HashiCorp Terraform provides practitioners a simple way to define and manage their infrastructure as code, as part of a broader application or infrastructure pipeline, or via automated processes. This model has helped many of you improve repeatability, reduce failures, and increase provisioning speed. But, as all of these code objects are created and need to be managed, one capability of Terraform Cloud that’s often overlooked is its native integration with many popular Version Control Systems (VCS).
It’s always been HashiCorp’s position that the best way to provision infrastructure is to store your infrastructure as code (IaC) configuration files in a VCS repository and use Terraform to create resources based on them. This process typically has three steps:
- Write infrastructure as code
- Manage configuration files in VCS
- Automate infrastructure provisioning
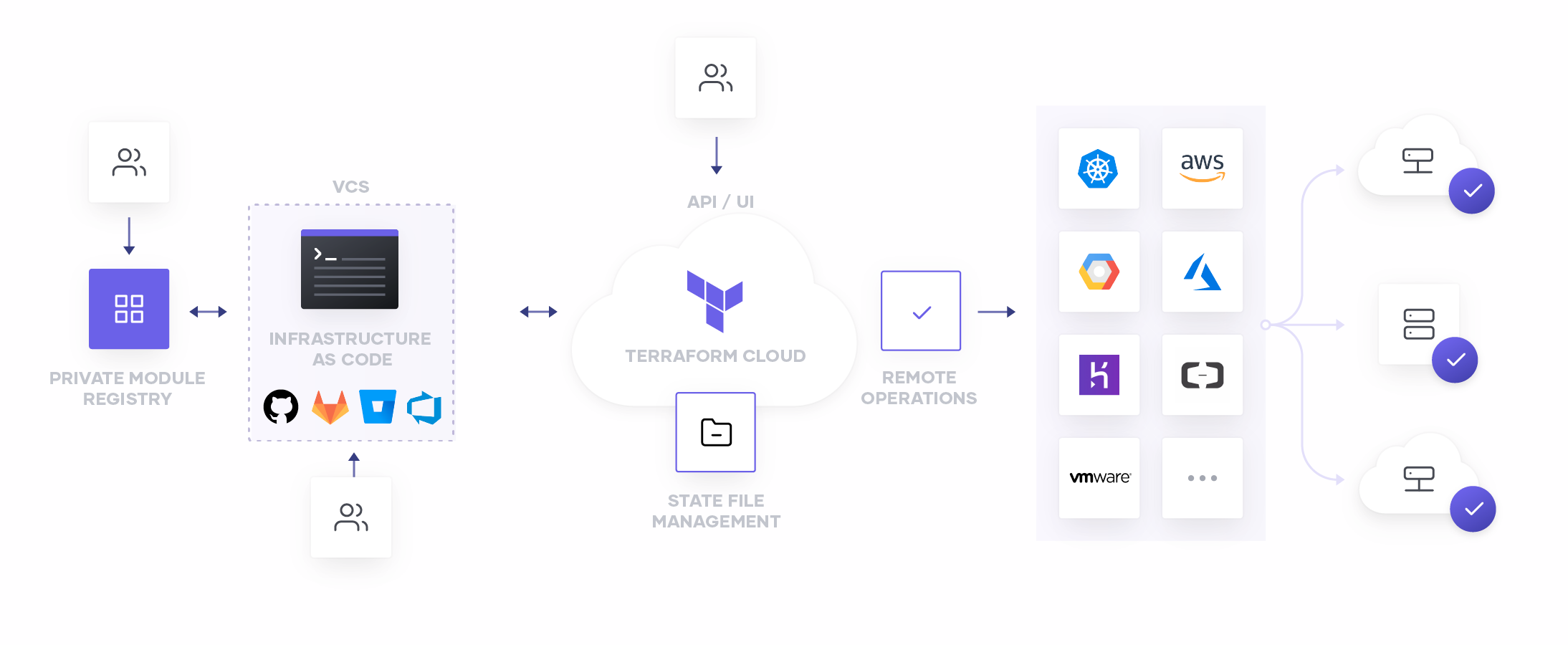
»Why Version Control System Integration?
Terraform Cloud can integrate directly to popular on-premises and SaaS distributions of GitHub, GitLab, Atlassian BitBucket, and Azure DevOps. This integration provides a streamlined and seamless workflow for practitioners to store and manage their code directly in the VCS of their choice, while bringing a new level of automated functionality to their process.
Linking your Terraform Cloud workspace to a VCS repository automatically establishes a connection which notifies Terraform Cloud of any commits, pull requests, and merges to your repository. This notification can invoke automated plans that show you the potential impact of your changes, or can even begin a deployment to ensure that your running infrastructure always represents the most current declared state of your code.
Once you’ve established the integration between your Terraform Cloud workspace and your VCS repository, Terraform will be notified any time the repository sees committed code, and will automatically produce a speculative plan. These speculative plans present as integrated checks, let you see at a glance exactly what will happen if you merge the request, as well as what, if any, policy violations may have occurred. All this without any risk to your existing infrastructure!
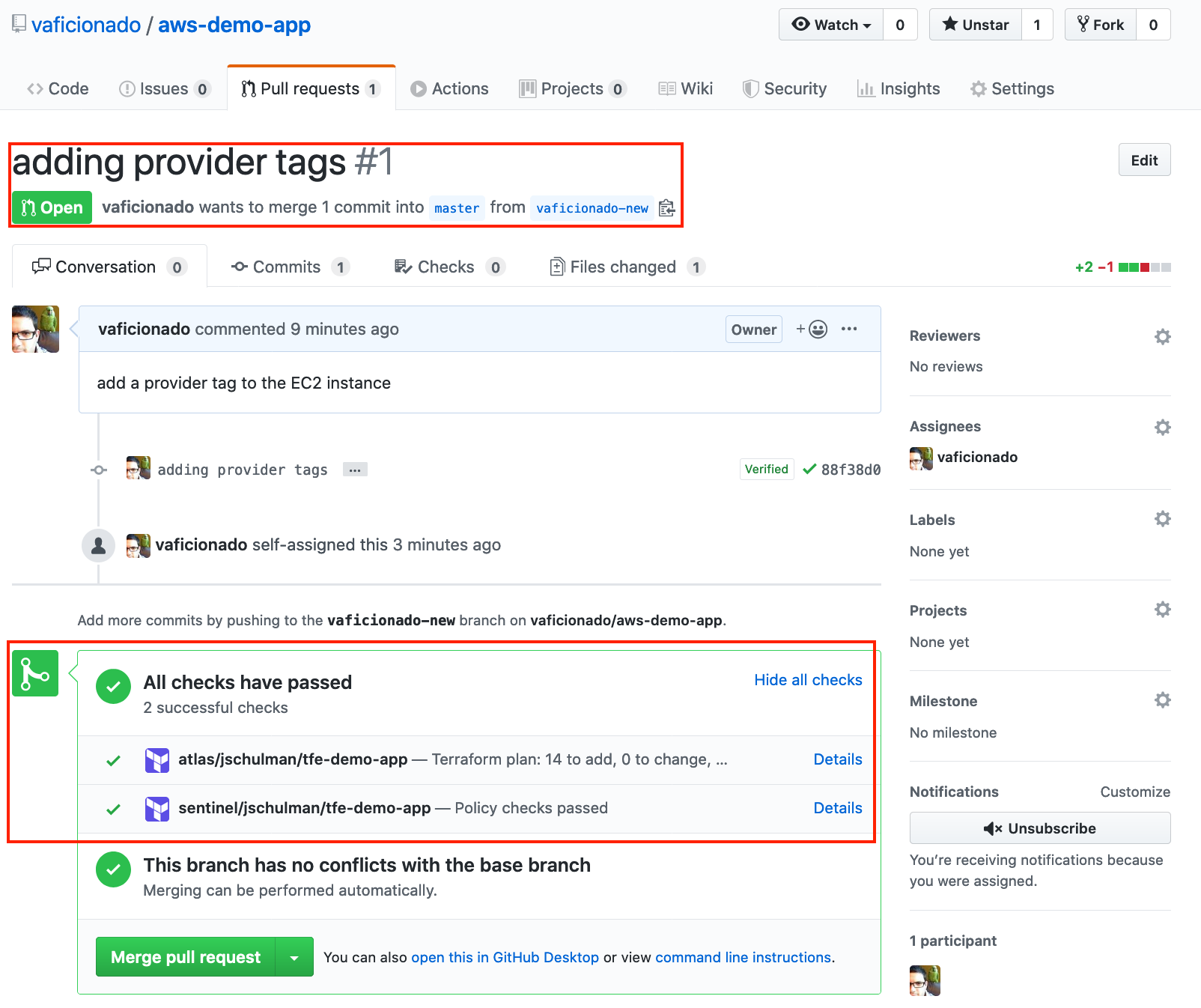
Here you can see a simple pull request into a GitHub repository containing Terraform configurations. Because this repo is linked to the `tfe-demo-app` workspace in Terraform Cloud, the speculative plan and Sentinel policy checks were automatically run, and the results returned directly to the PR. Both passed, so there’s not much reason to dig deeper—but you always can if the situation calls for it.
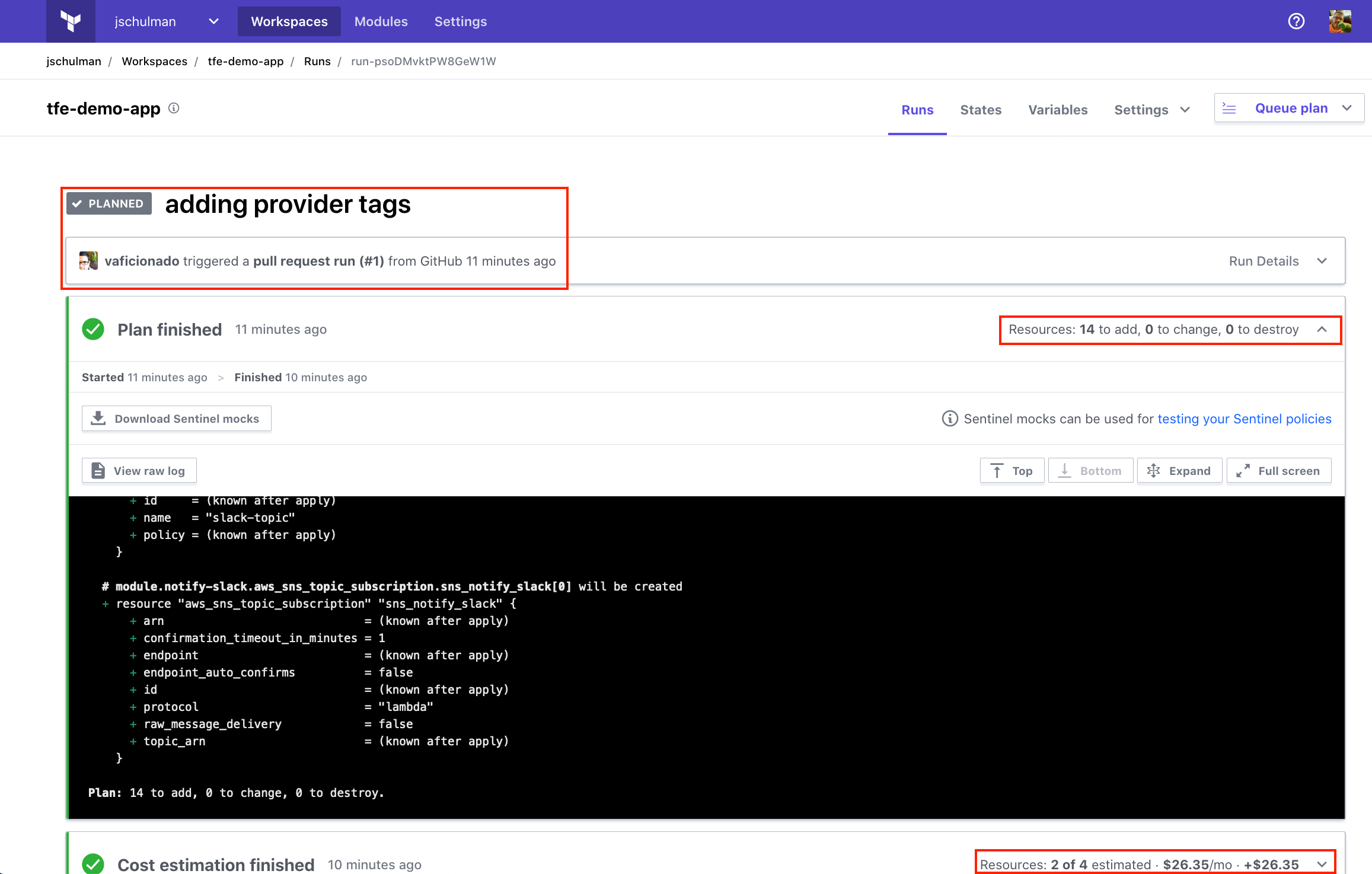
Clicking on the **Details** link in the check will bring you directly into your Terraform Cloud workspace, where you can see the details of your plan; including any changes to provisioned resources, estimated cost changes should the plan be applied, policy violations, and more.
For a video of this in action, see our previous blog post highlighting the integration between Terraform Cloud and Azure DevOps.
»Getting Started
To get started, sign up for a free Terraform Cloud account. Or to learn more, head over to our documentation for details on how to link your specific VCS provider, or visit the HashiCorp Learn platform and see Terraform in action today!








