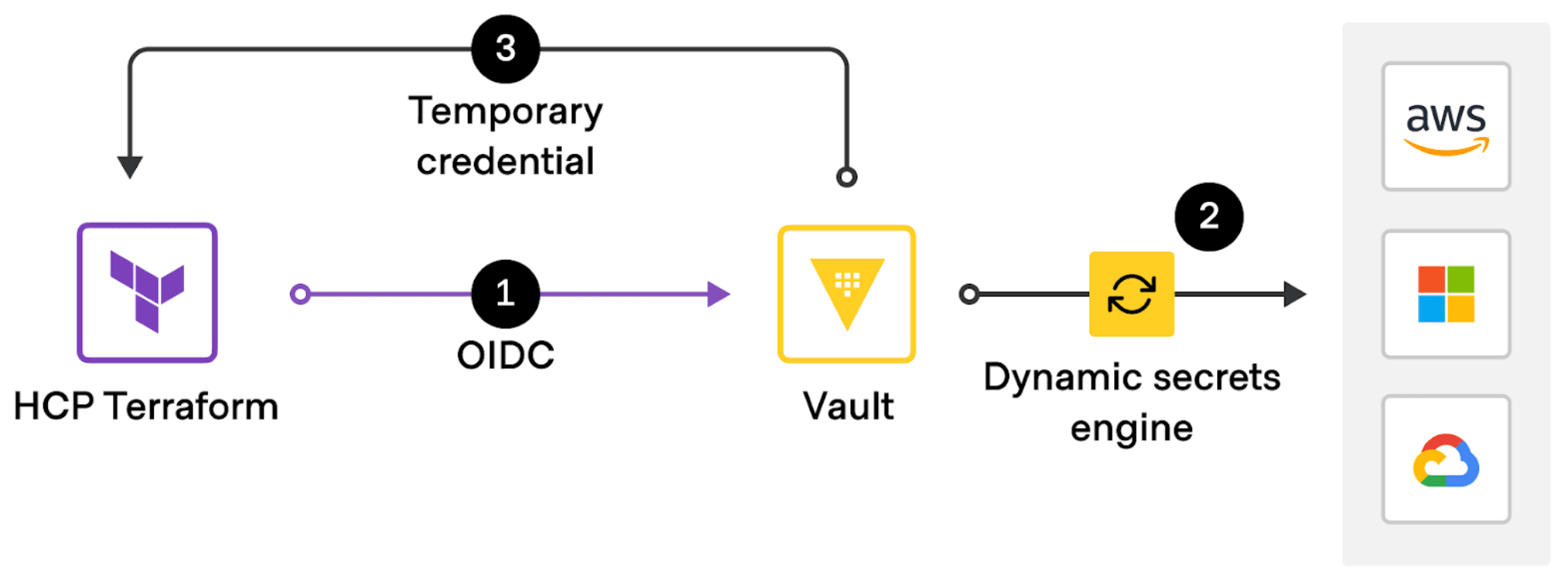
Vault-backed dynamic credentials authenticates to Vault with OIDC, then uses Vault secrets engines to generate cloud credentials for HCP Terraform runs.
»Why use Vault-backed dynamic credentials?
Vault-backed dynamic credentials include several advantages over using only dynamic provider credentials without Vault:
- Consolidated management and auditing for all your cloud credentials and other secrets
- No OIDC setup required in your cloud provider
- Leverage Vault secrets engine configurations
- No need to expose inbound access to self-hosted Terraform Enterprise instances from cloud providers to validate OIDC metadata.
»Consolidated management and auditing
Without being “Vault-backed”, dynamic provider credentials are still a step in the right direction to make your secrets management dynamic rather than static. But there isn’t as much auditing or management capability without the Vault integration. Secrets management is firmly in the purview of Vault, while Terraform is focused on provisioning. By using Vault-backed dynamic credentials instead of dynamic provider credentials without Vault, teams are able to logically consolidate Terraform credential management with all of the other secrets managed throughout the organization on one platform.
Unlike static credentials, dynamic credentials are most effectively utilized within a secrets management platform, such as HCP Vault Dedicated, that automates their lifecycle. HCP Vault Dedicated can automatically generate temporary secrets as required and integrate dynamic secrets into infrastructure automation tools such as HCP Terraform.
»No OIDC setup required in cloud provider
By setting up an OIDC flow from HCP Terraform to Vault instead of a cloud provider, teams can own the full security lifecycle process from authentication to secret generation. This lets teams use the more sophisticated feature set of Vault when managing dynamic provider credentials and reduce the surface area of security configurations required for all workloads.
»Leverage Vault secrets engine configurations
Vault-backed dynamic credentials leverage Vault’s authentication and authorization capabilities to limit permissions based on metadata like the execution phase, workspace, or organization involved in the operation. Security teams already well-versed in configuring Vault policies and mapping workloads to cloud roles can use their existing workflows to authorize Terraform runs, saving time and effort.
Another security benefit of Vault-backed dynamic credentials is the Vault token, which is revoked immediately after the plan or application runs. This means the cloud credentials are also immediately invalidated and cannot be re-used, as opposed to waiting for a fixed time-to-live to expire.
»Protected inbound access
The OIDC workflow requires two-way communication so that the identity provider can validate the signature and metadata of the workload identity token presented by the client. For self-hosted Terraform Enterprise customers using standard dynamic provider credentials to authenticate directly to a cloud provider, inbound network access must be allowed from the provider. Since the cloud providers don’t document the specific IP addresses used for OIDC integrations, this effectively means exposing Terraform Enterprise to the public internet.
Instead, with Vault-backed dynamic credentials, only the Vault instance needs to directly access the metadata endpoints. Vault’s secret engines then use outbound-only connections to the cloud provider.
»How do I start using Vault-backed dynamic credentials?
If you’re new to Vault, start here to try it out and see benefits quickly. If you’re already familiar with Vault, and have it set up in your organization, start by reading the Vault-backed dynamic provider credentials documentation to learn how to set up the feature. Then continue with a hands-on tutorial: Authenticate providers with Vault-backed dynamic credentials.
If you’re having trouble setting up Vault, or you just don’t have the time to self-manage and maintain an on-premises instance, let us manage it for you by signing up for a free HCP Vault Dedicated trial. Either of these two services are the easiest and fastest way to get started with Vault. You can also link your HCP Terraform and HashiCorp Cloud Platform (HCP) accounts together for a seamless sign-in experience.








