This blog is a guest post by Sameer Singh from Cisco Blogs, where it was originally posted.
Today, more organizations are embracing microservices and dynamic infrastructure deployments in cloud environments. In these environments, instances and services can be created and decommissioned as needed, which means keeping track of updates to such components in a fast-changing environment is a challenge for SecOps teams. This new reality requires solutions that are as dynamic as the environments they need to automate.
»Dealing with Changing IP Addresses
Here’s an example: a security policy configured on the Cisco Secure Firewall allows traffic from one service to another based on their IP addresses. It is effective as long as the IP address does not change. If the destination node goes down or becomes inaccessible, another node will replace it, making the policy ineffective. The policy does not dynamically change on the Firewall — it needs an administrator to log into the device and manually update it unless the Cisco Secure Firewall Management Center (FMC) receives dynamic updates to modify the policy rules based on the attributes of the node.
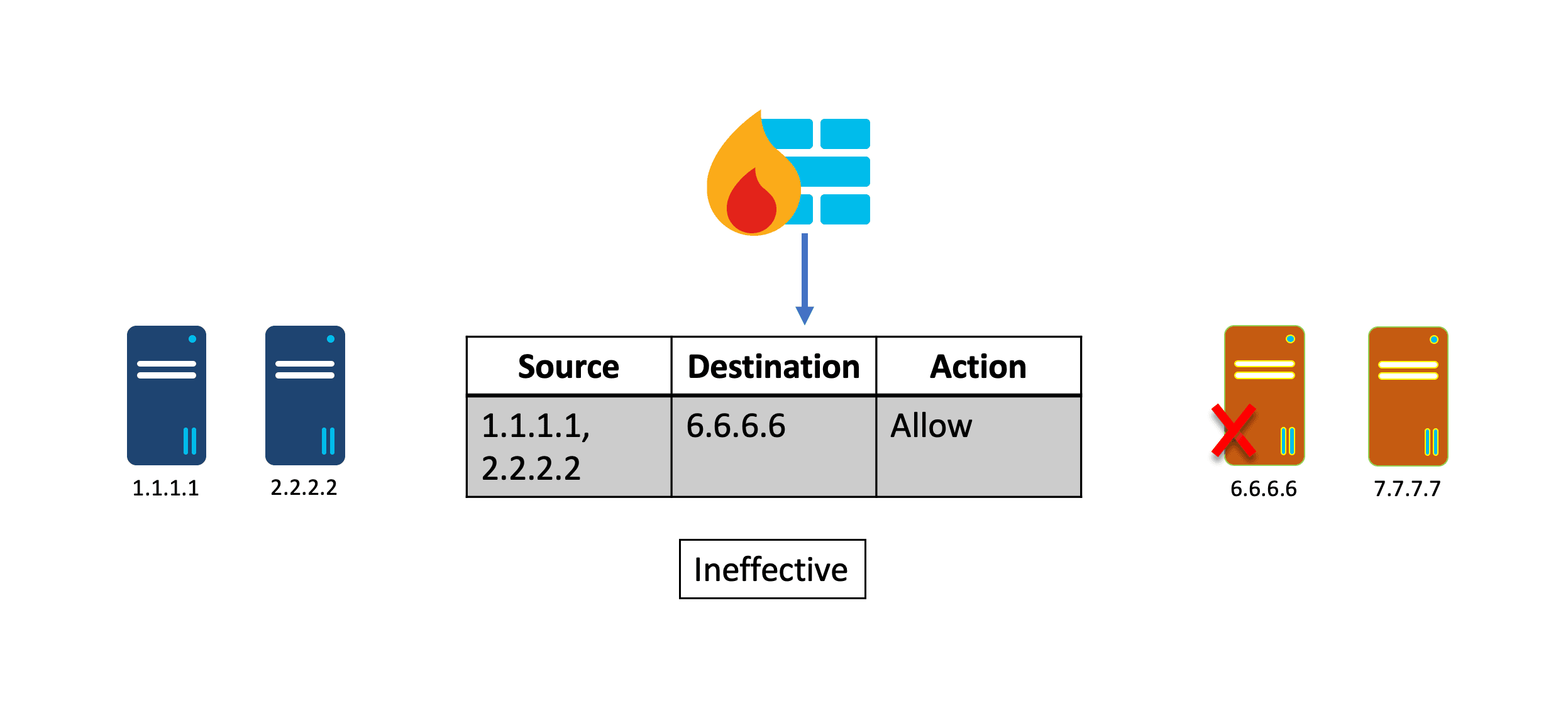
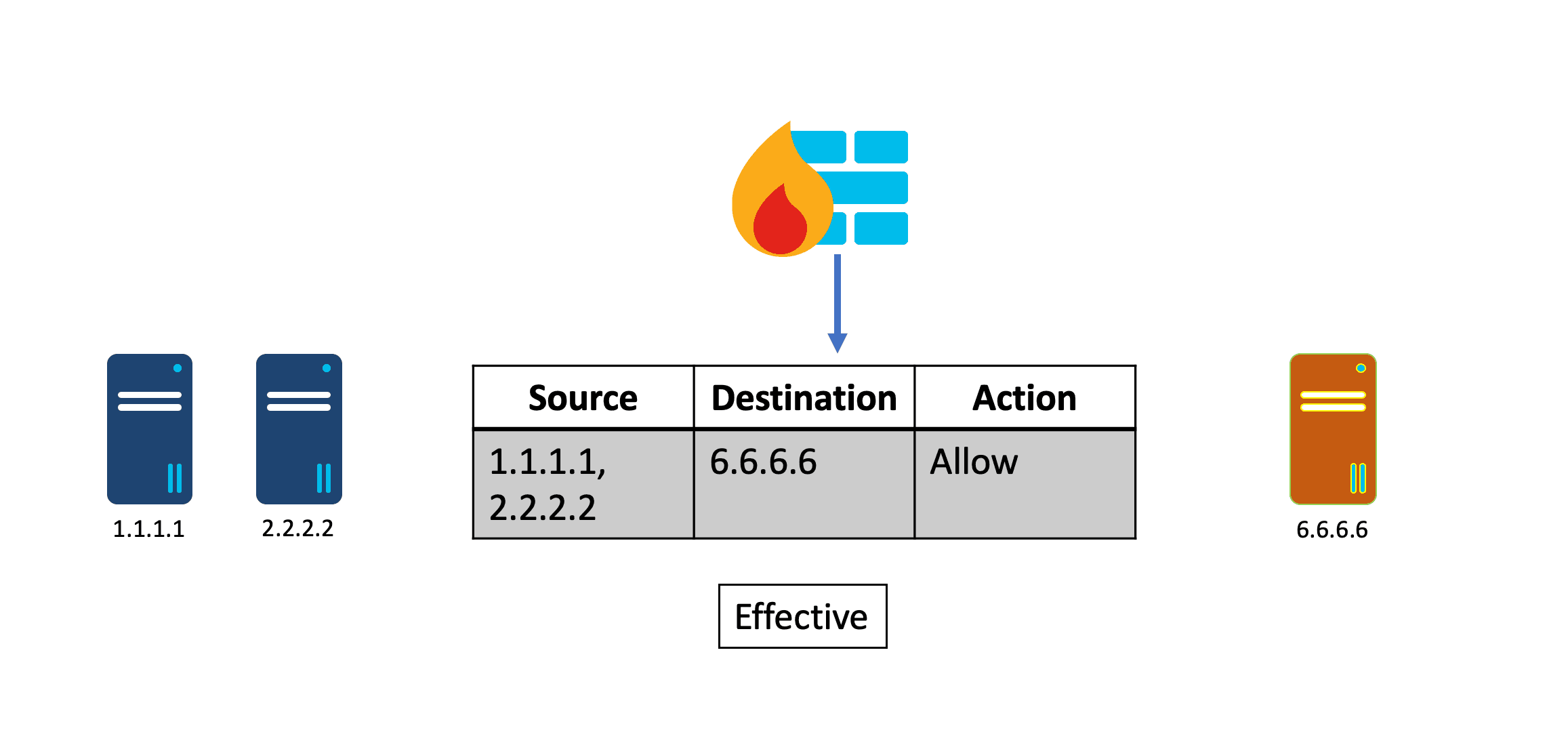
Cisco Secure Dynamic Attribute Connector (CSDAC) and Dynamic Objects on the Cisco Secure Firewall Management Center (FMC) allow changes to IP addresses or other node attributes to be propagated to the Firewall in real-time, eliminating the need to update security policies manually.
Alternatively, IP address mappings in the Dynamic Objects on FMC can be automatically created, updated, and deleted using HashiCorp’s Consul-Terraform-Sync (CTS) solution. For customers who use HashiCorp Terraform and Consul, this is the preferred solution.
»Network Automation with Consul-Terraform-Sync
HashiCorp Consul is a service mesh solution providing service discovery, configuration, and segmentation functionality across several environments. Its service discovery feature allows Consul agents to register services to a central registry called the Consul service catalog.
The Consul-Terraform-Sync service uses the Consul catalog as a data source that contains networking information about services and watches Consul state changes at the application layer (based on service health changes, new instances deployed, etc.) and forwards the data to a CTS-compatible Terraform module that is automatically triggered.
Terraform is used as the underlying automation tool and it leverages the Terraform provider ecosystem to drive relevant changes to the network infrastructure. Using the dynamicobjects module, for example, Consul-Terraform-Sync is able to dynamically update values of objects in Cisco Secure Firewall Management Center (FMC) that are applied as access rules to the firewall.
When the Consul-Terraform-Sync solution is used in conjunction with the dynamic object, the FMC is updated with the IP address mappings received by the dynamicobjects Terraform module. This in turn updates the access rules on the FMC containing that object, which ensures that the right access is always provided to the right services. This diagram illustrates the process:
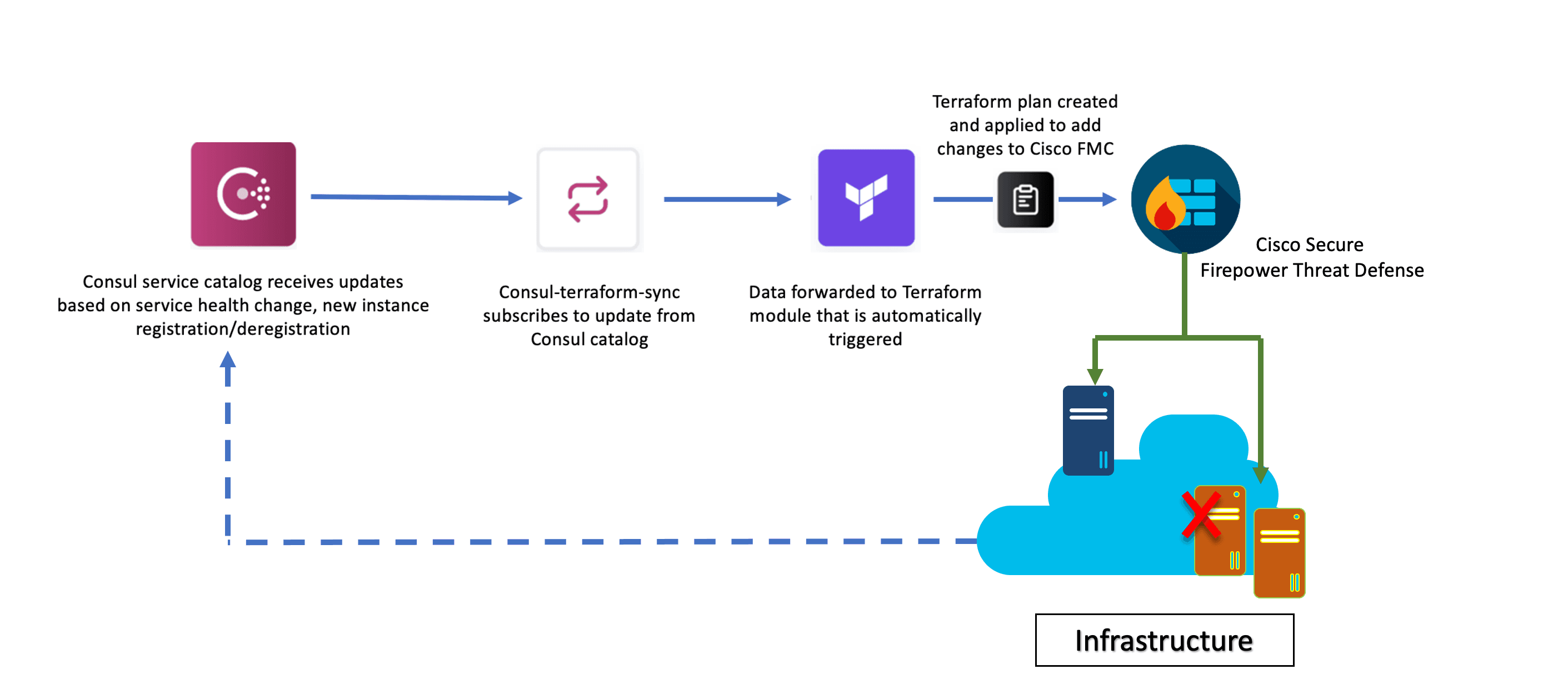
To see how to set up Consul-Terraform-Sync, read HashiCorp’s Network Infrastructure Automation with Consul-Terraform-Sync tutorial on HashiCorp Learn.
»Consul-Terraform-Sync and Cisco: Better Together
The partnership between Cisco and HashiCorp provides an agile solution for tracking dynamic changes in a cloud environment. Read the dynamicobjects Terraform module documentation for more detailed usage and workflow information on integrating Cisco Secure Firewall and Consul-Terraform-Sync.
Related resources:
YouTube Video: Network Security Automation using Cisco Secure Firewall and Hashicorp’s Consul








