As cloud platform teams seek to scale their infrastructure provisioning capabilities across their organization, enabling self-service becomes a key driver of efficiency. But self-service introduces new challenges for security, compliance, and reliability. HashiCorp Terraform Enterprise, the self-hosted distribution of Terraform Cloud, has added new features to address these challenges, including:
- Vault-backed dynamic credentials
- No-code provisioning workflow
- Support for Terraform 1.5’s new config-driven import
- Continuous validation of infrastructure health
This post reviews these major new enhancements from the last few HashiCorp Terraform releases.
»Vault-backed dynamic credentials
A secure self-service workflow starts with secure handling of sensitive cloud credentials. Added to Terraform Enterprise in v202303-1, dynamic provider credentials generates short-lived just-in-time credentials for the Amazon Web Services (AWS), Microsoft Azure, Google Cloud, and HashiCorp Vault providers using an OpenID Connect (OIDC) workflow.
New in v202305-1, Vault-backed dynamic credentials extends this functionality to support the Vault dynamic secrets engines for AWS, Azure, and Google Cloud. This approach provides a consolidated workflow using Vault for all your secrets management and centralized auditing needs, eliminating the risks and operational overhead of managing static credentials. Learn more about the benefits of this feature in the original Terraform Cloud adds Vault-backed dynamic credentials announcement blog.
As an added benefit specific to Terraform Enterprise, no inbound access to the Terraform Enterprise instance is required from cloud providers to validate the OIDC metadata. Only the Vault instance needs direct access to Terraform Enterprise. Interactions between Vault and the cloud provider are done using outbound API calls. This gives you all the benefits of dynamic credentials without additional exposure for Terraform Enterprise instances hosted in private networks.
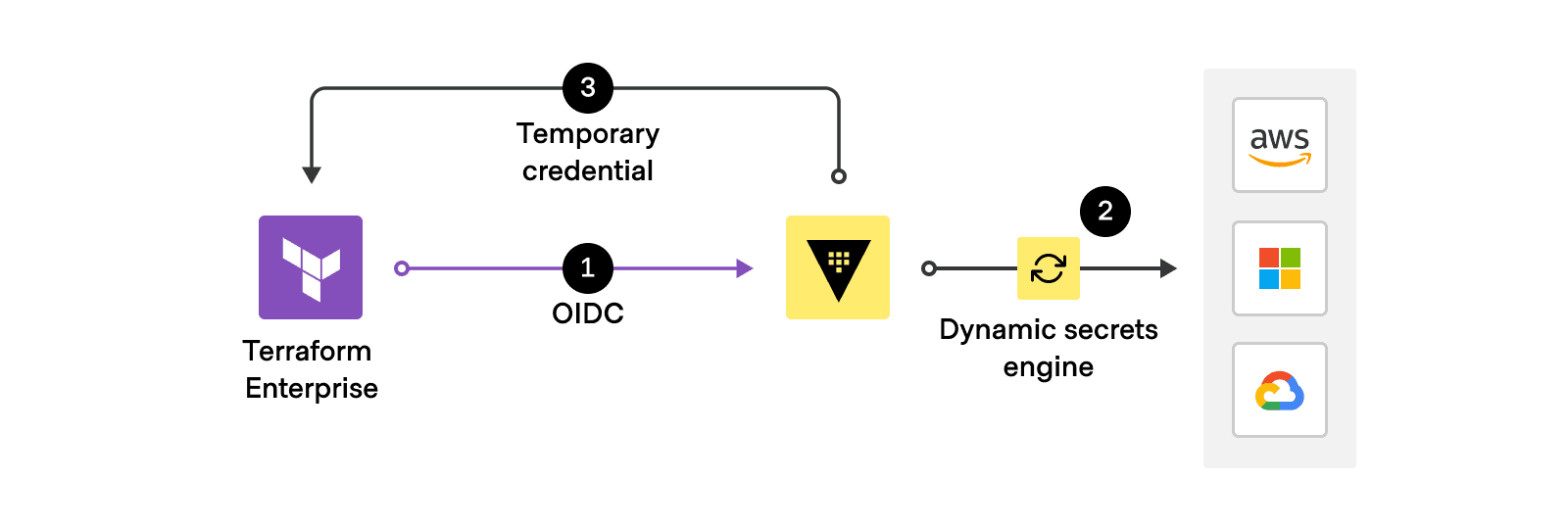
Automatically generate short-lived credentials for Terraform Enterprise runs.
»No-code provisioning
Our 2023 State of Cloud Strategy survey showed that, for the third year in a row, skills shortages are a top challenge to cloud adoption. The no-code provisioning workflow, now generally available in Terraform Enterprise v202306-1, allows platform teams to enable self-service for users without requiring specific Terraform or HashiCorp Configuration Language (HCL) skills. Authors enable their modules for no-code provisioning so end users can provision infrastructure without writing any Terraform code. Module authors can also define the allowed values for input variables, reducing the friction of failed deployments due to invalid inputs and typos.
Learn more about designing and provisioning no-code modules in the Terraform Enterprise documentation, and check out the demo video:
No-code provisioning includes guardrails to reduce frustrating misconfigurations.
Find out how no-code provisioning and Vault-backed dynamic credentials work together with our new tutorial: Enable self-service workflows with Vault-backed dynamic credentials.
»Config-driven import with Terraform 1.5
Released in June, Terraform 1.5 introduced a new and improved workflow to bring existing infrastructure under management — config-driven import. We’ve already heard great feedback on this new approach from many customers, and as of the July (v202307-1) release, this workflow is supported in Terraform Enterprise for a secure, unified experience. Resources to be imported are shown in the plan and apply output along with the auto-generated code. This means config-driven import can be used as part of VCS and CLI-driven workflows, which was not possible with the old terraform import command.
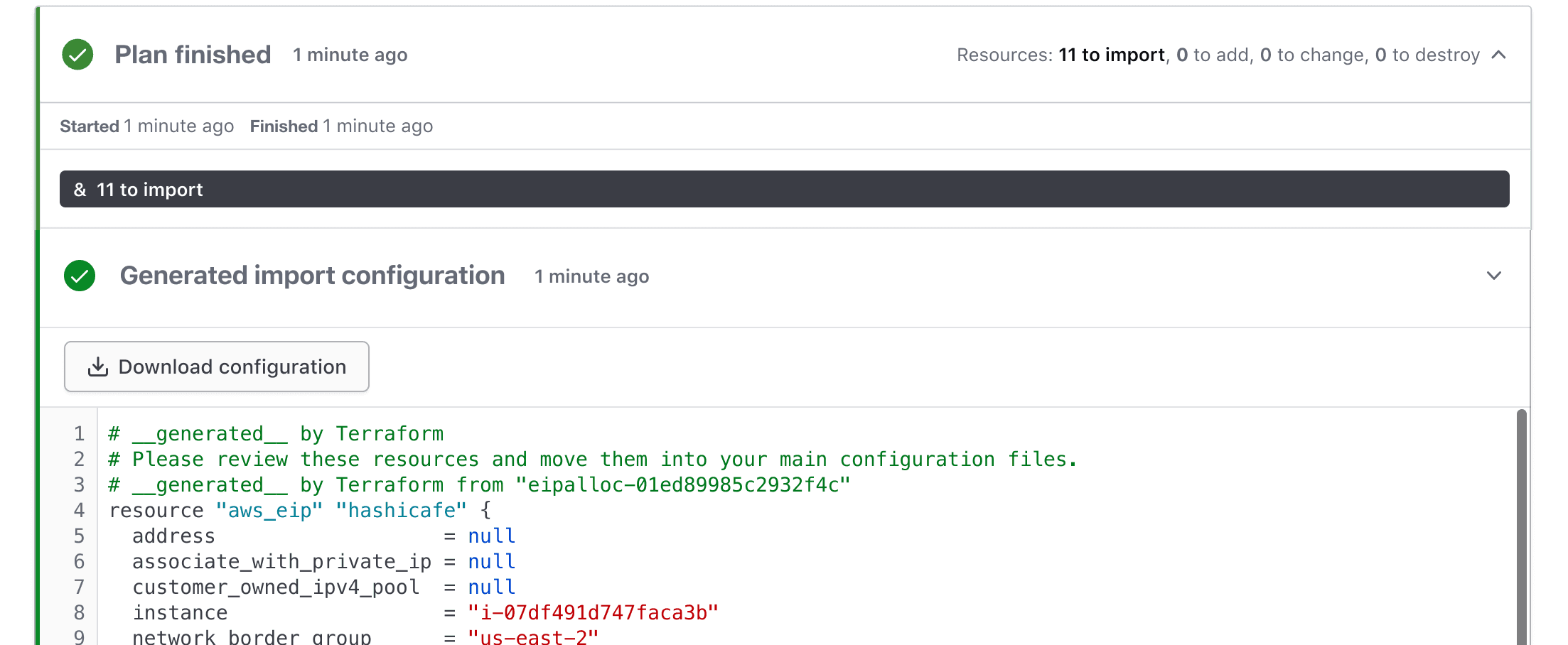
Bulk import of resources with automatic code generation
»Continuous validation
Once you’ve provisioned (or imported) infrastructure, how do you ensure it remains healthy on Day 2 and beyond? Continuous validation, part of Terraform Enterprise v202307-1, provides automated health checks using assertions defined in your Terraform code so that your infrastructure works as expected over the long term. Customizable notifications alert infrastructure owners as soon as a check fails, helping you avoid costly downtime due to preventable issues such as expiring certificates or security issues from outdated images and newly discovered vulnerabilities.
Continuous validation works with the new check blocks introduced in Terraform 1.5. Checks are ideal for post-apply continuous validation because of their flexibility as a top-level construct, and they are well suited for holistic functional validations across your entire configuration. Along with drift detection, conditions and checks are evaluated on an ongoing basis via automatic health assessment runs. The assessment interval can be customized by the Terraform Enterprise administrator.
For more continuous validation examples, read our recent blog post about 8 Terraform continuous validation use cases for AWS, Google Cloud, and Azure.
»Other enhancements and next steps
Along with these major new features, Terraform Enterprise also now supports assignment of variable sets at the project level, a new Sentinel policy review UI, and the ability to set a lifetime for user, team, and organization API tokens. And version 1.9 of Terraform Cloud agents added support for writing to environment variables from agent hooks, broadening the capabilities of custom agent images.
Customers should note that June (v202306-1) marked the removal of the legacy run pipeline mode, which was first deprecated in February (v202302-1). If your environment is using a custom worker image, you must transition to a new custom agent image before moving to the v202306-1 release. To find out more about this migration, refer to the custom agent image migration guide. This migration guide has been updated to include the environment variable enhancement released in tfc-agent 1.9.
For more information about the latest releases of Terraform Enterprise, review the release notes in the Terraform Enterprise documentation. For more information about Terraform Enterprise or to get started, visit the Terraform product page or contact HashiCorp sales.








