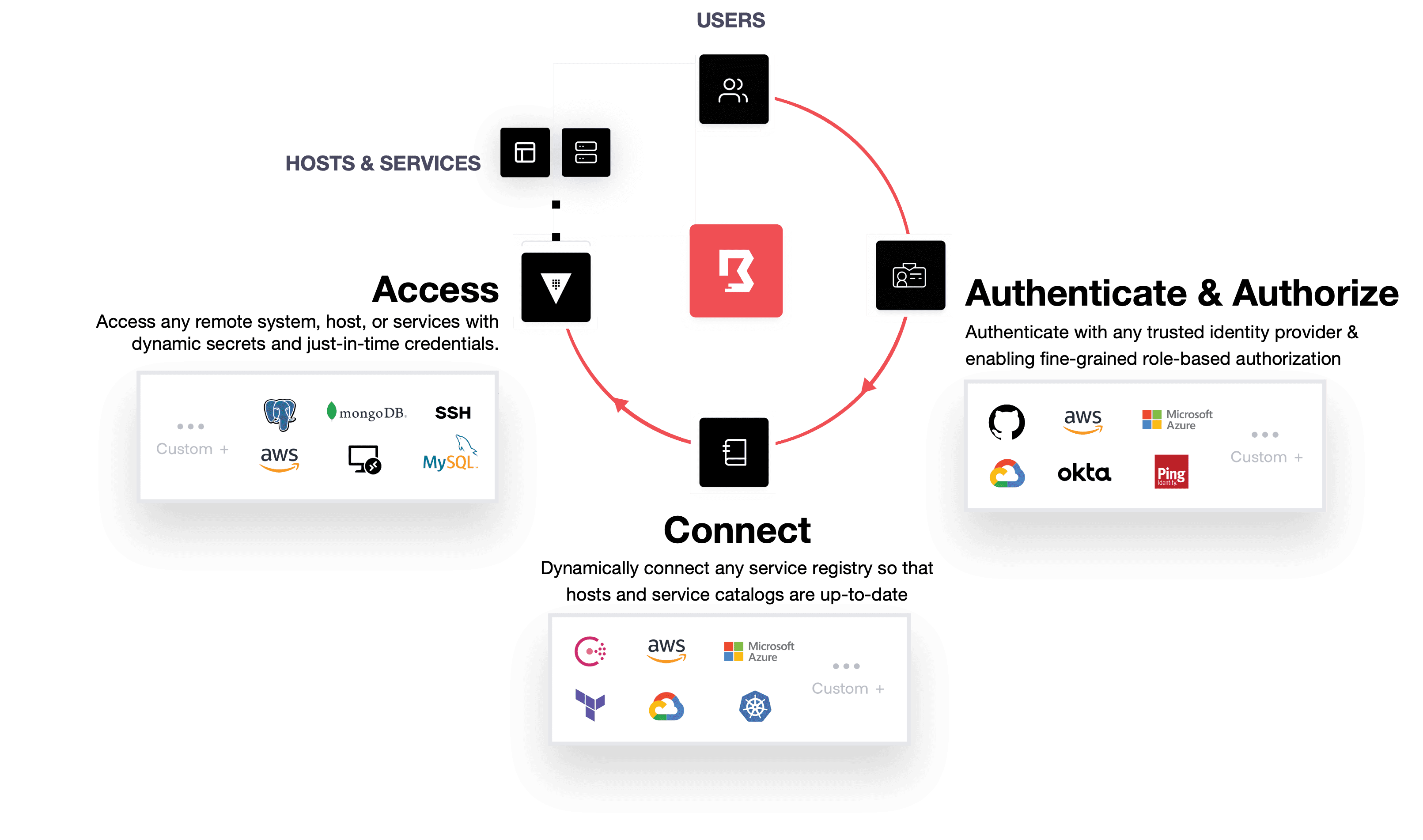
Today at HashiConf Europe, HashiCorp launched Boundary on the HashiCorp Cloud Platform (HCP Boundary) which is now in public beta. We first released HashiCorp Boundary as an open source project in October 2020 to provide an easy way to securely and remotely access critical systems with fine-grained authorizations based on trusted identities. HCP Boundary builds on top of this power and flexibility to provide a single, fully managed, cloud-based workflow to securely connect to remote hosts and critical systems across cloud service catalogs, on-premises infrastructure, and Kubernetes clusters, without needing to manage any of the underlying systems or operations. HCP Boundary is the first solution of its kind to automate onboarding of users and targets to streamline secure remote access with integrations with leading identity providers (IDPs) and service catalogs and registries.
The need for secure remote access to dynamic, heterogeneous environments is growing rapidly (according to the 2021 HashiCorp State of Cloud Strategy Survey, 76% companies say they are already multi-cloud). However, today's solutions — VPNs, SSH bastions, and PAM — fail to scale effectively in ephemeral, multi-cloud environments. Current solutions are complex and require multiple network addresses, credentials, permissions, and broad expertise for users to access remote hosts and systems. These solutions also give users access to entire networks and credentials to manage and protect on their own, oftentimes requiring multiple credentials for the network, hosts, and possibly services. With ephemeral environments, maintaining addresses is even more brittle and onboarding or offboarding users is incredibly manual, requiring a lot of overhead, help desk tickets, and so on.
HCP Boundary abstracts away the complexity so users can simply log in, choose the host or system they want to connect to, and connect. HCP Boundary handles all of the addresses, connections, and even credentials on the backend. Nothing is exposed to the user, meaning users can securely connect to their remote system or host and never see a credential, address, or network. HCP Boundary is secure remote access, made easy.
»Putting Developers At the Forefront of Access
HCP Boundary is the first solution of its kind to put developers and technical users at the forefront of its access design. In most instances, traditional access solutions (e.g. privileged access management, or PAM) are optimized for operators and administrators, but overlook the users, who need timely, secure access to critical infrastructure. DevOps engineers, application developers, and other personnel who require infrastructure access need an easy, standardized way to access their environments, wherever they reside, without filing tickets with their Ops team and potentially waiting weeks to be manually onboarded.

Dashboard shows targets that have been automatically onboarded.
»Automate Your Remote Access Workflows
HCP Boundary fully automates workflows for both user and target onboarding, which drastically minimizes the configuration overhead for operators and, unlike traditional access solutions, enables them to keep users and targets up-to-date in cloud environments.
First, HCP Boundary integrates with trusted identity platforms, such as Azure Active Directory, Okta, Ping, and many others that support OpenID Connect, to onboard trusted identities and delegate authentication. Next, operators can configure fine-grained authorization to critical systems and infrastructure based on identity (individual users can also do this for themselves). HCP Boundary then streamlines connection to hosts and targets by automating service discovery and access configuration as workloads are deployed or changed (dynamic host catalogs are currently available with AWS and Microsoft Azure).
This is critical in ephemeral, cloud-based environments so that operators don’t need to continually reconfigure access lists. Finally, HCP Boundary integrates with HashiCorp Vault, our secrets management solution, to broker credentials for critical infrastructure that are valid only for that session. This means no credentials are shared, so they won’t be accidentally lost or leaked.
With HCP Boundary, there are no SSH keys or VPN credentials to manage, no manual onboarding of target hosts and services, and no hard-coded or shared credentials for critical infrastructure. The result is a vastly simplified onboarding experience that reduces the risk of a credential compromise.
»No More Exposing Networks
Across clouds, local datacenters, and low-trust networks, HCP Boundary provides an easy solution to protect and safeguard access to applications and critical systems by leveraging trusted identities without exposing the underlying network. HCP Boundary is an identity-aware proxy that sits between users and the infrastructure they want to connect to. The proxy has two components:
- A control plane that manages state around users under management, targets, and access policies, and a group of external providers HCP Boundary can go to for service discovery.
- Worker nodes, assigned by the control plane once a user authenticates into HCP Boundary and selects a target to connect to. They are stateless proxies that need to have end-network access to targets under management.
HCP Boundary presents the session to the user as a TCP tunnel and it’s wrapped in mutual TLS, which mitigates the risk of a man-in-the-middle attack. Ultimately, if a user is connecting to a target over SSH through an HCP Boundary tunnel, there are two layers of encryption: the SSH session that user creates, and underlying TLS that HCP Boundary creates.
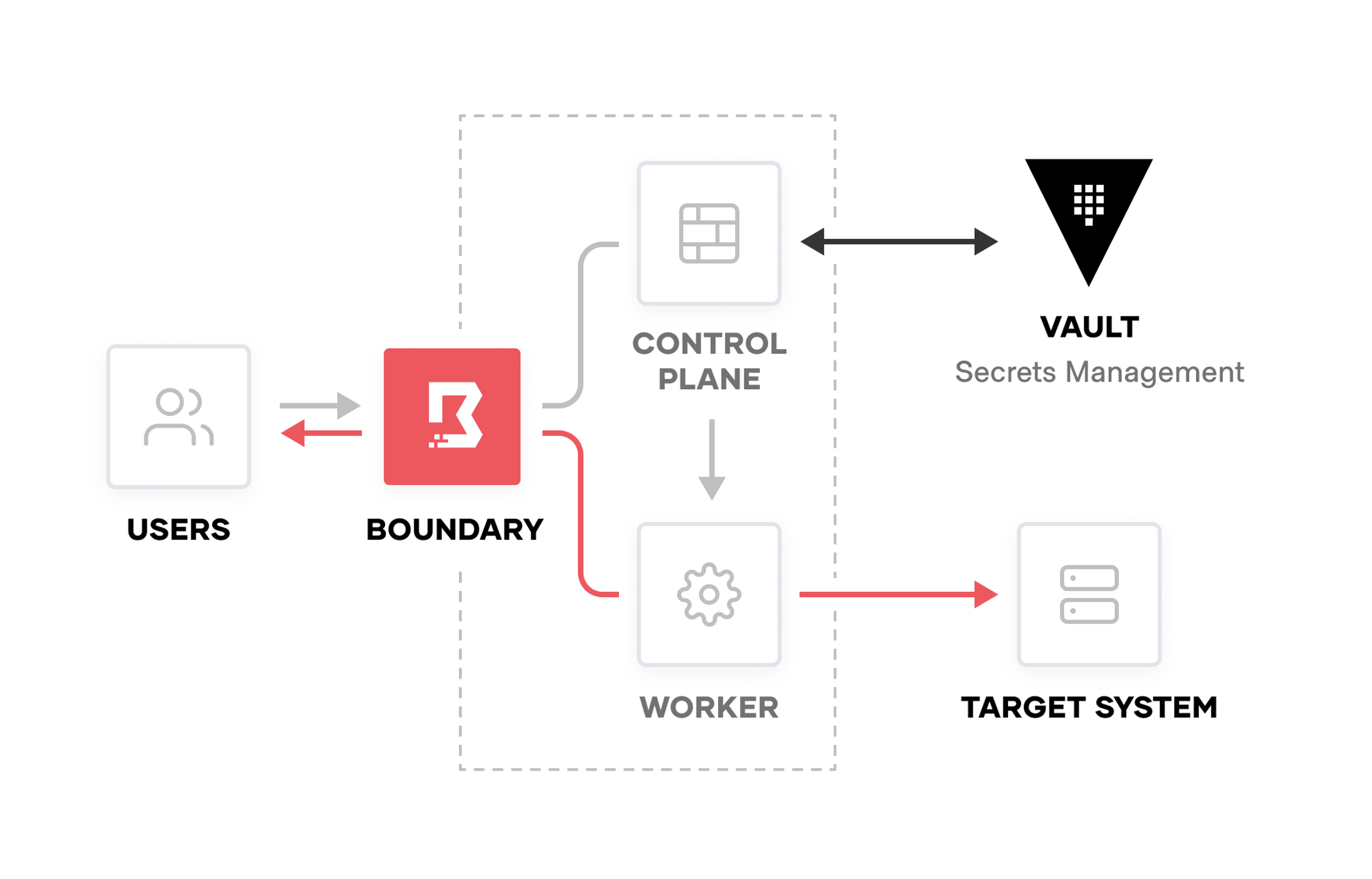
HCP Boundary access model.
HCP Boundary is fully managed by HashiCorp, but users can choose to self-manage Boundary workers (i.e. Boundary’s gateway nodes).
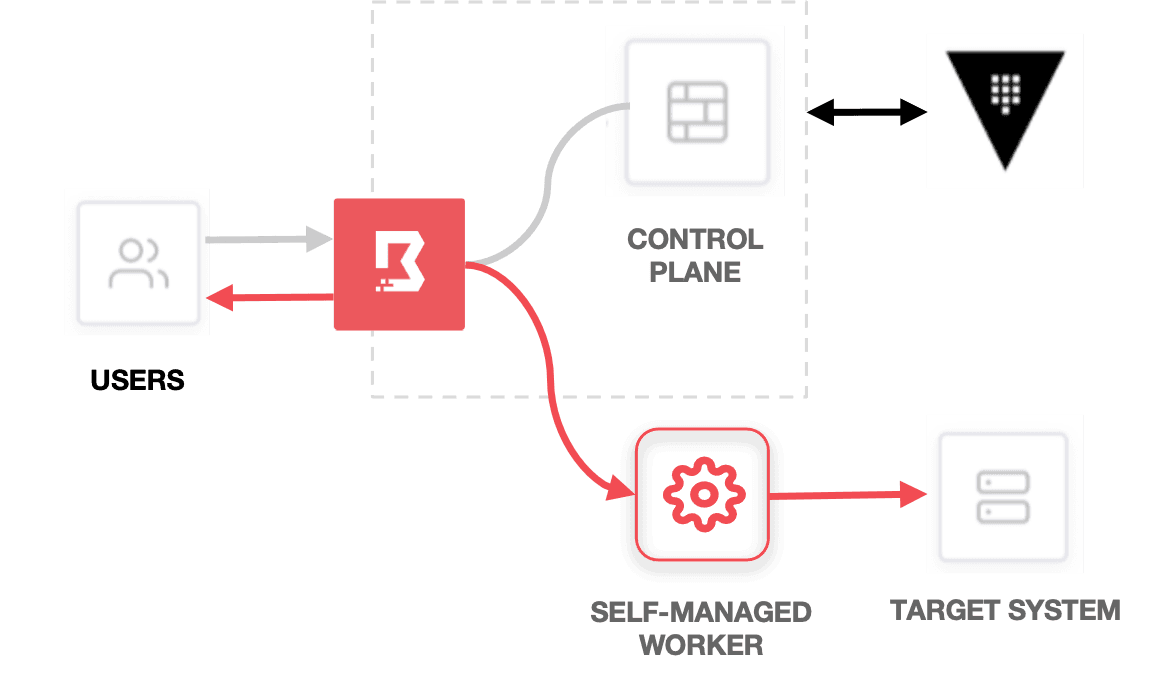
HCP Boundary with self-managed workers.
Self-managing your workers allows your Boundary users to securely connect to private endpoints (e.g. targets and Vault) without exposing your networks to the public or even to HashiCorp-managed resources.
»Try HCP Boundary Beta Free Today
Try HCP Boundary today and get started connecting securely to your first target infrastructure in less than 15 minutes. To get started, sign up for HCP Boundary for free and check out the HCP Boundary tutorial on HashiCorp Learn.
We want to hear from you. Once you’re up and running, please feel free to send us feedback.








