Before I automate the installation and configuration of a tool, I log into a virtual machine and run each command separately, eventually building a server with the correct configuration and packages. When I teach how to use tools like HashiCorp Vault and Consul on live streams, I encourage the use of manual commands to reinforce important concepts and build tacit knowledge when operating and using a tool. However, I also need a way to help my co-host learn the tools without making them depend too much on pre-existing knowledge of AWS and Terraform. I also need to automate their manual commands to set up for the next streaming episode.
HashiCorp Boundary is a secure remote access solution that provides an easy way to allow access to applications and critical systems with fine-grained authorizations based on trusted identities. Boundary helps me grant temporary access to my co-host on a live stream without them needing to fully understand AWS or Terraform.
In this post, I’ll show you how I use Boundary to grant temporary access to my co-host, record their manual commands on a live stream, and reconcile the commands into automation written in Terraform. At the end of the stream, I play back a session recording and use the configuration to automate the next episode. This workflow of making manual break-glass changes to an endpoint and reconciling the changes to automation applies to any automation you build.
»Grant temporary access to servers
Break-glass changes involve granting temporary access to log in to a system to make emergency changes. When making a live video, I need to collaborate with my co-host, Melissa Gurney (Director of Community Development), and grant her temporary access to a set of virtual machines during the episode. I set up HashiCorp Cloud Platform (HCP) Boundary and create a self-managed Boundary worker to help proxy into EC2 instances on AWS.
On the stream, Melissa uses Boundary Desktop to target a specific server without needing to download its SSH key or pass in a specific username. Prior to using Boundary, my co-host and I would share Amazon EC2 key pairs and label which ones logged into which instance. Now, Boundary automatically injects the SSH credentials from Vault. Melissa and I do not have direct access to the SSH keys, which further secures our environment and reduces the burden of downloading the keys for each EC2 instance.
Some episodes require us to configure multiple servers. To help with this, I create a host set to logically group a set of Vault servers in Boundary, as they share a common function. Melissa selects which Vault server to configure based on the list of hosts.
Sharing a screen on live video has its own security concerns. While we try to avoid showing root credentials in plaintext, we have to run commands that generate tokens and keys that we cannot easily mask. To mitigate the risk of exposing these credentials, I use Boundary to close Melissa’s sessions to each server at the end of each episode. Then, I use Terraform to create a new set of servers after each episode to revoke any tokens or keys.
»Reconcile manual commands into automation
During the live stream, Melissa logs into different servers and runs several commands to configure a Vault server. Prior to using Boundary, my previous co-hosts and I had to remember to copy the history of commands off each server we configured in the episode. We would replay the entire two-hour episode to reverse engineer the history by putting the proper configuration and commands into a script.
Now, I set up Boundary session recording to record each command Melissa runs on the server during the live stream. After the live stream, I find the session recording in Boundary and replay the commands. I directly copy the configuration into my automation for the next episode.
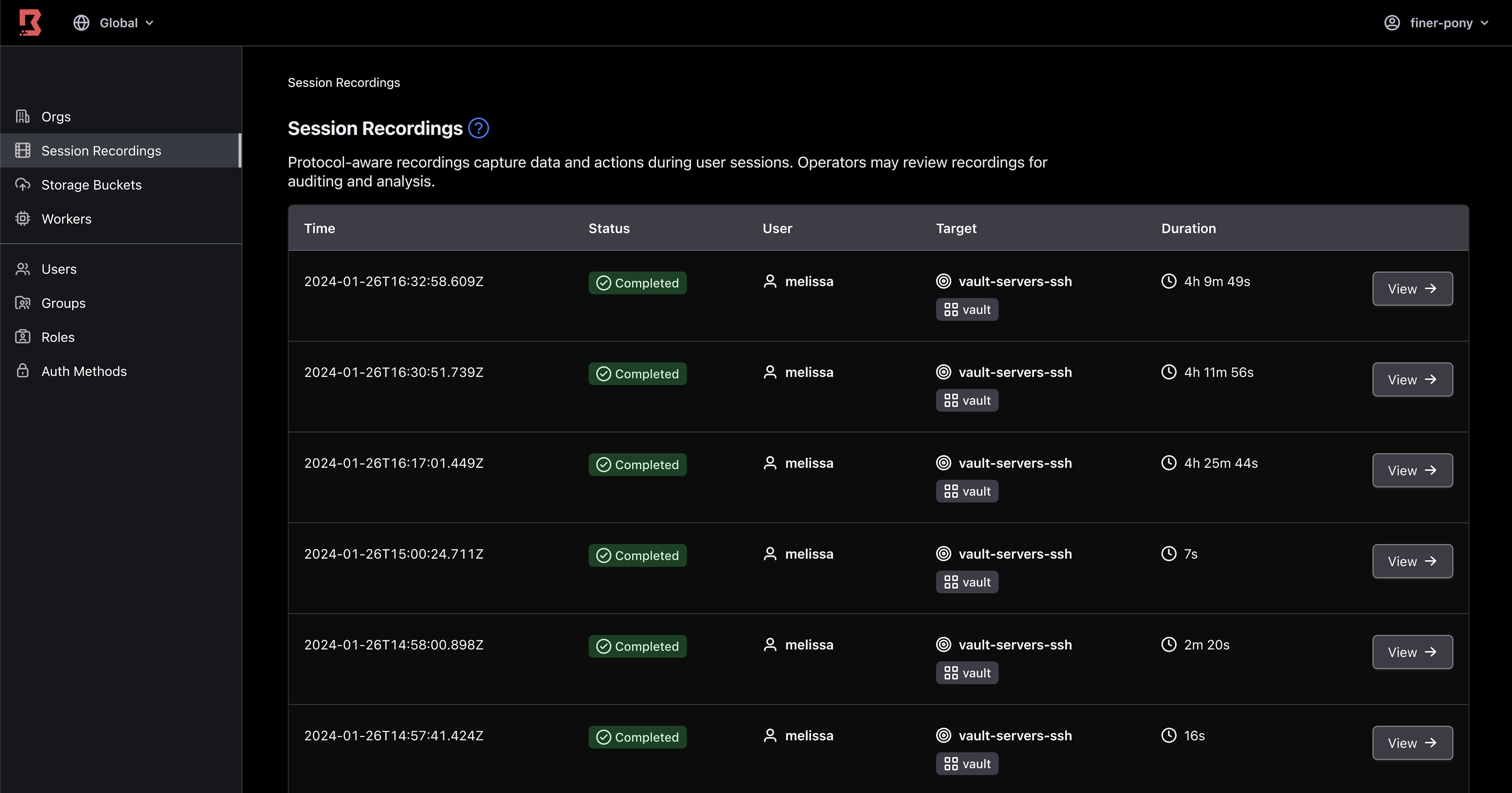
List of Boundary session recordings
For example, Melissa and I manually built a Vault server on one virtual machine instance. After the stream, I found the recording of the session on the Vault server. By reviewing the recording, I could copy a working Vault configuration and update it in the user data script for the EC2 instance.
Even though manual commands require some editing for automation, I can quickly copy a tested sequence of commands and configuration and apply minor updates for automation. These updates include refactoring manual commands and configurations with hard coded IP addresses or EC2 instance identifiers to use templated or dynamically generated values.
»Learn more
By granting temporary access to my co-host during the live stream and recording their manual commands with Boundary, I can track changes across multiple servers and replay them for future automation. Prior to using Boundary, I spent hours reviewing the episode and reconstructing the configuration we typed on stream. Now, it takes less than an hour to copy the configuration and refactor it for automation. As an additional benefit, I can always return to the session recording and verify the manual commands in case I need to build new automation.
The workflow I use for live streams applies to reconstructing any break-glass change you make to production. By using Boundary to control SSH access to servers in production, you can offer on-demand, time-limited access during break-glass changes. Rather than reverse engineer your commands, you can use a session recording to more efficiently copy your changes into automation after you stabilize the system.
To learn more, sign up for HCP Boundary and get started with Boundary session recording. Review our tutorial to enable it on your own Boundary cluster and configure SSH credential injection from Vault. To get a live demonstration of how we use Boundary, tune into our video series for Getting into Vault and check out the repository we use for setting up each episode.









