We are excited to announce the release of HashiCorp Vault 0.9. Vault is an infrastructure automation security product that provides secrets management, encryption as a service, and privileged access management.
The 0.9 release of Vault is focused on new functionality that improves Vault’s governance and data security capabilities across globally-distributed, multi-cloud environments.
New features in 0.9 include the following:
-
**Identity**: An integrated system for understanding the identity of a person or system across their logins and tokens and using this information for policy and access control decisions. This consists of two parts:
- **Entities**: A representation of a single person or system that is consistent across logins to simplify access control and auditing. Entities tie clients into a long-lived logical identity that can be more easily managed. Clients can associate their logical identity with multiple identity services.
- **Groups**: Collections of Entities and other Groups that understands group memberships from upstream identity providers and provides easy assignment of policies and access control. Groups can be members of other groups, allowing for better organizational modeling and management.
- **Seal Wrap / FIPS 140-2 Compliance (Vault Enterprise)**: Vault can take advantage of FIPS 140-2-certified HSMs to ensure that Critical Security Parameters are protected in a compliant fashion. Vault’s implementation has received a letter of compliance from Leidos.
- **New Vault UI (Vault Enterprise)**: A new user experience for graphically managing Vault clusters.
- **Control Groups (Vault Enterprise)**: Require multiple Identity Entities or members of Identity Groups to authorize an requested action before it is allowed to run.
- **Cloud Auto-unseal (Vault Enterprise)**: Automatically unseal Vault clusters using AWS Key Management System (KMS) and Google Cloud Platform (GCP) Cloud KMS.
- **Sentinel Integration (Vault Enterprise)**: Take advantage of HashiCorp Sentinel to provide extremely flexible access control policies -- even on unauthenticated endpoints.
The release also includes additional new features, secure workflow enhancements, general improvements, and bug fixes. The Vault 0.9 changelog provides a full list of features, enhancements, and bug fixes.
As always, we send a big thank-you to our community for their ideas, bug reports, and pull requests.
»Identity
Vault 0.9 introduces a new means of managing access to secrets via the new Identity system. This system allows Vault to understand the identity of individual users and machines across their tokens, and manage them via groups. There are two fundamental components of the Identity system: entities and groups.
Identity Groups will serve as a major piece of Vault’s Privileged Access Management story going forward, and we will build on this feature with new enhancements and functionality in future releases of Vault and Vault Enterprise. Some more information follows; full Identity documentation is available here.
»Identity Entities
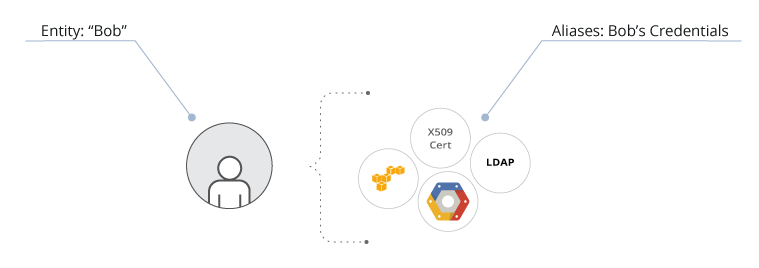
Entities are single, logical identities that represent users and applications across any tokens they have generated using auth backends, even multiple auth backends. For example, a user may have AWS credentials as well as LDAP or Active Directory credentials. These separate credentials (known as Aliases within Vault Identity) and all of the tokens generated by these credentials are all recognized as referring to the single user or application within various parts of Vault. Vault simplifies administration across multiple Identity Providers (IDP) by bridging them into a common identity.
Vault will automatically create an Entity if one does not exist for any client gaining access to a secret within Vault. Entities can have policies assigned to them that apply to all tokens associated with that entity. They can also be referenced in Sentinel policies, and custom metadata set on the entity can also be referenced within Sentinel policies. This can be used to do grouping of entities, but the Identity system also supports real groups.
»Identity Groups
Vault’s Identity system also contains the ability to manage organizations of entities in groups. Groups can be internal groups, which are managed directly within Vault, or external groups, which are sourced from external identity providers. At authentication time, external group information for a user is returned to Vault, which can automatically categorize users into appropriate groups within Vault’s Identity system.
Similarly to entities, groups can be used to assign policies and metadata. Groups can contain direct entity members, and can also contain other groups. This allows for major enhancements to automation by using Identity Groups to quickly and easily grant access to secrets and functionality within Vault.
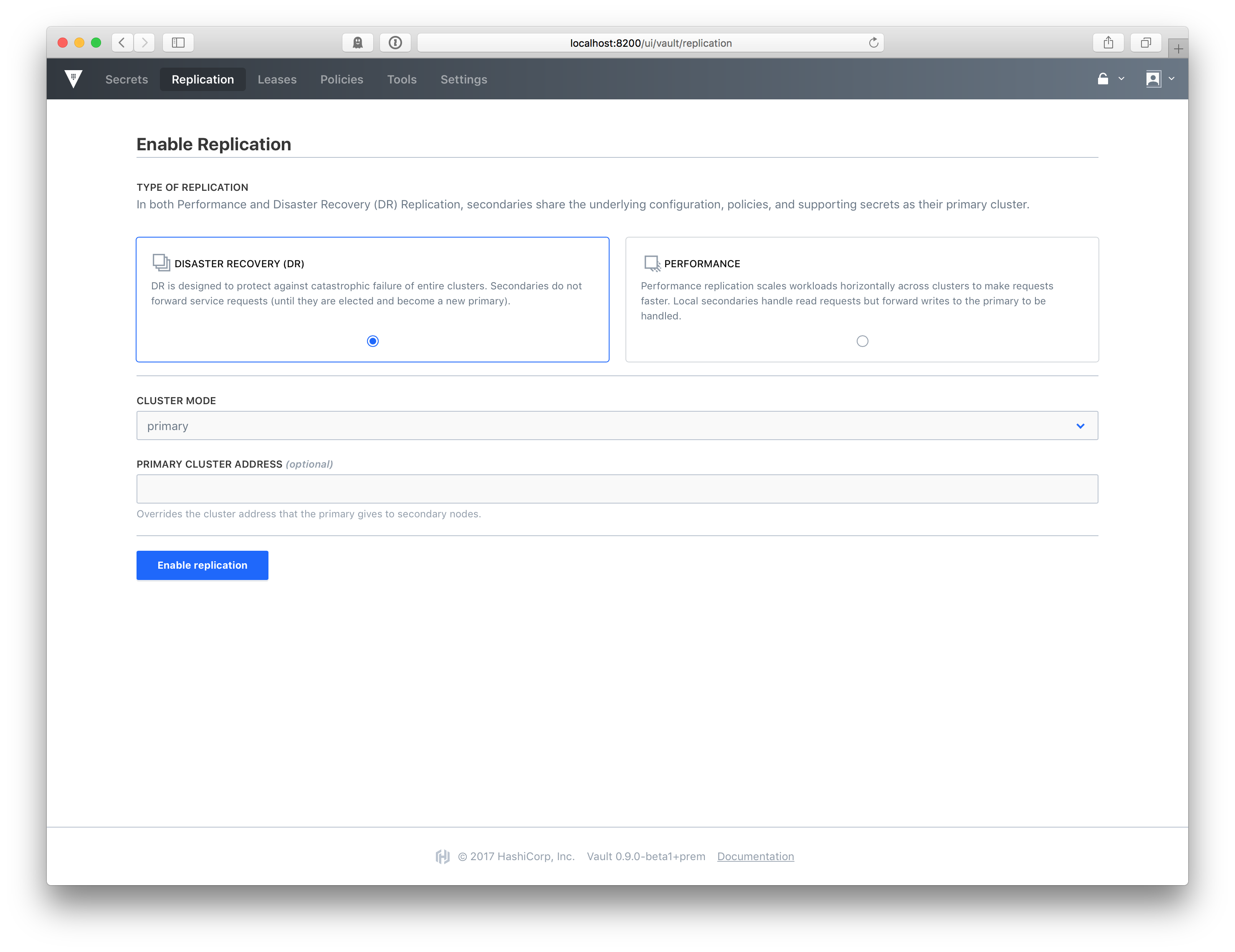
»New Vault UI
 **(Note: this is a Vault Enterprise Pro Feature)**
**(Note: this is a Vault Enterprise Pro Feature)**
Vault 0.9 introduces a new user experience for Vault Enterprise Pro and Vault Enterprise Premium users to manage their cluster environments primarily from a graphical user interface. Vault Enterprise’s new user experience is focused on bringing Vault into alignment with the design language of other HashiCorp Enterprise products, allowing operators using Vault Enterprise to have a have a similar experience when using other products such as Terraform Enterprise.
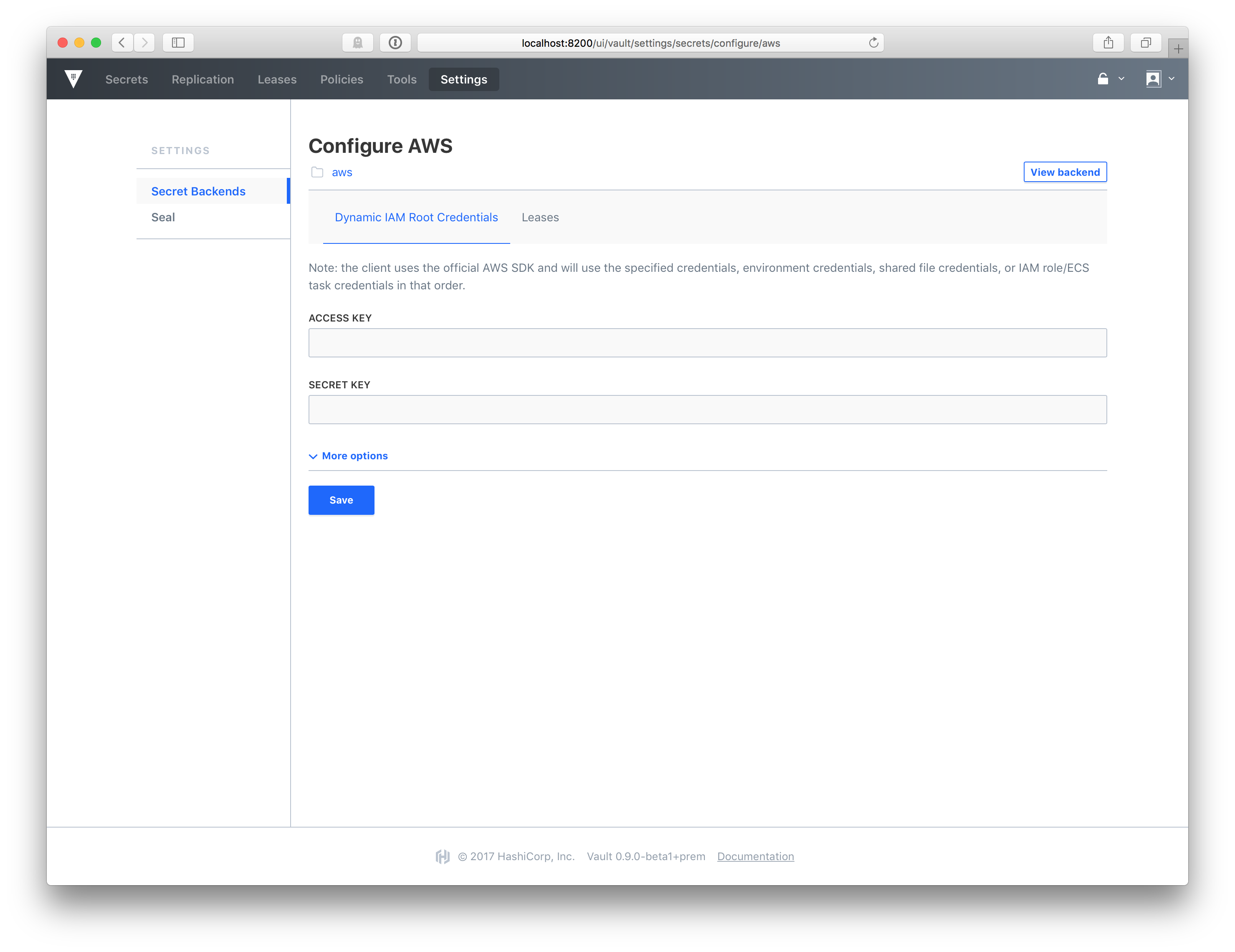
The new Vault UI also expands on the functionality seen in previous versions of Vault Enterprise. In Vault 0.9, users can also engage in common workflows for secrets management including configuring backends such as the AWS IAM secret backend completely within the GUI.
»Cloud Auto-Unseal
(Note: this is a Vault Enterprise Pro Feature)
Vault 0.9 introduces new forms of Auto-Unseal functionality. Previously, Vault Enterprise Premium clusters could automatically unseal themselves when coupled to a Hardware Security Module (HSM). With the new functionality, available in both Vault Enterprise Pro and Vault Enterprise Premium, Vault systems can now integrate with cloud-based key management systems to automate the process of unsealing a Vault cluster. This streamlines the unseal process for Vault and enables the root of trust for Vault to be distributed across other highly secure systems.
In Vault 0.9, Vault Enterprise supports Auto-Unsealing on AWS KMS and GCP Cloud KMS. We will continue to iterate on Cloud Auto-unseal in future releases with supporting cloud environments such as Microsoft Azure via Azure Key Vault.
»Seal Wrap / FIPS 140-2 Compliance
Note: this is a Vault Enterprise Premium Feature
Seal Wrap is new functionality within Vault Enterprise Premium that allows Vault to encode Critical Security Parameters (CSPs) with encryption derived from external modules. These external cryptographic modules are derived from sources that Vault can Auto-Unseal from, including AWS KMS and GCP Cloud KMS; as a result, seal wrapping is available whenever Auto-Unseal is enabled.
Seal Wrap allows operators to reinforce Vault’s encryption with specific cryptography necessary for government and regulatory compliance - in particular the US FIPS 140-2 standard.
Using Seal Wrap, Vault Enterprise Premium systems can comply with the FIPS 140-2 standards for Key Transport (FIPS 140-2 IG 7.16) and Key Storage (FIPS 140-2 IG D.9) at a Security Level equal to the cryptography of the external module. For example, when using a FIPS 140-2 Security Level 3 Module within a HSM, Seal Wrap will ensure that cryptographic fundamentals within Vault will be protected at Security Level 3.
Seal Wrap has been evaluated for FIPS 140-2 compliance by Leidos, a major defense and security research lab. See Vault Compliance Letter for more details.
For more information on Seal Wrap, see HashiCorp Vault Completes FIPS 140-2 Evaluation press release.
»Control Groups
Note: this is a Vault Enterprise Premium Feature
Control Groups allow a given request within Vault to require authorization from one or more Identity group members acting as “gatekeepers”. This authorization requirement can be applied to nearly any Vault request, whether for generating dynamic secrets or changing Vault configuration. For example, a policy can be set to require any request for production Postgres credentials to be approved by members of the "DBA Admin" Identity group.
Control Groups are designed to help Vault Enterprise systems store data in conformance with regulations like the European Union GDPR or HIPAA that require multiple authorizers for accessing certain types of sensitive information.
For more information on Control Groups, see control groups documentation.
»Sentinel Integration
Note: this is a Vault Enterprise Premium Feature
Vault 0.9 adds integration with Sentinel, HashiCorp’s policy-as-code framework.
Vault Enterprise Premium supports two types of Sentinel policies for managing access to Vault secrets and functionality. Role Granting Policies (or RGPs) focus on how specific Identities or Identity Groups access secrets. Endpoint Granting Policies (or EGPs) focus on managing access to specific API endpoints, including unauthenticated paths such as login paths.
Through RGPs and EGPs, operators can create and enforce powerful Sentinel policies for brokering access to secrets within Vault. For example, a policy could be created to require that Entities within a specific Identity group must connect via corporate internal IP addresses and pass through Multi-Factor Authentication when attempting to access secrets within Vault.
For more information on Sentinel’s integration within Vault, see:Sentinel with Vault documentation
»Other Features
There are many new features in Vault 0.9 that have been developed over the course of the 0.8.x releases. We have summarized a few of the larger features below, and as always consult the Changelog for full details.
- RSA support in Transit Backend - Supports using RSA keys for encrypting and signing data via Vault’s transit backend.
- Kubernetes Auth Backend - Integrates Vault with Kubernetes to deliver access tokens to pods.
- Lazy Lease Loading - Drastically reduces the time required to start Vault or have a new HA node take active duty by asynchronously loading existing token and secret leases.
- PKI Backend Enhancements - Vault’s PKI backend can now sign self-issued certificates to support some CA rotation workflows.
- Google IAM Authentication Backend - Supports authenticating to Vault via GCP’s IAM system.
- Oracle Database Backend - Support managing and creating dynamic database credentials for Oracle databases.
- Ping Identity MFA (Enterprise Only) - Support the use of Ping Identity for MFA within Vault’s API.
»Upgrade Details
Vault 0.9 introduces significant new functionality. As such, we provide both general upgrade instructions, a Vault 0.9-specific upgrade page.
As always, we recommend upgrading and testing this release in an isolated environment. If you experience any issues, please report them on the Vault GitHub issue trackeror post to the Vault mailing list.
For more information about HashiCorp Vault Enterprise, go to https://www.hashicorp.com/products/vault. Users can download the open source version of Vault at Vault downloads.
We hope you enjoy Vault 0.9