Today, at HashiDays in London, we are detailing recent and upcoming additions to our Security Lifecycle Management (SLM) products: HashiCorp Vault and Boundary. Our SLM solutions use identity-based security workflows and offer a system of record for sensitive information (credentials, certificates, keys, customer data) along with the ability to manage the entire lifecycle of that data. This post explores how our SLM product updates protect sensitive data, inspect your security posture, and securely connect machines and users.
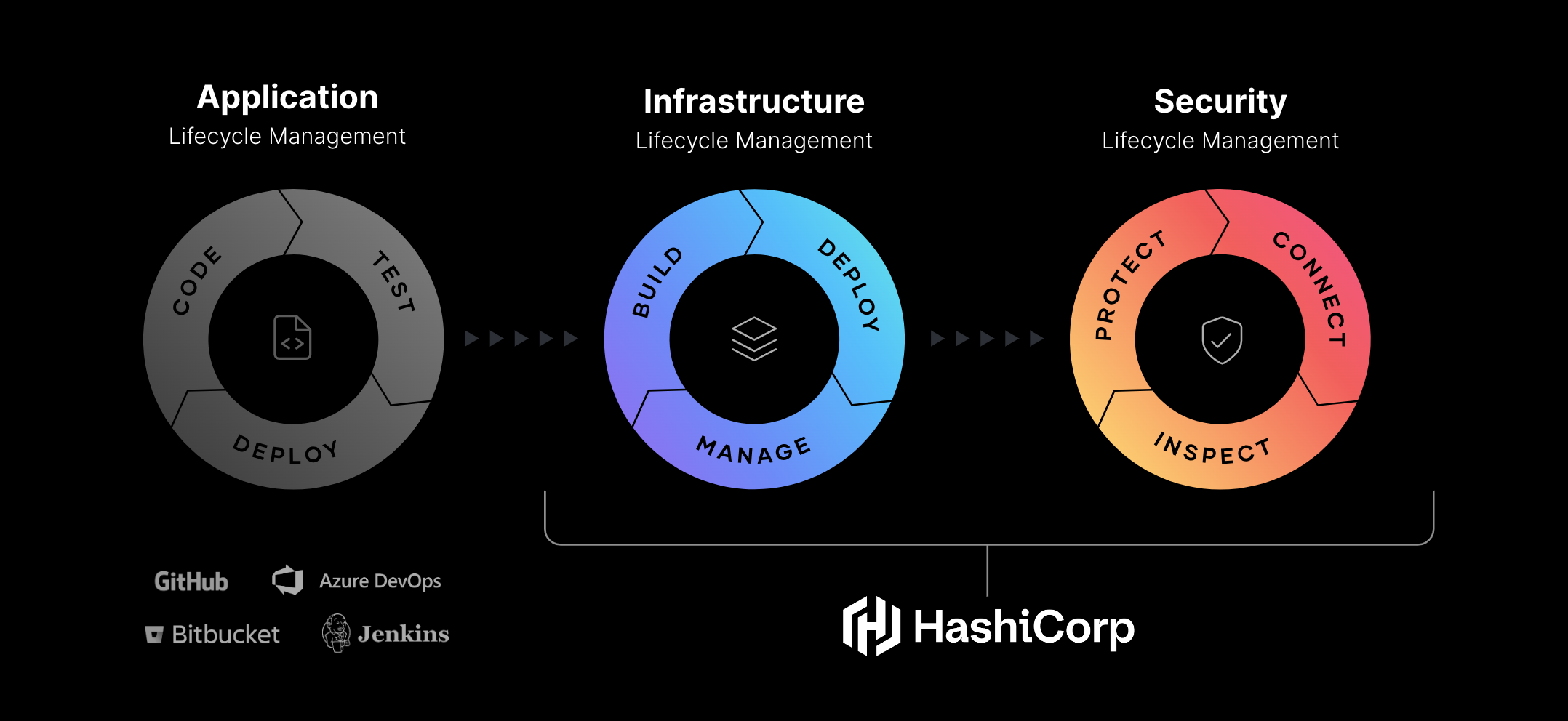
The Infrastructure Cloud from HashiCorp provides Infrastructure and Security Lifecycle Management.
»Protect sensitive data
For organizations to protect their cloud environments, they need a system of record and full lifecycle management for secrets (certificates, passwords, keys, etc.). HashiCorp has announced several enhancements and additions to Vault that do just that:
»Workload Identity Federation
Workload Identity Federation (WIF), coming soon to Vault Enterprise in version 1.17, enables secretless configuration for Vault plugins that integrate with external systems supporting WIF, such as Amazon Web Services, Microsoft Azure, and Google Cloud. By enabling secretless configuration, organizations reduce security concerns that can come with using long-lived and highly privileged security credentials. With WIF, Vault no longer needs access to highly sensitive root credentials for cloud providers, giving operators a solution to the “secret zero” problem.

Workload Identity Federation (WIF) provides a secretless approach to configure Vault plugins.
»Secrets Sync
Secrets sync recently became generally available in Vault Enterprise and it helps organizations manage secret sprawl by centralizing the governance and control of secrets from other secrets managers into Vault as a central system of record. Secrets sync can synchronize updates to AWS Secrets Manager, Google Cloud Secrets Manager, Microsoft Azure Key Vault, GitHub Actions, and Vercel. This helps organizations running a multi-cloud environment consolidate siloed secret visibility, audits, and management into one system, shrinking attack surfaces and streamlining compliance management.
»Vault Secrets Operator
The Vault Secrets Operator (VSO) provides native Kubernetes Secrets integration with Vault. The latest updates support OpenShift OLM and secret templating, which are available now, while instant updates are scheduled to be available in June.
»OpenShift OLM
OpenShift is a widely used container orchestration platform that lets developers build and modernize applications at scale. OpenShift offers a consistent experience across public cloud, on-premises, hybrid cloud, and edge architectures. With this enhancement, VSO on OpenShift can be installed, updated, and managed through the embedded OperatorHub on OpenShift.
»Secret transformation
For applications that require precisely formatted secret data that does not align with what is stored in Vault, VSO can now transform the raw secret data into a form compatible with their application using templating, reducing custom code and complication for developers. For example, see the code snippet below that generates database-access URLs from a secret field:
spec:
destination:
transformation:
excludes:
- .*
templates:
url:
text: |
{{- $host := get .Annotations "myapp.config/postgres-host" -}}
{{- printif "postgresql://%s:%s@%s/postgres?sslmode=disable"
(get .Secrets "username")
(get .Secrets "password") $host
-}}
labels:
Vds: "true"
Secret transformation lets developers define secret templates within a VSO secret custom resource (CR). Transformations include the ability to render secret data from a Go template and provide inclusion or exclusion data filters. The result of a secret’s transformation is stored in the destination Kubernetes secret. This new feature reduces the amount of code needed to manage and improves performance, lifting the burden of secret transformation from the application developer.
»Instant updates
Due to emergencies or security events, a secret may need to be revoked or rotated before it expires. This could result in downtime because VSO would not be aware that the secret has been changed. With Vault Enterprise 1.17, VSO users will be able to set the instant update flag to avoid this situation. When secrets change in Vault Enterprise, instant updates will notify VSO that relevant secrets have been updated and that it should immediately refresh the secret instead of waiting for its repolling window, minimizing downtime. Instant sync initially supports KVv1 and KVv2 secrets.
»Auto-rotation
Now in beta, auto-rotation for HCP Vault Secrets helps development and security teams auto-rotate their secrets for MongoDB Atlas and Twilio, with more providers on the roadmap. The new feature works by using a two-credential approach to eliminate downtime and ensure a new secret is always available. Authorized users can set schedules for continuous secret rotation or issue an instant rotation from the UI or API. These changes automatically relay to any downstream integrations where the secret has been synced. Auto-rotation addresses the risk that comes with long-lived credentials and manual management of credentials. Plus, manually updating and managing secrets is complex and time-consuming, creating more opportunities for human error leading to security breaches. You can access the secret auto-rotation beta on the HCP portal.
»Certificate automation for EST
Vault PKI now adds support for automating X509 certificates based on enrollment-at-scale requirements using the Enrollment over Secure Transport (EST) protocol. The rapid growth of connected devices and services has increased the attack surface area for enterprises, posing significant risks. Ensuring secure communications between devices and services is critical, but manual or ad hoc certificate lifecycle management is unrealistic at scale and may introduce additional security risks due to human error. Certificate automation within Vault now offers the ability to enroll and secure applications, virtual machines, containers, network components, infrastructure, and internet of things (IoT) devices with PKI EST.
»Inspect your cloud environment for security risks
Organizations can’t protect what they don’t know is vulnerable, so proper inspection of environments to discover unmanaged secrets is crucial. These recent updates from HCP Vault Radar help organizations detect security vulnerabilities and exposed credentials.
»New data sources
HCP Vault Radar continues to meet developers where they are with expanded secret scanning support beyond code environments. While developers may inadvertently introduce secrets into code, they also may add secrets to wiki pages, project planning documents, and support tickets. That’s why we’re introducing scannable data sources beyond GitHub, GitLab, and BitBucket to include Confluence and JIRA (in beta). The expansion of sources supported by HCP Vault Radar helps security teams further reduce risk by identifying and accurately prioritizing secrets in more applications.
»Vault correlation
HCP Vault Radar can integrate with Vault to determine if active secrets have been leaked. It leverages secret stores in Vault to scan supported data sources. Vault is a trusted source of active secrets and therefore more effective than pattern matching alone to discover active secrets that have leaked into code repositories and collaboration platforms. Credentials in Vault are used in critical production environments, so HCP Vault Radar will give exposed secrets a higher severity score and prioritization when they are also found in Vault’s key-value stores.
Additionally, HCP Vault Radar can integrate with AWS Parameter Store to validate active API keys and GitHub to determine valid user access tokens, and also inspect active JSON web-access tokens (JWTs) that have not expired. Vault Radar also uses this information to prioritize its findings.
Use the HCP Vault Radar Events dashboard to see secrets in context and correlate secret scanning results with secrets stored in Vault for remediation.
»Securely connect people to machines based on identity
Enforcing least-privilege access based on trusted identities is a key best practice. Since its inception, Boundary has provided a foundation for modern privileged access management (PAM) with highly automated workflows and identity-driven controls to secure access dynamically. Boundary 0.16 continues to drive a seamless end-user experience and improved governance by adding flexible storage options for session recordings with MinIO, simplified target connections with custom resource aliases, and search and filtering capabilities for admins.
»On-premises storage options for session recordings with MinIO
Support for MinIO as a backend storage option for session recordings gives customers an additional storage option that may better fit their infrastructure requirements.
MinIO is a popular, high-performance, Amazon S3-compatible object store. It’s software-defined, so customers can deploy and run it on any type of infrastructure. The addition of MinIO as a storage backend for Boundary gives organizations in highly regulated industries the flexibility to store recordings in any cloud or on-premises infrastructure. Boundary also provides S3 as a storage option. The MinIO integration is available on Boundary’s HCP Plus and Enterprise tiers.
»Custom resource aliases
As part of our ongoing initiative to drive simplicity, aliases let you use a custom name for target resources. Before the availability of aliases, when using the Boundary CLI to establish a new connection, end users needed to include the target ID of the desired target resource, which required them to know the target ID or look it up with an additional Boundary CLI command.
The new alias feature abstracts the target ID with an alias name that is easier for people to read and remember. This helps users recognize the underlying resource they are trying to access. When users establish new connections to a target using the Boundary CLI, they can type the alias rather than a target ID. Aliases are available across all editions of Boundary.
»Admin UI search and filtering
New search capabilities in the admin UI help Boundary administrators easily locate Boundary resources, such as targets, host catalogs, and IAM objects, when making configuration changes to support infrastructure access needs. We’ve also added support for pagination, which speeds up page loading. The new search and filtering updates are available across all editions of Boundary.
»Get started with Security Lifecycle Management
By leveraging HashiCorp’s Security Lifecycle Management offerings, organizations can trust that their most sensitive data is protected from start to finish. To implement SLM in your organization, sign up for a free HCP account and get started today, or reach out to our sales team to learn more.








