As quantum computers grow in power and reliability, we at HashiCorp have been asked a number of questions about how we plan on protecting Vault against quantum threats.
Quantum computing has the potential to seriously change how we think about cryptographic security. By exploiting quantum mechanics such as entanglement and quantum parallelism, quantum computers can run cryptanalysis algorithms capable of simplifying the math protecting many popular forms of encryption.
With modern computing power, attacking RSA 2048 using a number sieve should take a few orders of magnitude longer than the expected lifetime of our galaxy. With a sufficiently powerful quantum computer, we can expect to break the same encryption in roughly thirty minutes.
Publicly known quantum computers at the time of this writing are incapable of attacking modern cryptography with quantum cryptanalysis; modern publicized quantum computers are about two orders of magnitude less powerful than the above machine. But rapid advances in photonic physics and error correction are allowing us to advance the power of quantum computers at a doubly exponential rate - several orders of magnitude faster than how digital computers have evolved under Moore’s Law.
This rapid acceleration of quantum computing technology ensures that if one intends on protecting secrets for the future they must begin to think about quantum threats today. And for the last few years the Vault team has quietly been doing just that.
»Community Efforts Around Quantum Security
Since 2016 the National Institute of Standards and Technology (NIST) has led the Post Quantum Cryptographic Standardization Process (PQCSP). PQCSP’s goal is to review and endorse new algorithms resilient against known quantum cryptanalysis, and stop endorsing algorithms known to be vulnerable against quantum threats. The cryptographic community has rallied around these efforts and many security vendors are preparing to implement the output of PQCSP to protect their products against advanced adversaries in the future.
We on the Vault team have been closely following NIST’s efforts on post-quantum security since the process’ inception and plan on implementing guidance from NIST before draft changes to NIST SP800 documents (and correspondingly regulations such as FIPS 140-2) are introduced in 2022-2024.
But not all Vault users follow NIST’s guidelines or FIPS 140-2. Vault is a global project, and both Vault and Vault Enterprise are currently used to protect secrets across the world - even in low earth orbit! As such, we deal with quantum security holistically in Vault during the design and development of each release.
»Quantum Security in Vault
When we introduce features in Vault that have implications on Vault’s security or involve cryptography, we also review whether this change exposes Vault to known quantum cryptanalysis. In particular we consider two quantum algorithms: Shor’s Algorithm and Grover’s Algorithm.
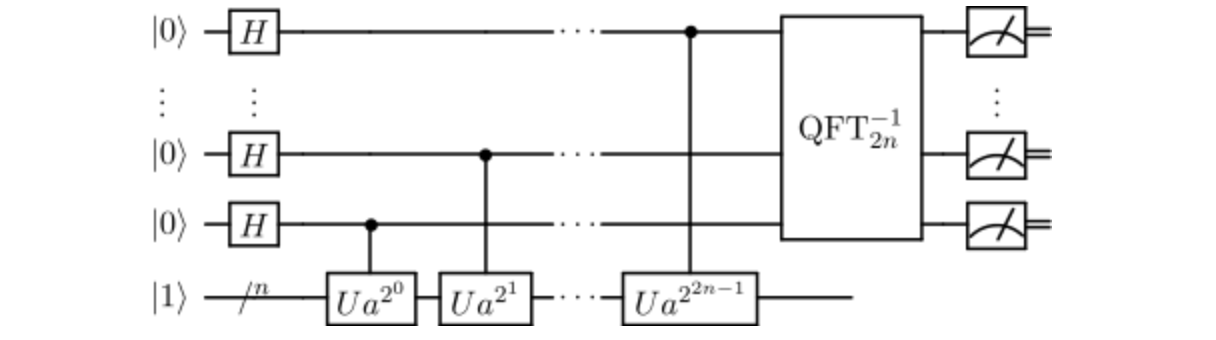
Shor’s Algorithm (or simply Shor’s) exploits quantum mechanics to dramatically reduce the difficulty of factoring large prime numbers via the use of a Quantum Fourier Transform. Shor’s reduces the computational difficulty of this task such that algorithms who rely on the difficulty of factoring prime numbers - for example ciphers such as RSA and Diffie Hellman - are vulnerable to attack by sufficiently powerful quantum computers.
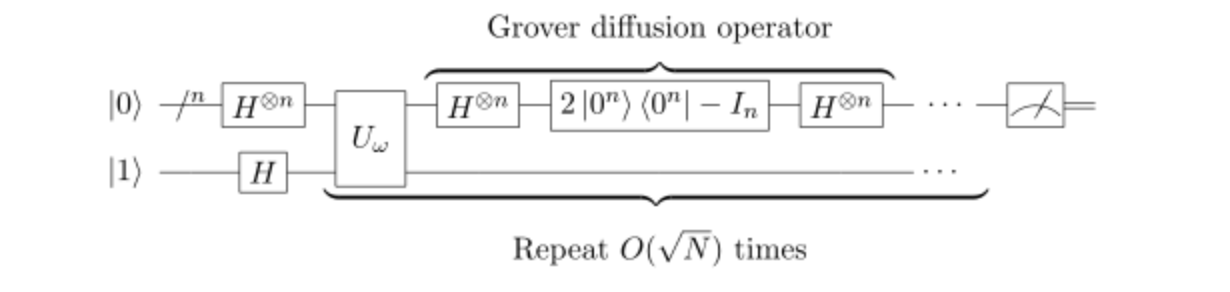
Grover’s Algorithm (or simply Grover’s) exploits quantum parallelism to quickly search for the statistically-probable input value of a black-boxed operation. Grover’s does not yield attacks that invalidate whole fields of encryption like Shor’s. But it does reduce the difficulty of intelligently searching for the keys of symmetric key encryption via brute force search.
When implementing new cryptography in Vault, and reviewing the cryptography protecting existing critical security parameters in Vault, we review whether Shor’s and Grover’s algorithms have implications on that cryptography’s security against adversaries armed with sufficiently-powerful quantum computers.
»Post-Quantum Cryptography in Vault
Quantum computing is not always destructive to security. There are a number of new (and in some cases renovated) ciphers and cryptographic techniques being introduced to deal with threats powered by quantum computers. When peer reviewed implementations of this cryptography are available, we look to support them in Vault.
An example of this is the chacha20-poly1305 cipher. Chacha20-poly1305 is a stream cipher that was introduced as an alternative to AES to deal with future cryptanalytical attacks.
Grover’s presents the possibility that future quantum computers may be able to attack symmetric key cryptography, thereby reducing the difficulty of breaking some modes of AES roughly by half. In response, chacha20-poly1305 has begun to be endorsed as an alternative in the face of future quantum cryptanalysis.
We have been tracking this conversation about AES and chacha20-poly1305 for several years. Since Vault 0.9.4 (2018), we have supported chacha20-poly1305 within the Transit secret engine. This allows Vault users to use chacha20-poly1305 for all transit encrypt/decrypt operations, including with convergent encryption and with key derivation.
We have also implemented mechanisms in Vault to handle seals-migration. While ostensibly this is to support the migration from Shamir’s Key Shares to different forms of auto-unseal, we respect that this may be used in the future to allow Vault to comprise its cryptographic barrier keys with future post-quantum cryptography.
Our implementation of AES 256-GCM, which we use to comprise the cryptographic barrier for Vault’s data at rest, is resistant against most known quantum attacks. But we respect that this may change in the decades to come as quantum computing enters more into the mainstream.
»Post-Quantum Key Distribution and Entropy Protection
Quantum computing presents a number of interesting new technologies for augmenting system security. Techniques such as Quantum Key Distribution (QKD) allow for quantum entanglement and superposition to provide mechanisms for securely distributing cryptographic keys over large distances in a way that highlights attempts to tamper or eavesdrop with that communication.
While implementations of QKD exist - most notably the Chinese "Micius" QKD satellite - implementing QKD for protecting commercial data is currently untenable. Still, we have the capabilities today in Vault to adopt implementations of QKD for auto-unseal and transit when they become available in the future.
What is available in modern quantum computers is lots of random data or entropy. Even today’s limited qubit quantum computers generate extremely random sets of entropy in normal operation. This entropy is extremely valuable in cryptography as operations such as key generation for symmetric key crypto like AES or generating ephemeral session keys for SSH/TLS require robust entropy sources for random number generation.
In upcoming versions of Vault Enterprise we will release features that allow Vault to sample entropy from external sources. Some of these external sources will include quantum computing sources, including hardware security modules who employ quantum cryptographic number generators.
»The Road Ahead
Vault’s mission is to secure any kind of information for any kind of infrastructure. As quantum computing becomes part of the infrastructure stack, and quantum threats become part of one’s threat model, we stand ready to adopt new technology in support of our ongoing mission.








