We are excited to announce the release of HashiCorp Vault 0.11! Vault is a security tool for secrets management, data encryption, and identity-based access among other features.
The 0.11 release of Vault delivers new features to streamline the management of tokens for applications and users attempting to access Vault, provide secure multi tenancy for multiple teams and organizations using a single Vault installation, and other features focused on enhancing system performance and automation.
New features in 0.11 include:
- Namespaces (Enterprise): Provide Secure Multi-tenancy within Vault via isolated, self-managed environments.
- Performance Standby Nodes (Enterprise): Multiply read performance for Vault Enterprise infrastructure via a new type of performance-focused standby node.
- Vault Agent: Automatically manage the secure introduction and renewal of tokens for local applications.
- ACL Templates: Support templating for identity groups, entities, and metadata within ACL policies.
- Alibaba Cloud Support: Support Alibaba Cloud identity systems and provide dynamic credential creation for Alibaba Cloud infrastructures via Vault.
- Microsoft Azure Secrets Engine: Generate dynamic credential access to Microsoft Azure infrastructure via Vault.
The release also includes additional new features, secure workflow enhancements, general improvements, and bug fixes. The Vault 0.11 changelog provides a full list of features, enhancements, and bug fixes.
As always, we send a big thank-you to our community for their ideas, bug reports, and pull requests.
»Namespaces
Note: This is a Vault Enterprise Pro feature
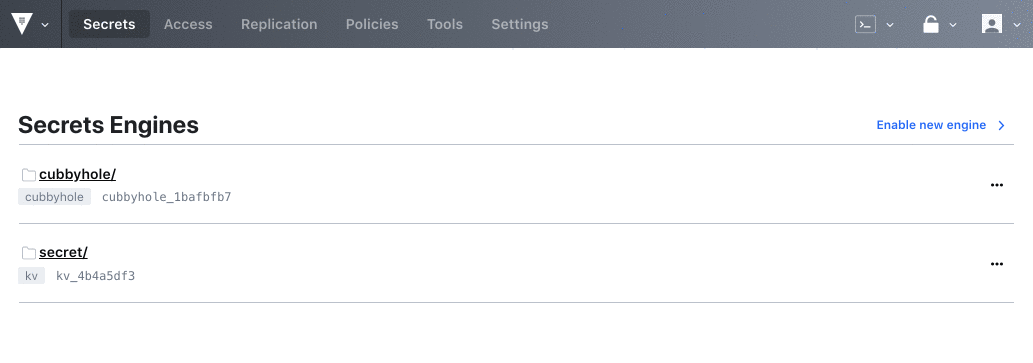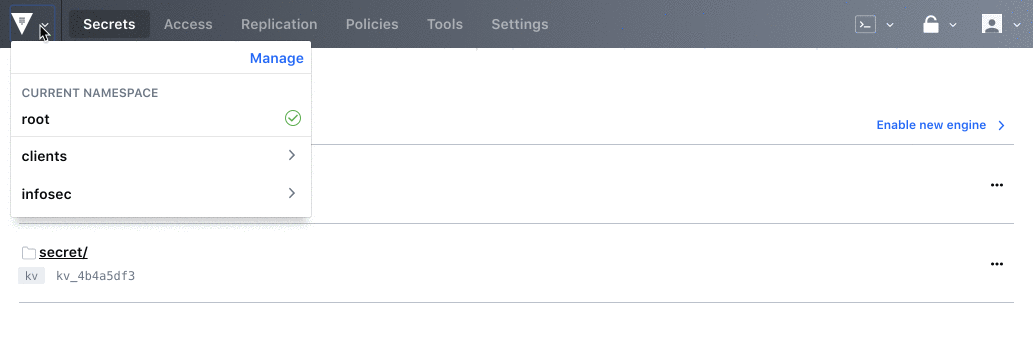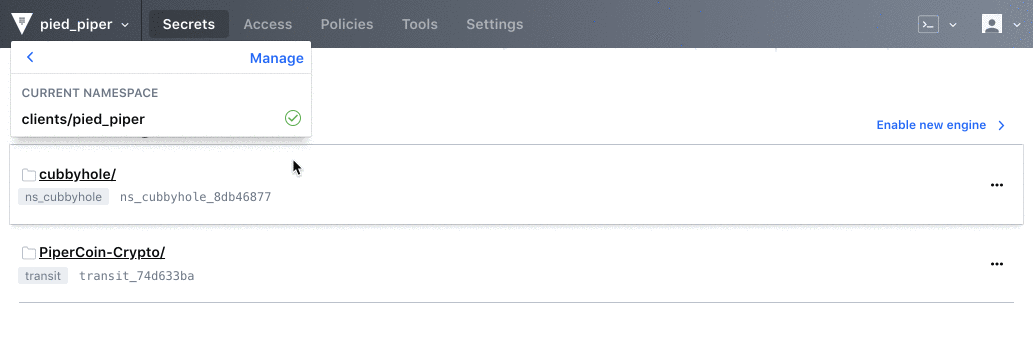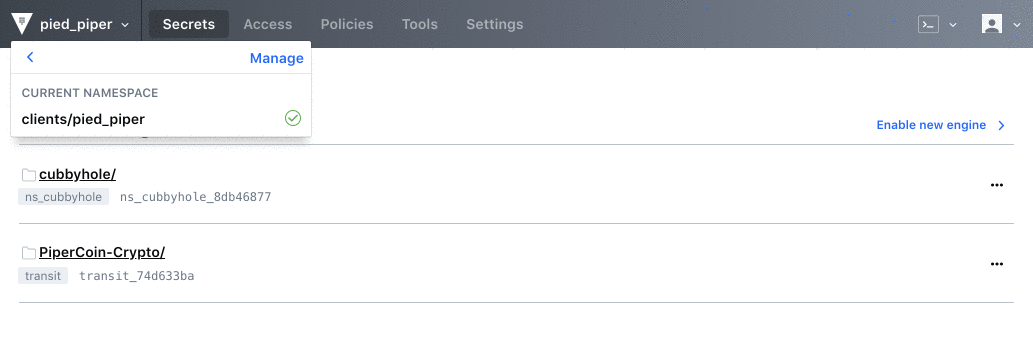
Vault 0.11 sees the new introduction of Namespaces, a suite of features that allows Vault Enterprise users to create isolated environments to support secure multi-tenancy within a single Vault Enterprise infrastructure. This allows for multiple teams or organizations to operate within separate environments that can be centrally managed and configured by a central ops or security team.
Within a namespace, users and applications can create and manage separate versions of the following:
- Secret Engines
- Auth Methods
- Identities (Entities and Identity Groups)
- Policies
- Tokens
Namespaces also allow members of a namespace to be delegated as administrators, allowing them to self-manage policies that apply only within that namespace. This significantly reduces the management burden of Vault Enterprise, allowing teams (and even individuals) to self-manage their own environments.
For more on namespaces, see our in-depth feature preview.
»Performance Standby Nodes
Note: This is a Vault Enterprise feature
Performance Standby Nodes (or simply "Performance Standbys") are a new node type within Vault to multiply Vault's ability to serve read-only operations (that is, operations that do not modify Vault's storage) within a single cluster. A selection of performance standby nodes come standard with Vault Enterprise Premium, and they can be added to Vault Enterprise Pro infrastructures.
A performance standby is just like a traditional High Availability (HA) standby node but is able to service read-only requests from users or applications. This allows for Vault to quickly scale its ability to service these kinds of operations, providing near-linear request-per-second scaling in many common scenarios for some secrets engines like K/V and Transit. By spreading traffic across performance standby nodes, clients can scale these IOPS horizontally to handle extremely high traffic workloads.
»Vault Agent
Vault Agent is a new mode for the Vault binary that allows Vault to automatically manage the process of securely introducing and rotating access tokens for a system. By configuring an auto-auth system with a Vault 0.11+ binary, Vault can be run as an agent that provides fresh local access tokens on a system for applications and users to leverage in accessing secrets.
For more on Vault Agent, see our in-depth feature preview.
»ACL Templates
In Vault 0.11 policies may now use templates to explicitly refer to entities, identities groups, and metadata within policies. This allows policies that are easier to manage and more explicit when granting RBAC to specific identities within Vault.
For example, a policy may now be written to carve out storage for a specific entity:
path "secret/data/{{identity.entity.id}}/*" {
capabilities = ["create", "update", "read", "delete"]
}
Or a policy can be written to assign RBAC to an identity group, allowing any member of the group to successfully perform operations but disallowing anyone else:
path "secret/data/groups/{{identity.groups.ids.fb036ebc-2f62-4124-9503-42aa7A869741.name}}/*" {
capabilities = ["create", "update", "read", "delete"]
}
»Alibaba Cloud Support
Vault now supports integration with Alibaba Cloud. Vault 0.11 sees the release of Alibaba Auth Methods and an Alibaba Cloud Secrets Engine - both of which allow users to login with Alibaba Cloud credentials and generate dynamic credentials for access to an Alibaba Cloud infrastructure respectively.
Vault users can also configure Alibaba Cloud storage targets as a Storage backend with Vault 0.11, and in the near future we will release functionality to allow Vault Enterprise users to Auto Unseal and Seal Wrap using Alibaba Cloud KMS.
»Microsoft Azure Secret Engine
Vault 0.11 now supports a Secrets Engine plugin that allows for Vault users to create dynamic access credentials to Microsoft Azure systems. Using time-limited service principals, Azure Secrets Engine allows Vault to broker secure access for users and applications provisioning resources on Azure.
»Other Features
There are many new features in Vault 0.11 that have been developed over the course of the 0.10.x releases. We have summarized a few of the larger features below, and as always consult the Changelog for full details.
- JWT/OIDC Discovery Auth Method: A new auth method that accepts JWTs and either validates signatures locally or uses OIDC Discovery to fetch the current set of keys for signature validation. Various claims can be specified for validation (in addition to the cryptographic signature) and a user and optional groups claim can be used to provide Identity information.
- UI Control Group Workflow (Enterprise): The UI will now detect control group responses and provides a workflow to view the status of the request and to authorize requests
- Active Directory Secrets Engine: A new ad secrets engine has been created which allows Vault to rotate and provide credentials for configured AD accounts. This Secrets Engine also supports automated rotation of its root credential.
- Azure Key Vault Support: Support for Microsoft Azure Key Vault for Auto Unseal and Seal Wrap.
- HA Support for MySQL Storage: MySQL storage now supports HA.
- Vault UI Browser CLI: The UI now supports usage of read/write/list/delete commands in a CLI that can be accessed from the nav bar. Complex inputs such as JSON files are not currently supported. This surfaces features otherwise unsupported in Vault's UI.
- FoundationDB Storage: You can now use FoundationDB for storing Vault data.
»Upgrade Details
Vault 0.11 introduces significant new functionality. As such, we provide both general upgrade instructions and a Vault 0.11-specific upgrade page.
As always, we recommend upgrading and testing this release in an isolated environment. If you experience any issues, please report them on the Vault GitHub issue tracker or post to the Vault mailing list.
For more information about HashiCorp Vault Enterprise, visit https://www.hashicorp.com/products/vault. Users can download the open source version of Vault at https://www.vaultproject.io.
We hope you enjoy Vault 0.11!