Field level encryption (FLE) allows developers to selectively encrypt specific data fields. It helps protect sensitive data and enhances the security of communication between client apps and server. Pairing an FTE-capable database with a KMIP provider offers the highest level of security and control.
The Key Management Interoperability Protocol (KMIP) standard is a widely adopted approach to handle cryptographic workloads and secrets management for enterprise infrastructure such as databases, network storage, and virtual and physical servers. HashiCorp Vault, being a KMIP compliant Key Management Server (KMS), enables organizations to perform cryptographic operations for their apps and services.
With MongoDB releasing client-side field level encryption with KMIP support, customers are now able to use Vault’s KMIP secrets engine to supply the encryption keys. This allows customers to be in full control of their keys.
»MongoDB FLE Features
MongoDB’s drivers encrypt the sensitive fields in your documents before they leave the application. Client-side FLE allows customers to:
- Protect data in transit, at rest, and in use. The database never sees plaintext, but data remains queryable.
- Make data unreadable to anyone running the database for you, even if they have access to the underlying database infrastructure.
- Simplify the process of enforcing right-to-erasure (sometimes called right-to-be-forgotten) mandates in modern privacy regulations such as the GDPR or the CCPA. This is because operators can simply destroy the key encrypting a user’s personally identifiable information (PII), and their data is rendered unreadable and unrecoverable — in memory, at rest, in backups, and in logs.
»Example FLE Flow in MongoDB with KMIP Provider
The diagram below illustrates the query flow submitted by an authenticated client using FLE:
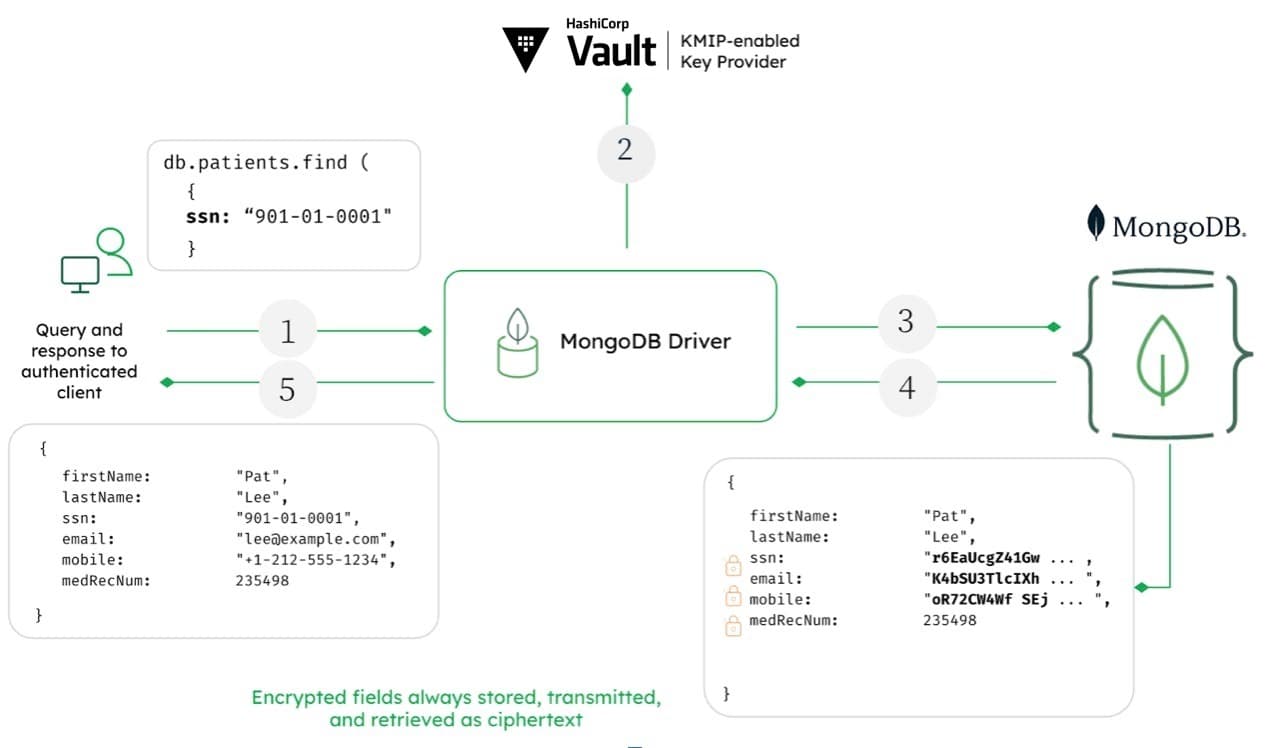
This example assumes we are retrieving a user’s record by their SSN number:
- When the application submits the query, the MongoDB driver analyzes it to determine if any encrypted fields are involved in the filter.
- Recognizing that the query is against an encrypted field, the driver requests the key encryption key (KEK) from the KMIP-enabled key provider. The key provider returns the keys to the MongoDB driver and encrypts the key fields, such as SSN, as shown in this example.
- The driver submits the query to the MongoDB server with the encrypted fields rendered as ciphertext.
- The MongoDB server returns the encrypted results of the query to the driver.
- The query results are decrypted with the keys held by the driver and returned to the authenticated client as readable plaintext.
This is one example of how MongoDB and HashiCorp Vault can help benefit organizations with security management across their databases and applications. We have built many integrations with MongoDB Atlas for database credential rotation and key management to help organizations protect and secure their data infrastructure.
»About MongoDB Atlas and HashiCorp Vault
MongoDB Atlas offers built-in security controls for customer data while also enabling enterprise-grade features to integrate with existing security protocols and compliance standards. In addition, Atlas simplifies deploying and managing databases while offering the versatility for developers to build resilient applications.
HashiCorp Vault is an identity-based sSecurity solution that leverages trusted sources of identity to keep secrets and application data secure with one centralized workflow for tightly controlling access to secrets across applications, systems, and infrastructure and encrypting data both in flight and at rest.
To learn more about how HashiCorp Vault and MongoDB can help your organization navigate through complex security challenges, tune into our virtual talk and session at MongoDB World, June 7-9 in New York City.








