In March 2023, we announced the general availability of dynamic provider credentials in Terraform Cloud. This native support lets users authenticate to providers using short-lived, just-in-time credentials in their Terraform Cloud workflows with the Amazon Web Services (AWS), Microsoft Azure, Google Cloud, and HashiCorp Vault providers. The enhancement helps users reduce the risk of exposure from storing long-lived static credentials and avoid the burden of manual secret rotation. Today we are excited to announce the general availability of dynamic provider credentials support for Kubernetes via Amazon Elastic Kubernetes Service (EKS) and Google Kubernetes Engine (GKE).
»Dynamic provider credentials for Kubernetes
Previously, users managing Kubernetes resources with Terraform often authenticated to clusters using long-lived, non-renewable static credentials. This approach frequently resulted in authentication failures upon expiration. Now Terraform offers Kubernetes users the ability to utilize the workload identity of Terraform Cloud integrated with the native OIDC support of EKS and GKE.
Dynamic provider credentials in Terraform Cloud eliminate the risks associated with storing long-lived credentials, removing the operational burdens of manually rotating them.
»How it works
Dynamic provider credentials are based on the industry-standard OpenID Connect (OIDC) workload identity authentication flow. With today’s enhancement, Terraform Cloud now supports just-in-time authentication for the official Kubernetes and Helm providers.
Once the OIDC trust relationship has been established, Kubernetes cluster roles are mapped to Terraform workloads by the platform team, rather than providing long-lived, static credentials to be shared across the organization. When a Terraform workload is executed, Terraform Cloud will automatically handle the necessary handshake with the target cluster and inject short-lived credentials directly into the Terraform execution environment.
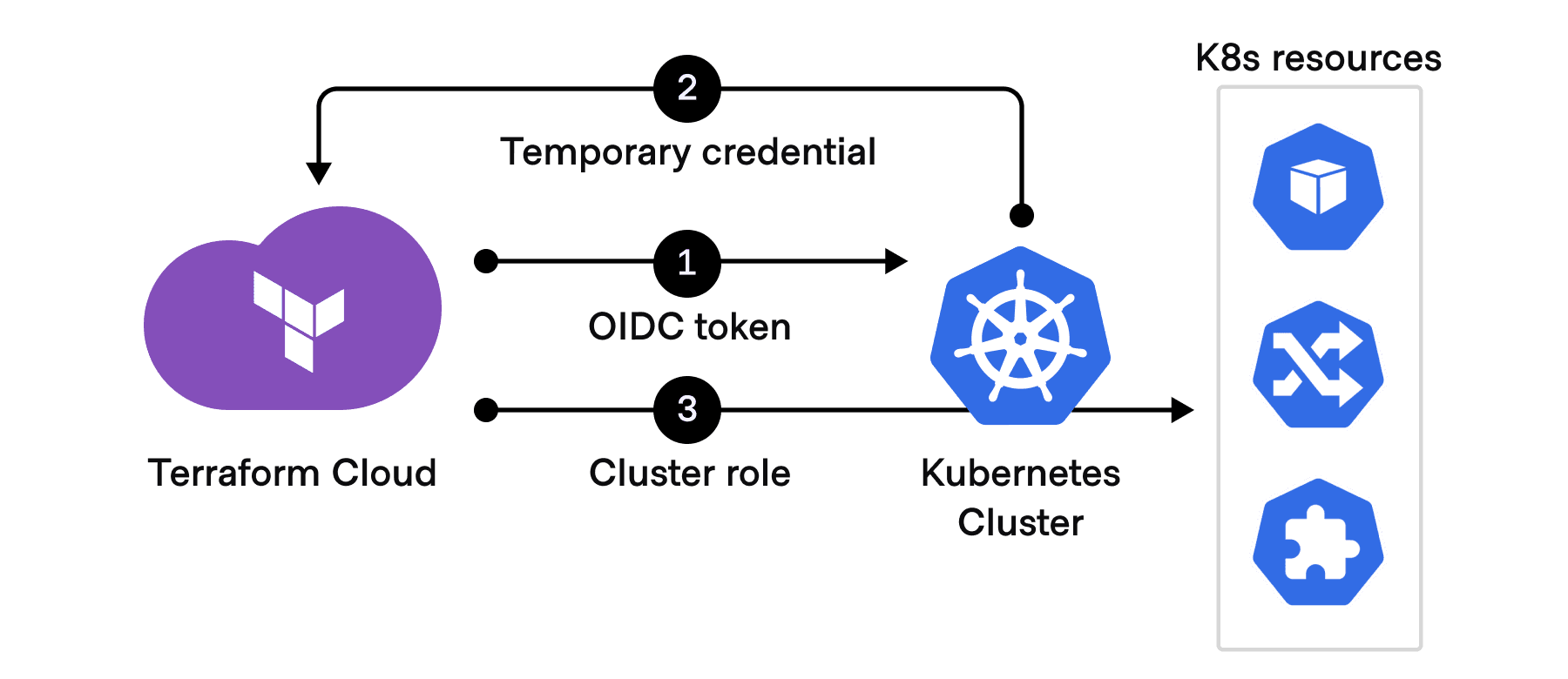
Using an industry-standard OIDC workflow, a temporary credential is automatically generated for each Terraform Cloud run.
»Key benefits
Dynamic provider credentials can now authenticate Kubernetes for EKS and GKE. That brings two main benefits:
- Increase Agility: Previously platform teams using the Kubernetes and Helm providers with EKS or GKE had to manage long-lived credentials to connect Terraform Cloud, requiring custom solutions and processes. Now teams can take advantage of native, dynamic creation of auth tokens and benefit from the reduction of operational complexity when managing provider credentials. Platform teams can enable self-service for end users without compromising security or compliance.
- Reduce risk: Platform teams storing long-lived credentials are exposed to security risks. The use of short-lived dynamic credentials reduces the risk of accidental credential exposure and re-use. Dynamic provider credentials allow cloud platforms to scope privileges down to the individual workspace level. This control gives users additional customization and enables the least privilege principle.
»Getting started with dynamic provider credentials
Dynamic provider credentials help organizations mitigate the security risks of storing long-lived credentials and avoid the operational burdens of manually rotating them. This helps simplify Terraform Cloud setup and ensures secure authentication across cloud environments.
To learn more about dynamic provider credentials for Kubernetes, please refer to Dynamic provider credentials documentation. If you are completely new to Terraform, sign up for Terraform Cloud and get started using the Free offering today.








