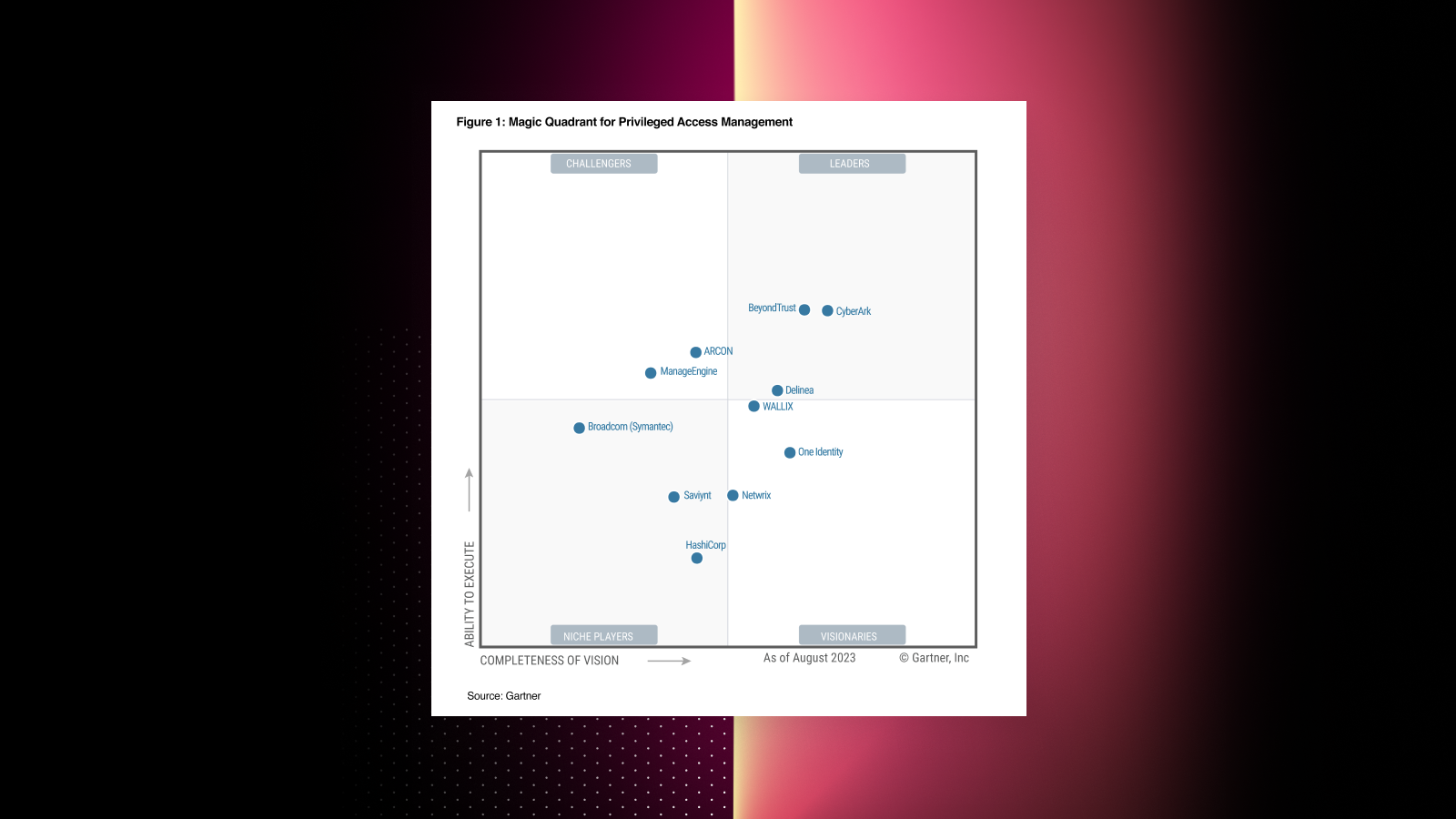
For the first time, HashiCorp has been named in the 2023 Gartner® Magic Quadrant™ for Privileged Access Management (PAM). Our inclusion in the Magic Quadrant (MQ) Niche quadrant validates HashiCorp’s approach, based on what we see as the five essential principles for modern PAM.
Throughout its history, HashiCorp has demonstrated a different approach to creating products to solve customer problems. For example, we created and built entirely new markets with breakthrough products like HashiCorp Terraform and Vault, which have become de facto standards for infrastructure as code (IaC) and secrets management. We are approaching PAM the same way, working to give our customers the capabilities they need rather than the complexity they don’t. We’re focused on where PAM requirements are going, not just where they’ve been.
»First inclusion in a Gartner Magic Quadrant
Gartner has begun to reevaluate the PAM market, which led to a change in the PAM MQ criteria, and the inclusion of HashiCorp for the first time. HashiCorp met the inclusion criteria with a solution combining our newest product, HashiCorp Boundary and one of our most popular products, HashiCorp Vault. These two products can be used together to solve new challenges around PAM that come from using the cloud. Built for this new reality, they take a modern approach to PAM and offer customers a consistent cloud operating model across all environments.
That focus means our offerings don’t look exactly like the current or previous generations of PAM solutions. Instead, our investments are focused on solving customers’ challenges in identity-based remote access for today and tomorrow. That aligns with our R&D approach — developing world-class capabilities around a specific set of modern core use cases focused on workflows not technologies, and based on hundreds of conversations with customers.
»The 5 essential principles of HashiCorp’s approach to modern PAM
At HashiCorp, we develop products to enable a cloud operating model based on automation and lifecycle management. Terraform, for example, disrupted traditional configuration management by focusing on infrastructure as code to become the industry standard for infrastructure provisioning and management. Vault disrupted legacy on-premises secrets management solutions with a cloud-centric and DevOps-friendly approach to identity-based security. It is now the de facto standard for secrets brokering and management, with organizations like Starbucks, Vodafone, Q2, GitHub, Wayfair, Ubisoft, and many others relying on Vault to secure their applications.
We’re committed to the same approach with Boundary, offering an alternative to solutions that require highly manual configurations not optimized for cloud and/or rely on IP-based security. Our approach focuses on five core principles to enable modern PAM, centered on identity-based controls in cloud-driven environments:
»1. Authentication and authorization
Authentication and authorization are critical to modern PAM solutions. Rather than creating and managing another source of identity, organizations should use the systems already in place. That means customers need capabilities like single sign-on (SSO) integration as well as the ability to create roles and logical services.
With Boundary, users can leverage their existing providers via the OpenID Connect (OIDC) and LDAP authentication protocol to enable SSO access to trusted providers. In addition, Boundary leverages identities’ permission claims to assign roles to users or groups, and for authorizing access to logical services. This lets organizations tightly control access and actions performed against systems and automate provisioning of the groups/roles to which you have access.
»2. Time-bound, least-privileged access
It’s not enough to enable least privileged access to users by default. Traditional PAM solutions do not ensure secure user access is limited to predetermined periods of time on an as-needed basis to mitigate risk. Boundary and Vault ensure users have the minimum amount of access to sensitive credentials, networks, endpoints, and data to accomplish a task. For credentials, HashiCorp’s modern PAM solution provides a differentiated approach by integrating Vault-managed secrets into Boundary for a consolidated workflow. Vault has industry-leading secrets management capabilities and supports a broad ecosystem of integrations for managing SSH usernames and passwords, SSH certificates, x509 certificates, database accounts, Windows accounts, Kubernetes service accounts, and many other endpoint types.
Administrators can choose Vault to generate just-in-time credentials and use Boundary’s credential injection feature, which secures user sessions by injecting single-use credentials so that secrets are never returned to users. That gives end users passwordless access.
When it comes to networks, HashiCorp’s modern PAM solution provides time-limited network access via proxies that connect directly to private endpoints via TCP/IP, avoiding the need to expose your network to users. And to support role-based permissions, Boundary’s managed groups let teams dynamically assign user permission workflows to enable just-in-time permissions based on IdP-level context such as identity provider (IdP) MFA checks and group memberships in order to authorize user access to resources. Lastly, Boundary’s role-based access controls can granularly control access to specific services and systems.
»3. Automation and flexible deployment
Beyond using automation to ensure PAM processes are secure, we see automated onboarding of services as an essential component of a modern PAM solution, especially in extremely dynamic and multi-cloud environments. However, traditional PAM solutions lack the ability to discover and onboard newly deployed services automatically. Boundary includes automated controls to facilitate onboarding of services via Terraform for preconfigured security policies or using dynamic host catalogs, which automatically discover on-boarding new or changed infrastructure resources and their connection information, such as Amazon EC2 hosts and Microsoft Azure virtual machines. This workflow automates the process of on-boarding new or changed infrastructure resources and their connection information.
Also, we are committed to enabling flexible deployments across our product line. Unlike other PAM offerings that require installation of multiple components, customers can deploy Boundary as a single binary on-premises or in the cloud via a self-hosted version, or as a managed service offering on the HashiCorp Cloud Platform (HCP).
»4. Streamlined DevOps workflow
Privileged access management increasingly focuses on enabling faster developer productivity using a consolidated, everything-as-code approach. This is especially important for Privileged Elevation and Delegation Management (PEDM), a category of PAM where specific privileges are granted via host-based agents to log in users. This traditional approach creates higher operational complexity by requiring users to deploy and manage host agents across many systems. Additionally, an agent-based approach breaks down for modern target endpoints that no longer have the concept of “instances” where you might deploy an agent (as in a Platform-as-a-Service environment) or shift the point of control to an API where an agent can’t be deployed.
In contrast, HashiCorp focuses on optimizing DevOps workflows to solve these types of problems. Boundary and Vault leverage configuration as code workflows to configure target endpoints, target account permissions, and access controls as a more durable way to support modern endpoints such as APIs and Platform-as-a-Service (PaaS). Our approach — using programmatic interfaces and configuration as code workflows — separates HashiCorp from the many agent-based solutions in the PAM market.
»5. Auditing and logging
Auditing and logging are essential to support organizations’ compliance and regulatory requirements. Boundary session recording and audit logs let HashiCorp customers track user and application actions when accessing critical systems. Customers can record every SSH session and play back detailed commands and actions executed by each user. Our PAM solution maintains an auditable record of all activities to enhance compliance, and logs user access to infrastructure resources as well as the Vault and Boundary components.
»Investing in PAM going forward
Going forward, we’ll continue to focus on and invest in least-privilege as a design philosophy, PAM as a solution to help address the impact on security teams as they transition to a cloud operating model, and capabilities that give security administrators visibility into actions across their digital estates.
For example, we released session recording in June 2023 (after the cutoff for inclusion in Gartner’s 2023 MQ evaluation) and we’ll continue to invest in supporting session recording for additional target types and auditing capabilities. We also see customer interest in agentless workflows that deliver the security benefits of traditional PAM solutions while enabling automated onboarding and management of complex estates of ever-changing cloud resources and identities. That’s why we continue to grow Boundary’s broad ecosystem of providers and target types that support passwordless access. For more information on Boundary, watch this short video explaining what Boundary is and how it works.
Inclusion in our first Gartner PAM MQ represents an important milestone. And we are pleased to see Gartner’s openness to evolving its views of PAM as the firm begins to recognize the changing needs of organizations.
HashiCorp offers Community and Commercial versions of Vault and Boundary. Commercial versions provide enterprise capabilities needed to deliver PAM, using Vault and Boundary as standardized shared services for your organization.