We are pleased to announce the general availability of HashiCorp Vault 1.16. HashiCorp Vault provides secrets management, data encryption, identity management, and other workflow capabilities for applications on any infrastructure.
Vault 1.16 focuses on enhancements to Vault’s performance and administration as well as support for new integrations and workflows. Key additions in this release include:
- Secrets sync
- Customizable GUI banners
- Proactive event notifications
- PKI secrets engine support for Enrollment over Secure Transport (EST) (beta)
- Plugin workload identity
- Audit log filtering
- Vault Secrets Operator enhancements
- Vault Enterprise Long-Term Support (LTS)
Let’s take a closer look:
»Secrets sync (Enterprise, GA)
Vault Enterprise secrets sync supports one-way synchronization of Vault’s KV v2 secrets with five external destinations:
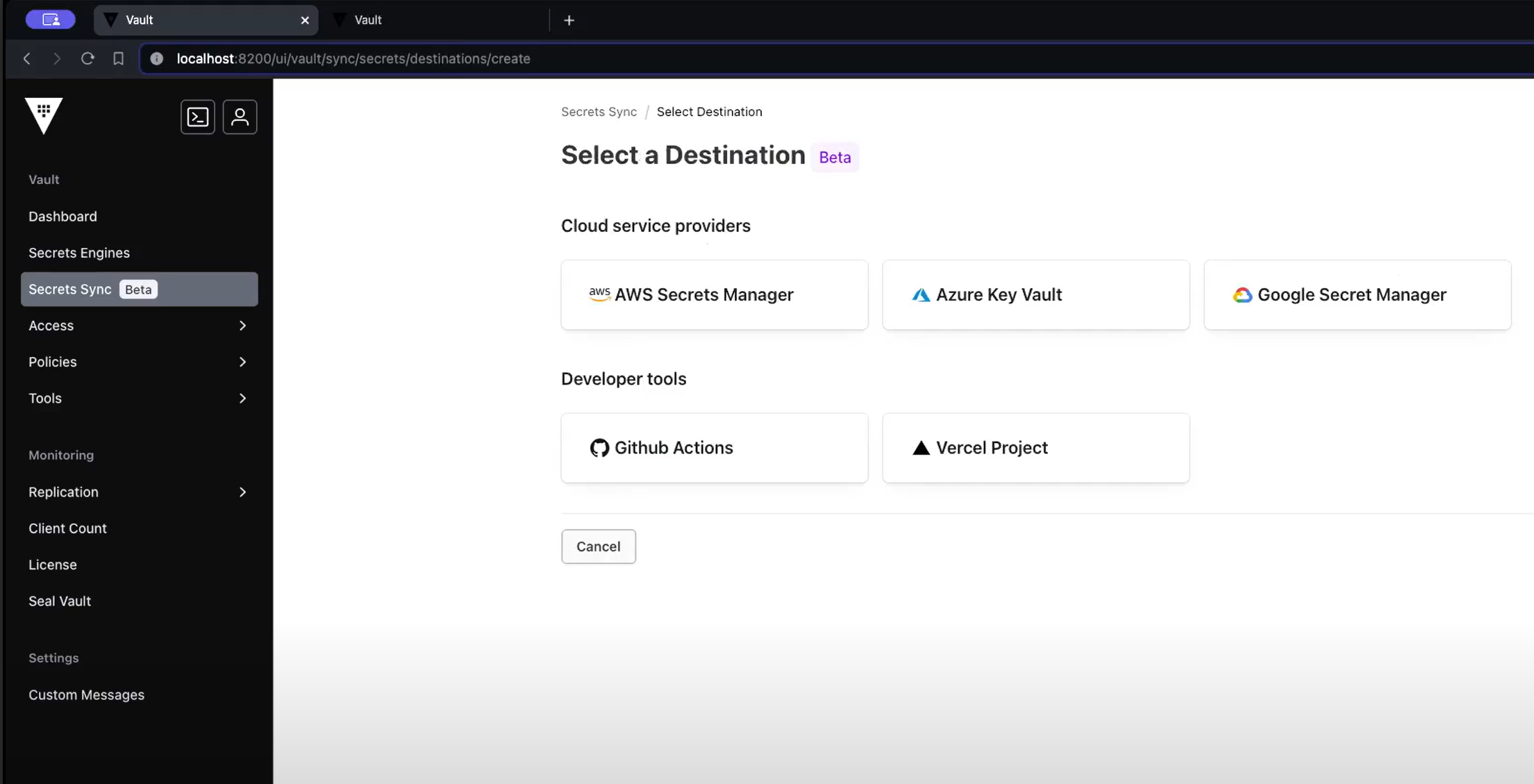
- AWS Secrets Manager
- Microsoft Azure Key Vault
- Google Cloud Secret Manager
- GitHub Action Secrets
- Vercel Project Environment Variables
To solve the problem of some managed services requiring users to fetch secrets from the native cloud-service provider’s secrets manager, secrets sync synchronizes secrets to the five destinations listed above. This capability lets Vault remain the system of record for these secrets, caching them as read-only values in the external system. Users can then read the secrets from the external secret manager.
Learn more in the deep dive blog post: Secrets sync now available on Vault Enterprise to manage secrets sprawl
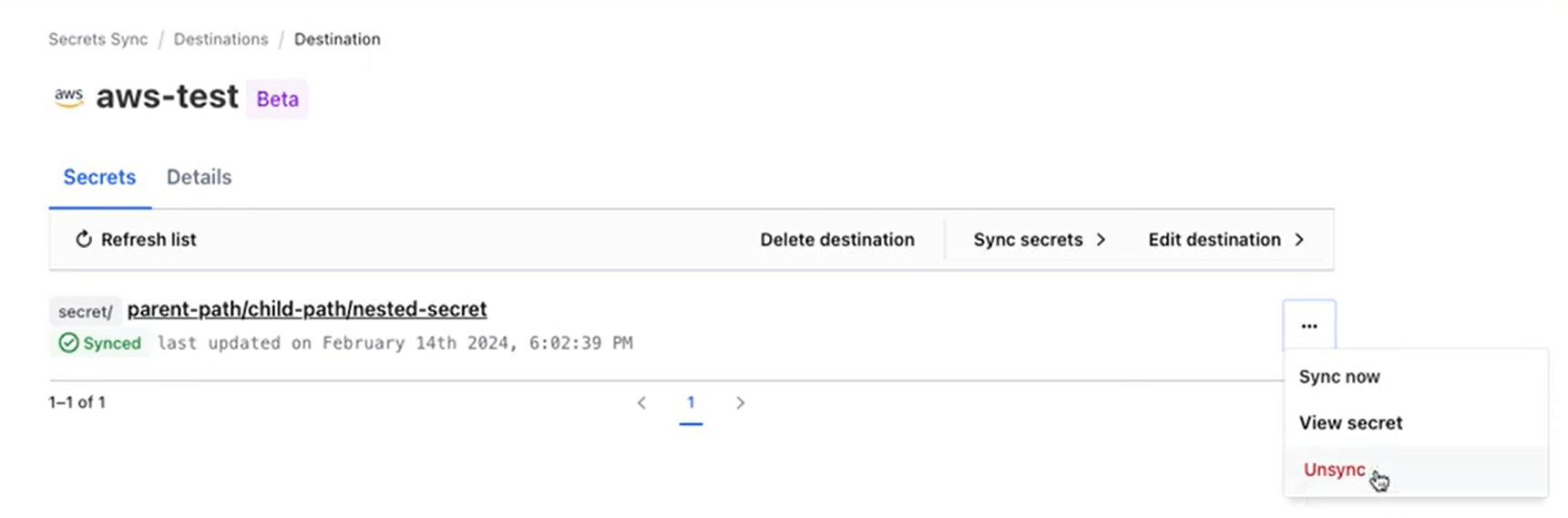
Detailed sync management
Based on customer feedback from the beta release, today’s GA release includes feature and performance improvements along with significant UI enhancements to provide a richer management experience. For example, it is now possible to create and configure a sync destination completely within the user interface.
»Customizable GUI banners (Enterprise)
This new capability addresses important feedback from customers requesting the ability to make announcements to their internal Vault users with important information such as scheduled maintenance or known issues. Here is a simple example:
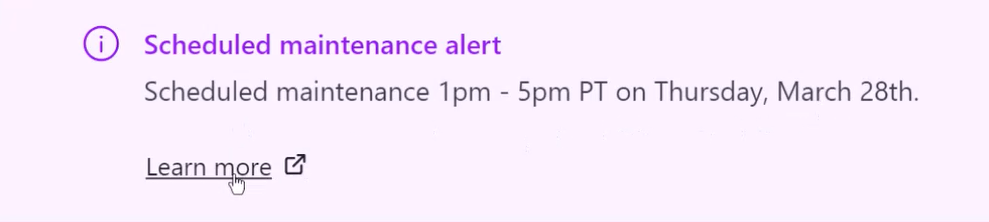
It allows admins to configure custom messages that display on the login page both before and after you log in. The amount of time those messages live is also configurable. The ability to make proactive announcements promises to help reduce the support load on operators by keeping relevant announcements inside the context of Vault, rather than through external channels.
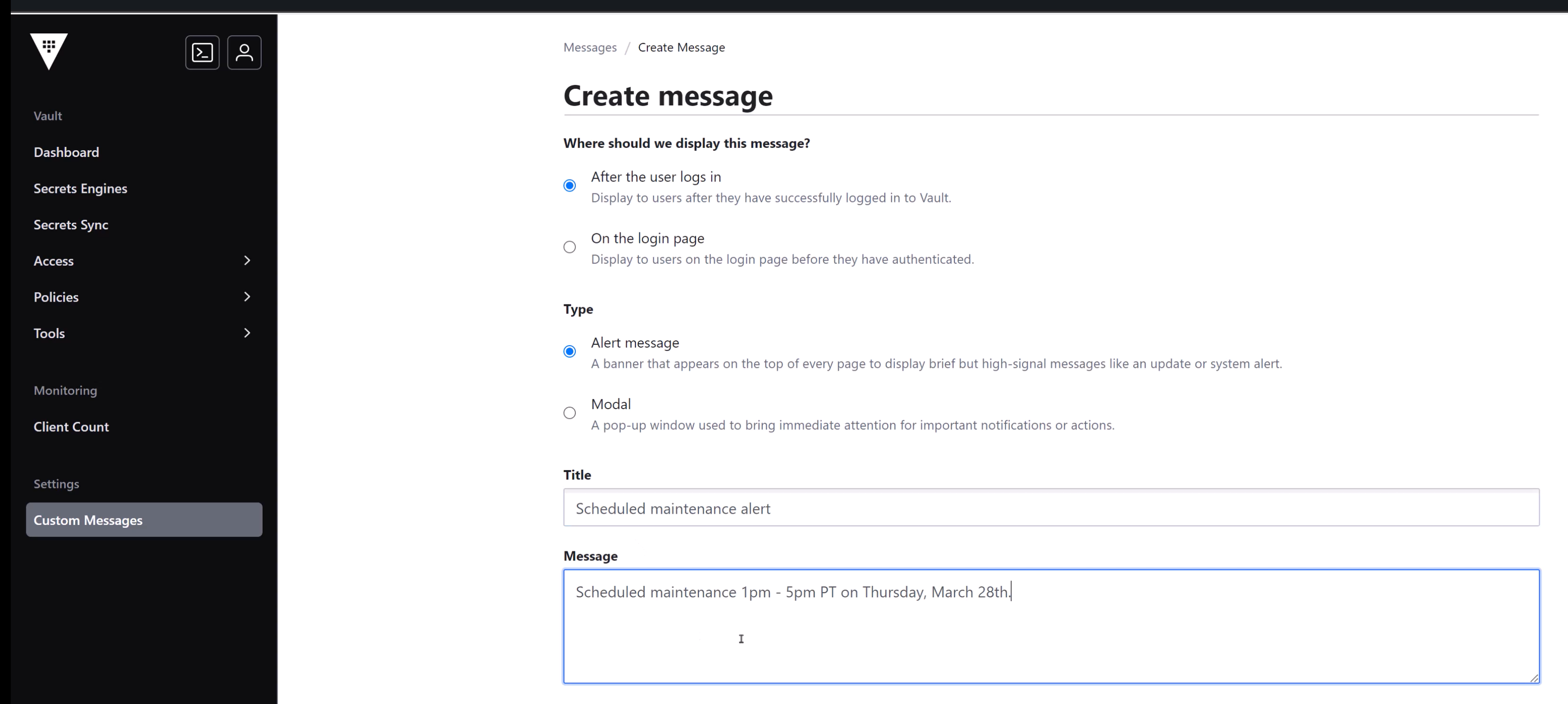
Create custom messages
»Proactive event notifications (Enterprise)
Customers want to know immediately when certain events occur, such as when a secret is created, modified, or deleted. Applications and external integrations that rely on Vault for secrets management also need to be alerted when a secret in Vault is updated. This new event notification system allows subscribers to register to be notified of changes to their KV v2 or database secrets. At release, subscribers can include destinations such as the Vault agent (to allow for static secret caching), Vault subsystems such as plugins, or another Vault instance. We plan to support more secrets engines in the future.
»PKI support for IoT/EST based devices (beta)
In response to customer demand for automated certificate enrollment and management using the Enrollment over Secure Transport (EST) protocol, this release includes a beta capability to natively support EST in Vault PKI. EST is an industry standard protocol for securing devices based on PKI certificates. Vault customers can take advantage of this capability to manage large-scale certificate issuance for EST-capable devices such as IoT devices, network devices, routers, etc.
»Plugin workload identity (Enterprise)
This new plugin capability helps eliminate long-lived cloud provider credentials for auth methods, secrets engines, and secret syncing. Admins can now use workload identity federation (WIF) to establish trust relationships and enable the exchange of identity from one system with another. For example, a Vault-created identity token can be exchanged for AWS credentials provided there is a trust relationship between Vault and AWS. This promises to eliminate a class of concerns around providing security credentials to Vault plugins.
»Customized audit log filtering (Enterprise)
In response to customer requests for greater customization of audit logs to support compliance needs, audit logs are now tunable so that customers can specify which fields they want to log and where to send those logs based on their content. This new capability lets customers collect specific events to better meet their compliance reporting needs.
»Vault Secrets Operator (VSO) enhancements
Since the release of Vault Secrets Operator for Kubernetes in June of 2023, we continue to enhance the capability to directly connect Vault to native Kubernetes secrets. The recent VSO 0.5 release, included two feature enhancements based on customer requests:
- A rich templating library to transform secrets from Vault or HCP Vault Secrets, before storing them in the destination Kubernetes Secret. This gives customers the flexibility to fine tune the secrets to match the required formats.
- To enable upgradability for Vault Enterprise customers via OperatorHub in Red Hat OpenShift, VSO now provides seamless upgrades with the Operator Lifecycle Manager (OLM).
Note: VSO supports multiple recent Vault releases and is released asynchronously to Vault.
»Vault Enterprise Long-Term Support (LTS)
For customers who are comfortable doing minor version upgrades, but can’t fit in a major version jump more than once every two years, LTS provides a way to stay on a single major version and receive critical bug and security fixes after the first year.
Vault Enterprise joins other HashiCorp products in offering LTS with the following key characteristics:
- Extended maintenance: Two years of critical fixes provided via minor releases
- Efficient upgrades: Support for direct upgrades from one LTS release to the next, reducing major version upgrade risk and improving operational efficiency
LTS is available now to all Vault Enterprise customers with self-managed deployments. To upgrade your Vault Enterprise deployment to an LTS version (1.16), refer to Vault’s upgrade documentation. If you currently have Vault Enterprise 1.16 deployed, you’re already running a maintained LTS version — no further action is required at this time. For more information, visit the LTS documentation page.
»Upgrade details
This release also includes more new features, workflow enhancements, general improvements, and bug fixes. All of these updates can be found in the Vault 1.16 changelog. Please visit the Vault release highlights page for step-by-step tutorials demonstrating the new features.
As always, we recommend upgrading and testing new releases in an isolated environment. If you experience any issues, please report them on the Vault GitHub issue tracker or post to the Vault discussion forum. As a reminder, if you believe you have found a security issue in Vault, please responsibly disclose it by emailing security@hashicorp.com — do not use the public issue tracker. For more information, please consult our security policy and our PGP key.
For more information about HCP Vault and Vault Enterprise, visit the HashiCorp Vault product page.








