When you have an application that reads data from a database, you can leverage Vault's database secrets engine to dynamically generate a short-lived username and password to secure the database access.
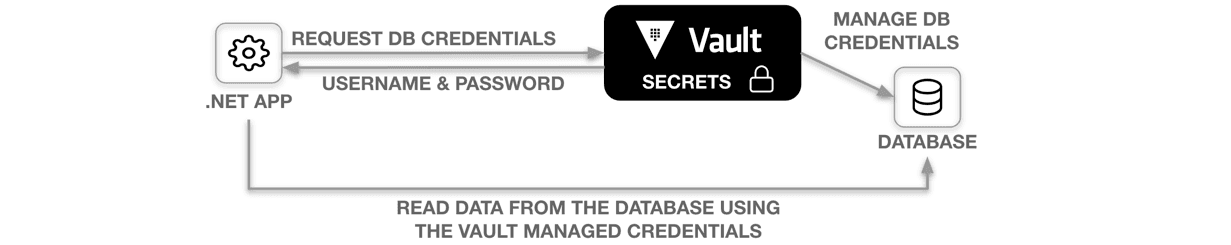
This sounds easy, but to accomplish this, your application must:
- Authenticate with Vault and acquire a token
- Use the token to request database credentials from Vault
- Connect to the target database using the credentials managed by Vault
To demonstrate the end-to-end workflow, we introduced the Using HashiCorp Vault C# Client with .NET Core tutorial. You will see how an ASP.NET Core application uses the Vault Sharp client library to authenticate with Vault and then acquire database credentials to read data from a database.
At the end of this tutorial, it will present another challenge. By keeping the database credentials short-lived, you secure the database connection. However, you now must build additional logic into your application to watch for changes in dynamic secrets and reload. To address this, the Using HashiCorp Vault Agent with .NET Core tutorial demonstrates the use of Vault Agent.
If you are running .NET applications, visit the Vault Learn page to find these two new tutorials.