Organizations trying to scale quickly and securely are sometimes forced to choose between productivity and security. This conundrum is especially common when applying policy sets and assigning user permissions. So how can organizations empower users with a self-service model, while also enforcing policies across the organization? Customization is the answer.
Today, we are excited to introduce two new improvements to HashiCorp Terraform Cloud: customizable project permissions and policy assignment, to help organizations scale securely by providing more granular customization options for adherence to internal policies and external regulations. These updates empower teams to manage their infrastructure effectively.
»Customizable project permissions
Back in January, we introduced a new organizational structure in Terraform Cloud called projects, allowing teams to safely self-manage groups of related workspaces with four predefined roles: Admin, Maintain, Write, and Read at the project level. But as organizations look to delegate more responsibility to help their platform teams achieve scale, they need more flexibility to customize permissions, to avoid giving users unnecessary privileges because no predefined role meets their exact needs.
Customizable project permissions for Terraform Cloud Standard and Plus (coming soon to Terraform Enterprise) let organizations tailor project-level permissions, in addition to the predefined roles, to maintain the least-privilege approach and reduce risks.
Administrators can assign teams one of the four predefined roles at a project level, or use the new custom option to pick and choose the appropriate level of permissions to assign out to a team. Examples include workspace permissions, such as the ability to execute runs or view state files that apply to all workspaces in the project.
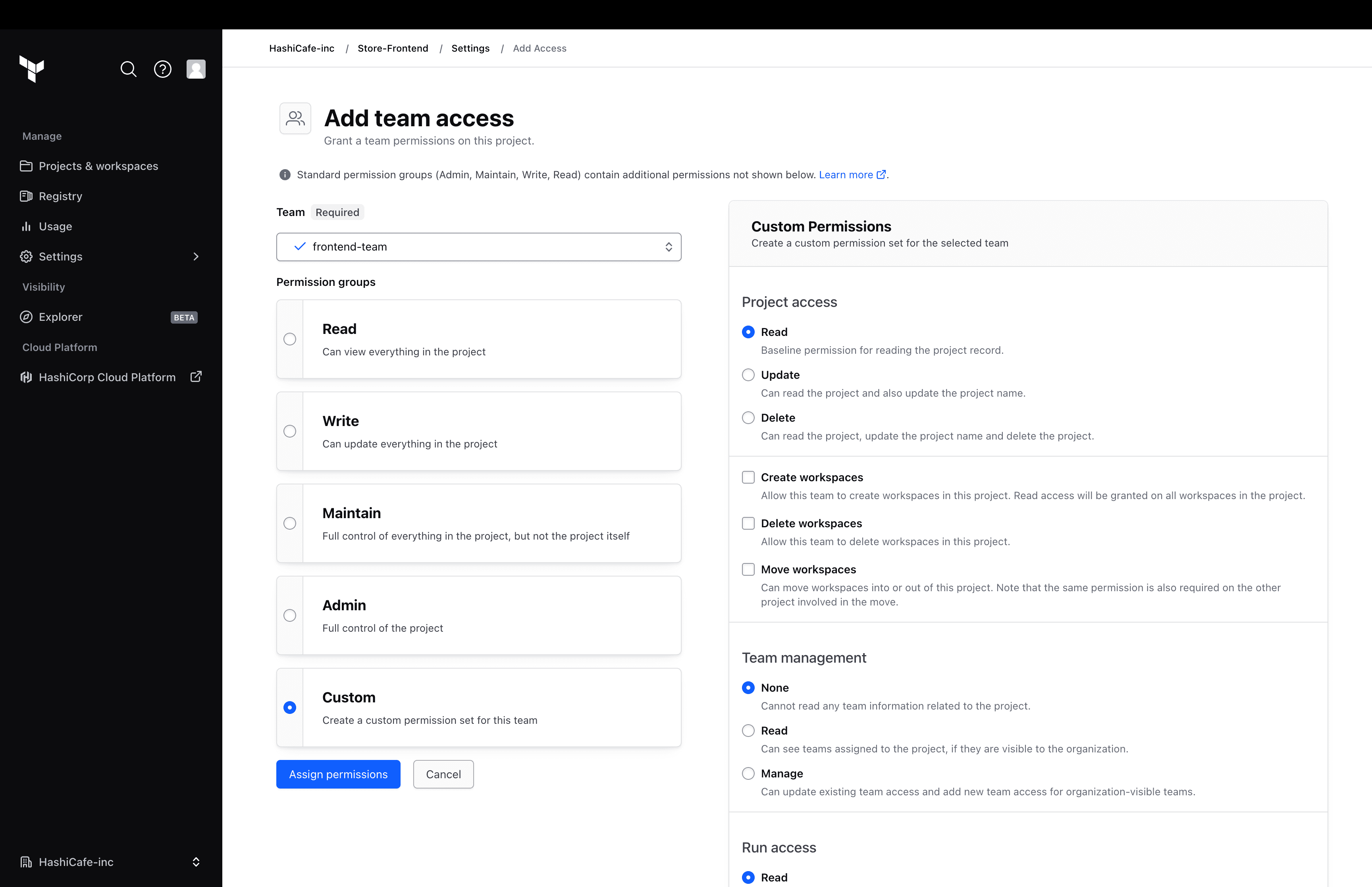
Customizable project permissions allow more flexibility to assign access rights with the appropriate level of permissions.
»Customizable policy assignment
According HashiCorp 2023 State of Cloud Strategy Survey, security is ranked as the #1 multi-cloud success factor. That’s why many customers see policy enforcement as the first line of defense to ensure their infrastructure is secure and compliant.
However, globally enforced policy sets can’t make exceptions for individual workspaces, leaving administrators no choice but to manually apply policy sets to workspaces one at a time. So newly created workspaces, such as those created through no-code provisioning workflows, can become security gaps since policies won’t be enforced automatically.
Customizable policy assignment for Terraform Cloud (coming soon to Terraform Enterprise), allows organizations to assign policy sets at the project level in addition to the previously available organization or workspace levels, maintaining security and compliance with more flexibility. Policies are applied to all current and future workspaces in a project, making self-service provisioning achievable without sacrificing the protection offered by policy guardrails.
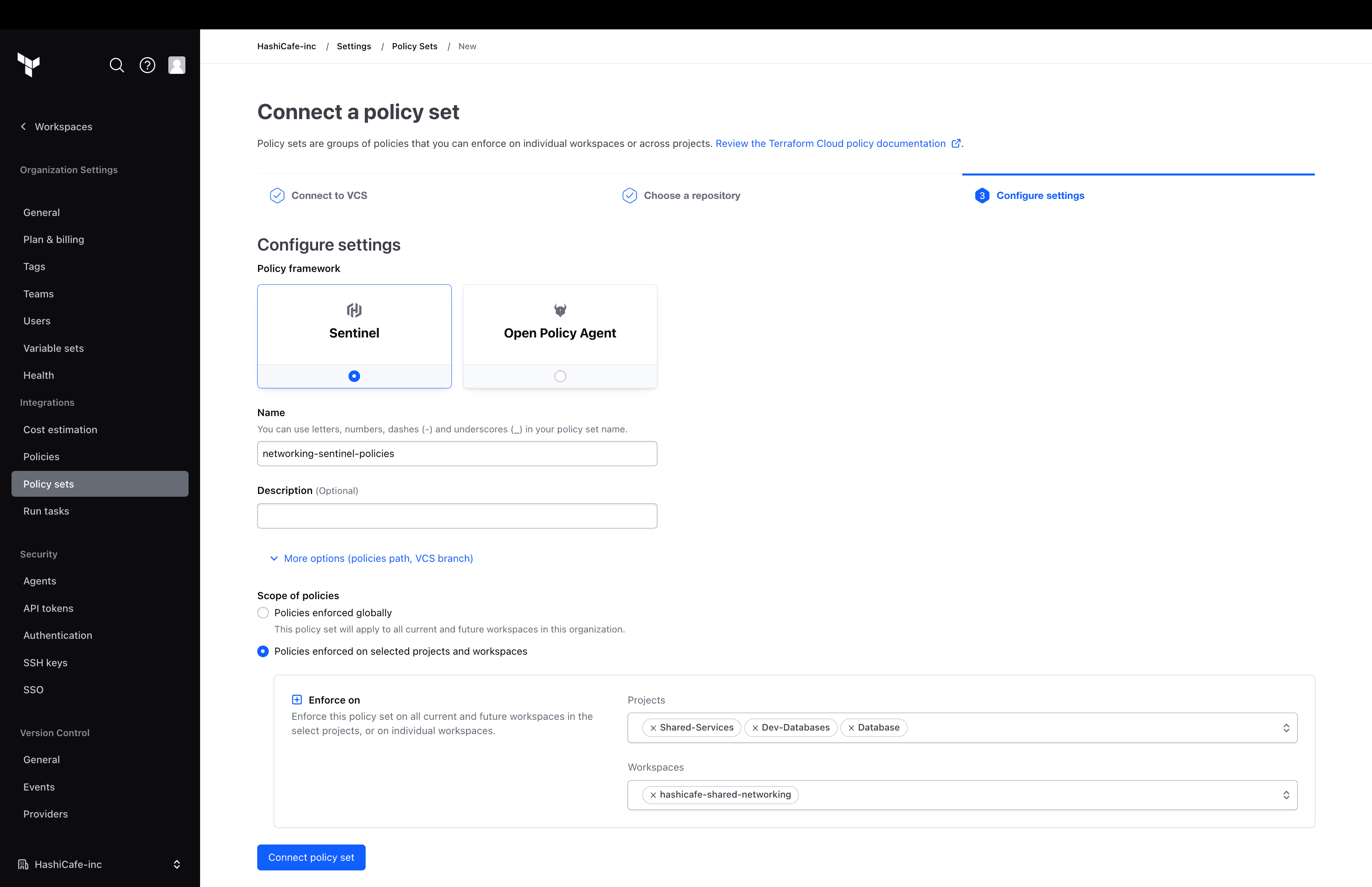
Customizable policy assignment lets organizations enforce policy sets at an organization or project level, or individually on a workspace.
Coming in early September, another new capability will allow a list of workspaces to be excluded from a policy set. This is helpful when a single workspace may have a policy failure and the organization needs to make a temporary exception for that workspace to unblock its owners from provisioning infrastructure while investigating the policy issue.
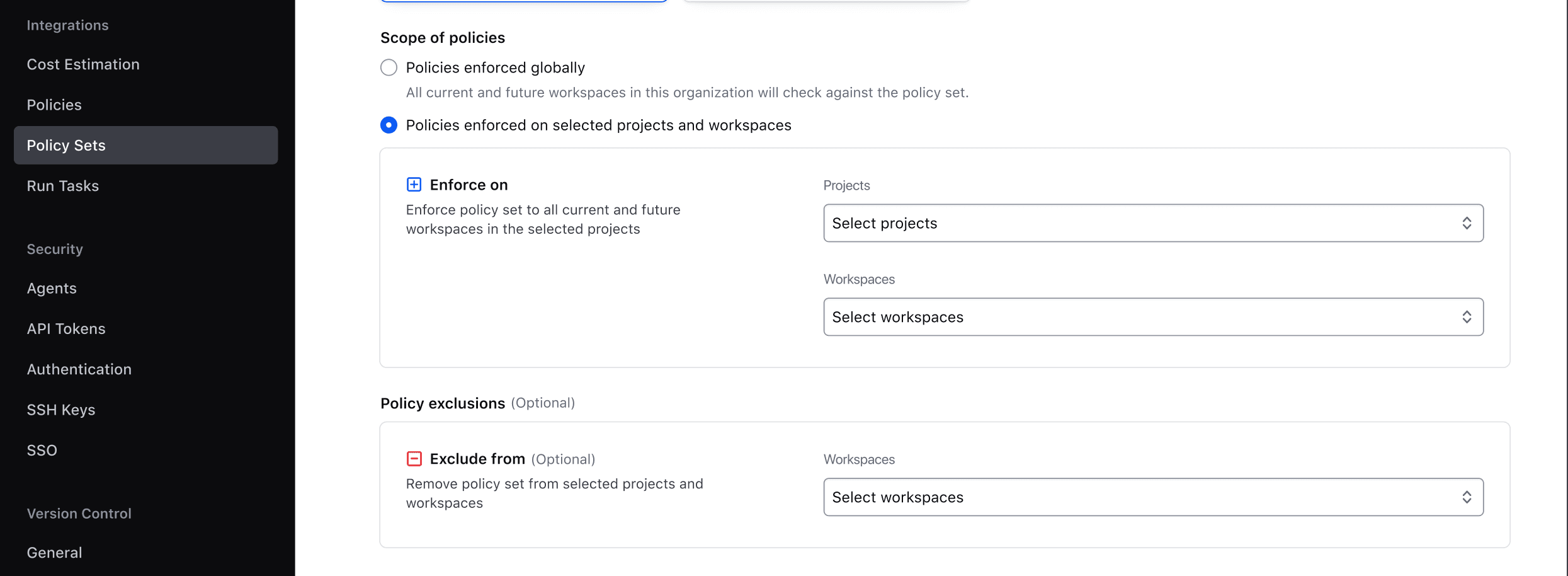
Soon users will be able to exclude a list of workspaces from a policy set.
»Try Terraform Cloud today
Terraform is the industry standard for provisioning and managing any infrastructure. With more customization options in project permissions and policy assignment, organizations can now tailor solutions based on their specific needs to scale confidently. They no longer need to choose between security and productivity.
Try these new features today — and if you are new to Terraform, sign up for Terraform Cloud and get started using the Free offering. For more information, check out the documentation for project permissions and the documentation for policy set assignment.










