We are excited to introduce cross-project service principals and fine-grained roles in the HashiCorp Cloud Platform (HCP). These features enhance security, efficiency, and collaboration by allowing more precise role-based access control (RBAC) across different projects.
Cross-project service principals enable access to resources in other projects while adhering to least-privileged access principles, limiting access to only necessary resources and requiring specific permission. Meanwhile, fine-grained roles support more-tailored access control to match specific personas and responsibilities within HCP organizations. These features strengthen and streamline operations across HCP.
»Improved least-privileged access with fine-grained roles
The HashiCorp Cloud Platform (HCP) has expanded the number of roles that can be used to secure access to your services and data. Historically, HCP’s RBAC system supported basic roles that encompassed permissions for all services. These roles are meant to be used to get started on HCP or govern the entirety of your HCP organization. We added fine-grained roles to reflect personas for individual services and strengthen your organization’s security posture.
»HCP’s expanded RBAC capability
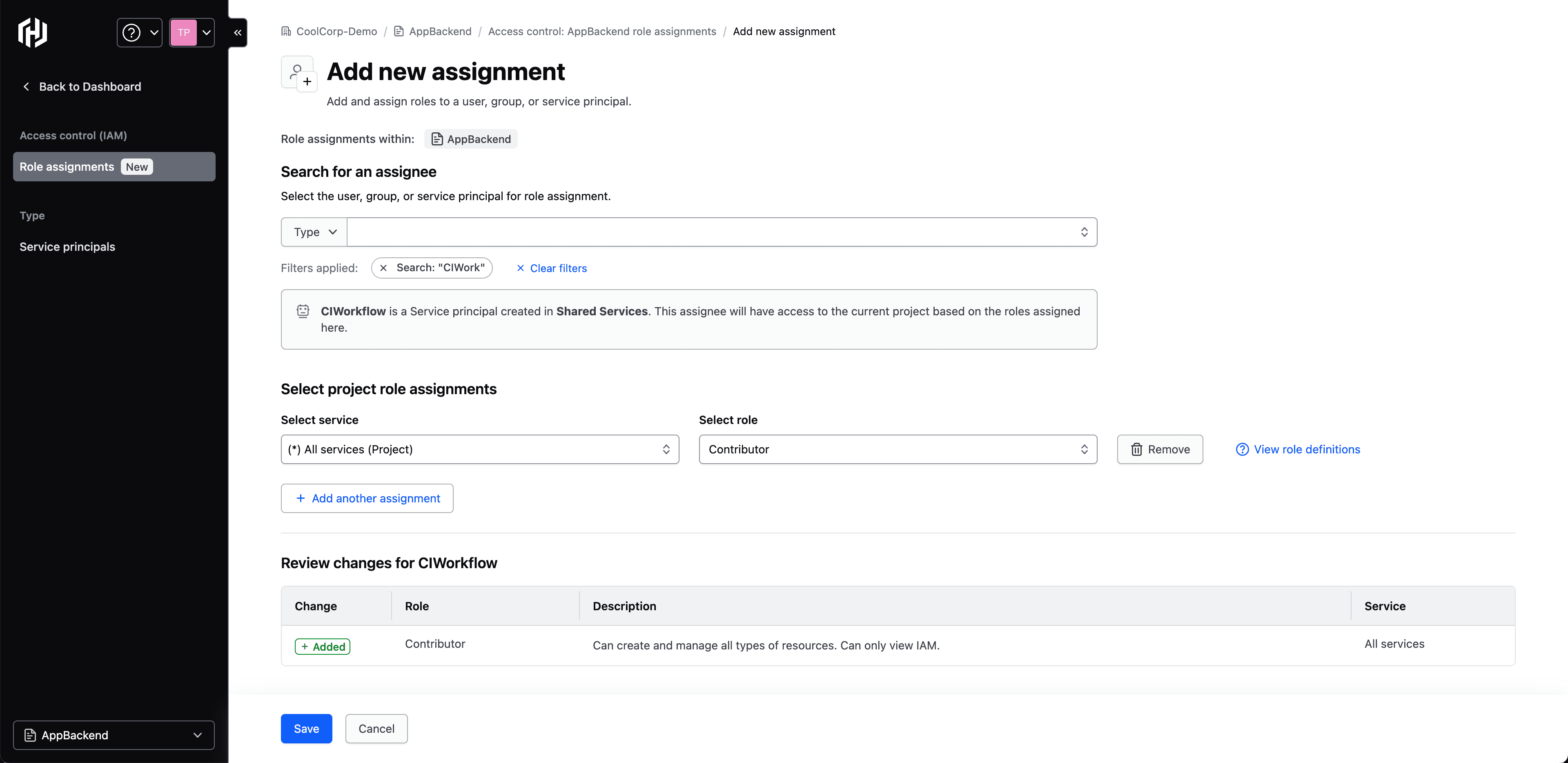
You can now assign multiple roles to HCP identities (users, groups, and service principals) at all tiers of your HCP organization. This helps you better match your team structure and access model in HCP. You can also view role assignments for those same identities, allowing you to audit access to different resources in HCP. You can view identities and role assignments via the Access Control menu in the HCP Portal or through the HCP Terraform provider.


»Project service principals can now access other projects
HCP now supports cross-project interaction through the innovative use of cross-project service principals. This new capability lets customers access and manage resources across different projects, provided they have the requisite permissions. Cross-project service principals are part of HashiCorp’s approach to Security Lifecycle Management (SLM), the process by which organizations protect, inspect, and connect their environments and manage their most sensitive data, from creation to expiration.
In response to customer requests for a more persona-based, project-scoped cloud platform, we are making the roles of cloud engineers, platform engineers, and security personnel more manageable. For example, HCP Vault Secrets previously allowed interaction across project resources only with organizational-level service principals. While this approach was convenient, the access was often too-broad for some team’s security preferences. The addition of cross-project service principals lets you strike a balance between flexibility and security, giving more control and customization over resource access across projects.
Cross-project service principals give users and services access only to the specific projects and resources they need. By mandating explicit permissions for project interaction, this feature supports a privacy-preserving framework that aligns with security best practices. The visibility into all of these access paths also helps teams monitor and assess their security posture.
»The benefits of cross-project service principals
These new capabilities help teams work together more efficiently and securely, securely streamlining operations across multiple projects. Cross-project service principals allow cross-interaction at the project level while maintaining privacy by requiring permissions and approvals from the visited project. Project-level service principals can interact with resources in other projects, but only with the appropriate permissions and approvals. This enhances organizational flexibility and collaboration while maintaining security guardrails. And by adhering to least-privileged access principles, it helps organizations meet compliance requirements and protect sensitive data across projects.
By focusing on cross-project service principals, we hope to reduce enterprises’ reliance on organization-level service principals and advance towards least-privileged access, maximizing security and operational efficiencies across the platform.

»Looking ahead
Cross-project service principals provide a more flexible and secure approach to resource management within the HashiCorp Cloud Platform by easing project-level resource interaction while maintaining strict permission controls. Using HCP’s fine-grained roles with cross-project service principals mitigates risk, enhances collaboration, and makes your organization more secure.
We encourage you to inspect your organization’s security posture and begin integrating the new cross-project service principal capabilities into your workflows for enhanced efficiency and security.
Finally, your feedback is invaluable to us. Please share your experiences and suggestions to help us improve our Security Lifecycle Management portfolio here: HashiCorp Cloud Platform feedback.








