We are pleased to announce the release of HashiCorp Boundary 0.6 and the release of Boundary Desktop 1.3. Boundary provides identity-based secure remote access for dynamic infrastructure. Boundary 0.6 includes several key features and improvements that are new since August’s Boundary 0.5 release:
- Boundary Desktop for Linux: Boundary Desktop gives users the ability to connect to remote targets and view active session details. Boundary Desktop 1.3 adds support for Debian-based Linux distributions in addition to existing macOS and Windows support.
- Permissions-based UI: Boundary 0.6 dynamically tailors the UI to individual users’ permissions, ensuring users are presented only with actions and workflows that can succeed.
- Managed group configurations via Terraform: Managed groups, which allow Boundary group memberships to be managed based on permission claims maintained by an external identity provider (IdP), can now be configured via Boundary’s Terraform provider.
»Boundary Desktop for Linux
Boundary 0.6 includes a new release of its desktop client, Boundary Desktop 1.3, which now has initial support for Debian-based Linux distributions such as Ubuntu. This version offers feature parity with our existing macOS and Windows desktop clients and gives our Linux users the same ease-of-use for starting, stopping, and observing sessions from one easy graphical interface.
Boundary Desktop 1.3 for Linux
To download the new Boundary Desktop client for Linux, navigate to our releases page to download our Linux-specific installation. Documentation for installing on Linux has also been added to our documentation site.
»Permissions-Based Admin UI
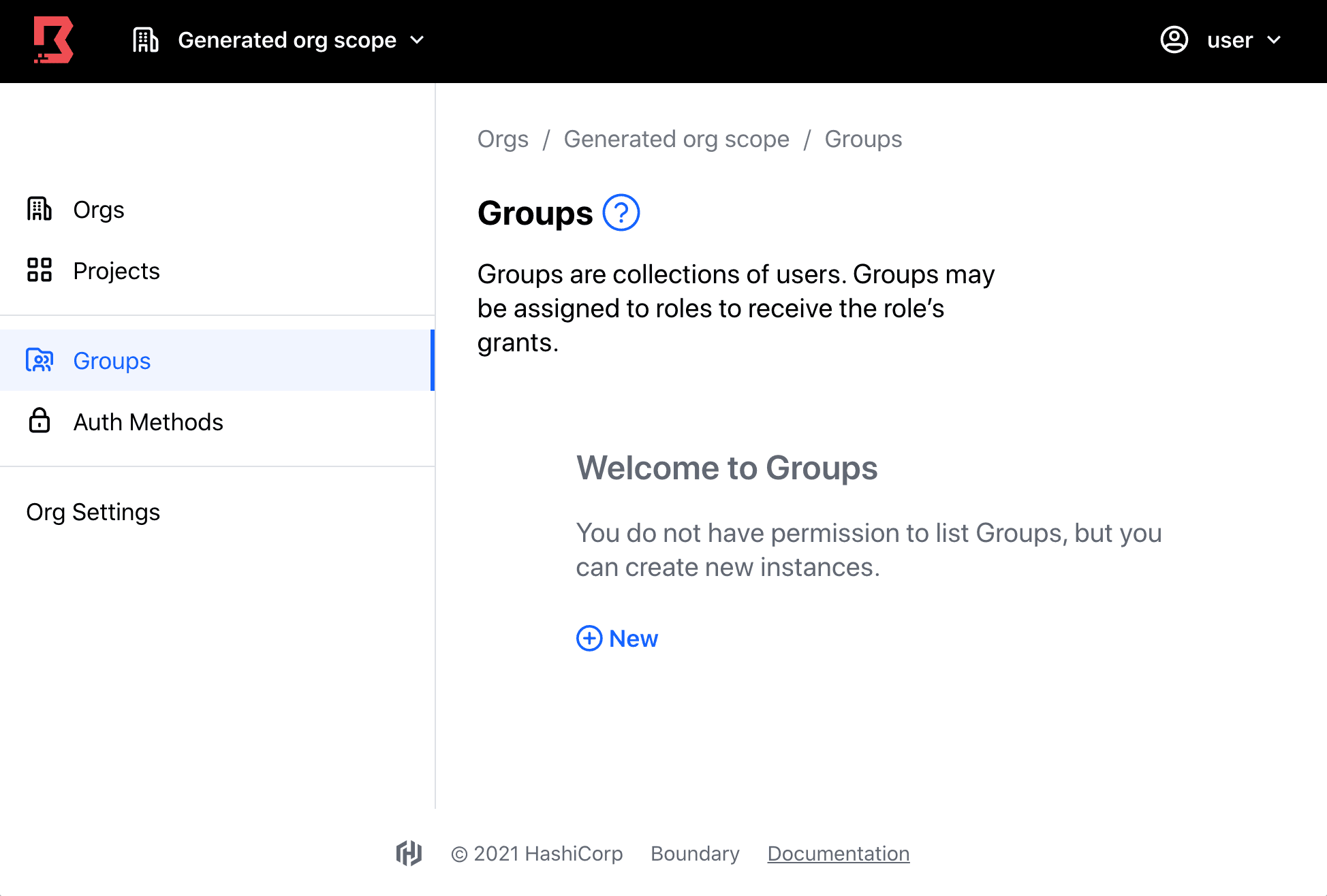
Message for restricted user permissions in the user interface
Boundary 0.6 introduces significant enhancements and security controls to Boundary’s admin console. With these improvements, administrators can now manage their users’ abilities to view and interact with UI elements based on the permission grants the user receives. For each user, this leads to automated toggling of UI features based on the user’s received permissions. This is a significant security and user experience improvement for Boundary users and administrators alike.
»Managed OIDC Groups via Terraform
Managed groups were released in Boundary 0.3 to automate the population of Boundary groups based on permission claims maintained by an external IdP, such as Okta, Azure Active Directory, and others. This allows powerful syncing of IAM permissions between an external IdP and Boundary. Since Boundary 0.5.1, the team delivered Terraform support for managed groups, which is now available in the Boundary Terraform Provider version 1.0.4.

You can try out Boundary’s managed groups capabilities on our HashiCorp Learn tutorial here, or check out the example below:
resource "boundary_auth_method_oidc" "example" {
name = "example"
description = "An example OIDC auth method using boundary's built-in OIDC test server"
scope_id = boundary_scope.my_org.id
issuer = "http://localhost:9200"
client_id = "foo_id"
client_secret = "foo_secret"
max_age = 10
api_url_prefix = "http://localhost:9200"
idp_ca_certs = [
<<EOT
Omitted for brevity
EOT
]
allowed_audiences = ["foo_aud"]
signing_algorithms = ["ES256"]
account_claim_maps = ["oid=sub"]
claims_scopes = ["profile"]
}
resource "boundary_managed_group" "example" {
name = "example"
description = "An example of an OIDC managed group"
auth_method_id = boundary_auth_method_oidc.example.id
filter = "name == \"foo\""
}
»Upgrade Details
Boundary 0.6 introduces significant new functionality. Please review Boundary’s general upgrade guide and release notes for details.
As always, we recommend upgrading and testing this release in an isolated environment. If you experience any issues, please report them on the Boundary GitHub issue tracker or post to the Boundary discussion forum. As a reminder, if you believe you have found a security issue in Boundary, please responsibly disclose it by emailing security@hashicorp.com — do not use the public issue tracker. Our security policy and our PGP key can be found on the HashiCorp security page.
We hope you enjoy Boundary 0.6!








