AWS re:Inforce is an immersive cloud security learning event kicking off Monday, June 10, in Philadelphia. HashiCorp once again has a major presence at the event, including breakout sessions, expert talks, and product demos.
Earlier this year, HashiCorp announced The Infrastructure Cloud and showed how Security Lifecycle Management (SLM) helps users protect sensitive elements of their infrastructure, inspect their security posture, and securely connect machines, users, and services. The AWS re:Inforce security conference offers an opportunity to detail the new additions and improvements we have made across our SLM product portfolio that do just that. That includes new announcements and integrations with AWS to help customers enforce security best practices across AWS resources.
Recent HashiCorp/AWS security developments include:
- An agreement to co-develop new policy as code for HashiCorp Terraform
- Secrets sync with HashiCorp Vault and AWS Secrets Manager
- AWS Secrets Manager now displays secrets managed via Vault
- Workload identity federation for AWS
- Scanning secrets in Terraform using HCP Vault Radar
- re:Inforce speaking session: Security Lifecycle Management in a multi-cloud world
»Policy as code co-development
HashiCorp and AWS have announced a Strategic Collaboration Agreement to help customers drive innovation with HashiCorp solutions on AWS. The agreement includes a joint initiative to create policy as code using Terraform.
The concept of policy as code involves writing code in a high-level language to manage and automate policies. For example, you could write a policy using HashiCorp’s policy as code language, Sentinel, to not allow deployments on Fridays, or you could write a policy that only allows approved Terraform modules to be provisioned, unless you’re an administrator.
As part of the agreement, AWS and HashiCorp will co-develop comprehensive Terraform policies that provide expert guidance on architecting, configuring, and operating on AWS. These solutions will include policies for additional AWS services and ensure compliance with standards set by governing bodies such as CIS, HIPAA, and FINOS, while also following the principles of the AWS Well-Architected Framework. This joint effort will help accelerate customer time-to-value for policy as code initiatives, mitigate security and reliability risks, and provide a framework to address outcome-driven use cases surrounding security and compliance. We will provide updates as this collaboration expands.
»Sync secrets with Vault and AWS Secrets Manager
Moving towards an identity-based secrets management solution helps organizations move away from non-scalable, incomplete solutions created by developers to broker secrets across cloud environments. Secrets sync is a new feature for HCP Vault Secrets and Vault Enterprise that helps organizations manage secret sprawl by syncing with other secrets managers to centralize the governance and control of secrets. Secrets sync lets users sync changes out to multiple external secrets managers, including AWS Secrets Manager, in multi-cloud environments to solve the challenges around isolated secrets management, compliance, and protecting expanded attack surfaces. For more information, check out how to Integrate with AWS Secrets Manager on the HashiCorp Cloud Platform (HCP).

Sync secrets with Vault and AWS Secrets Manager
»AWS Secrets Manager displays secrets managed via Vault
To further support secrets sync, users can now search for secrets managed by Vault in AWS Secrets Manager. In the AWS Secrets Manager console, search for secrets “Managed by: HashiCorp” to display secrets managed in Vault.
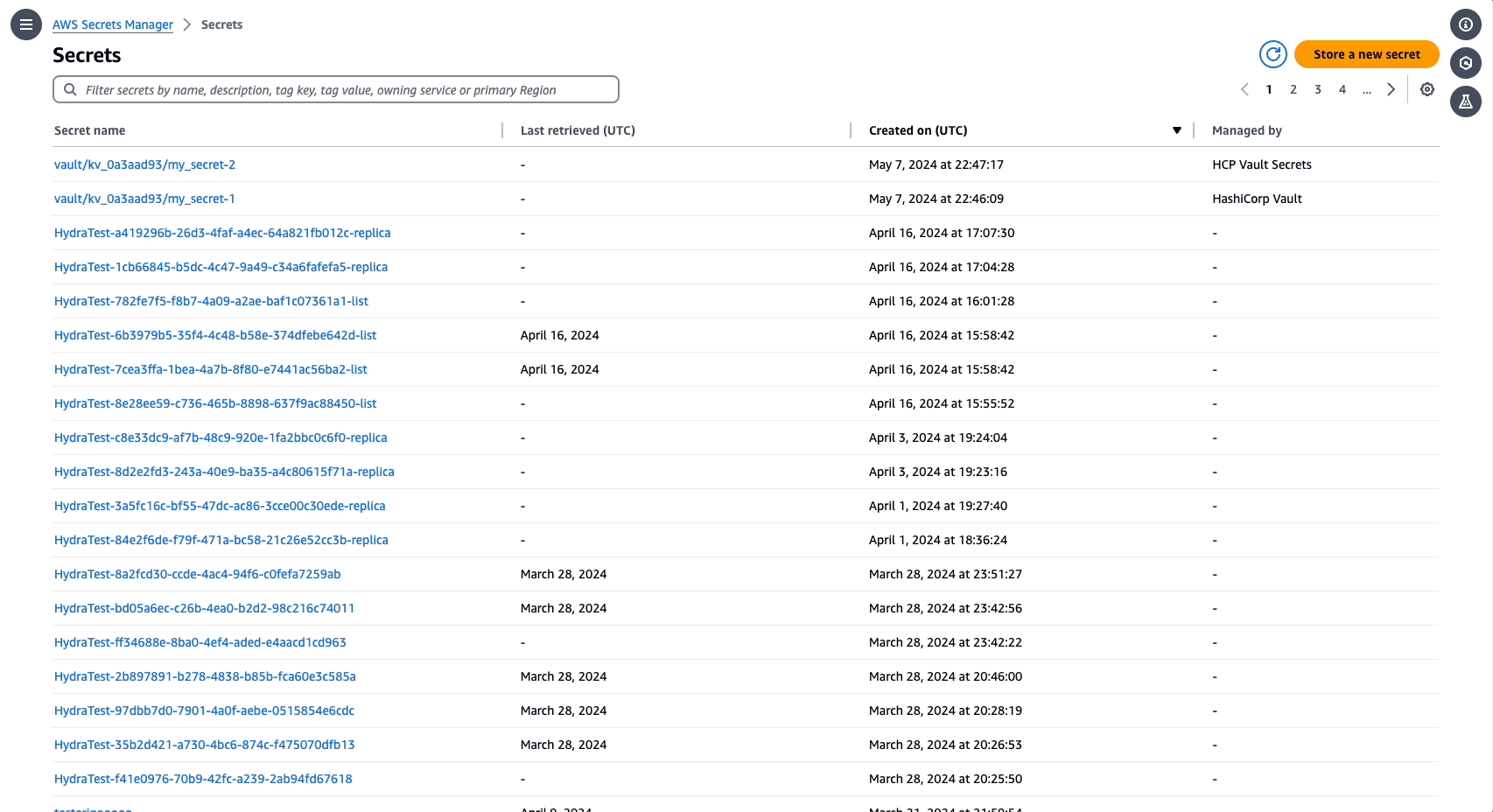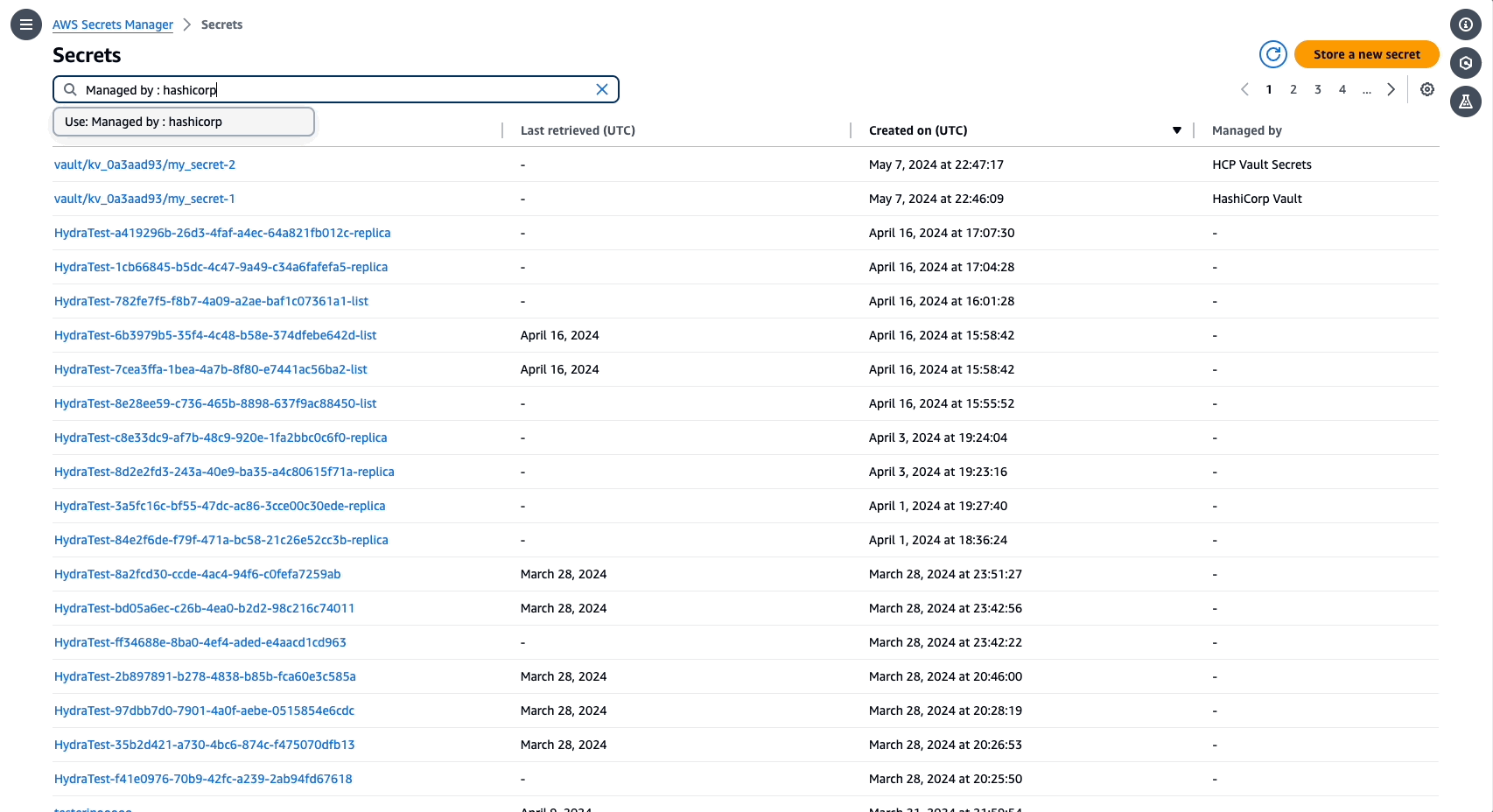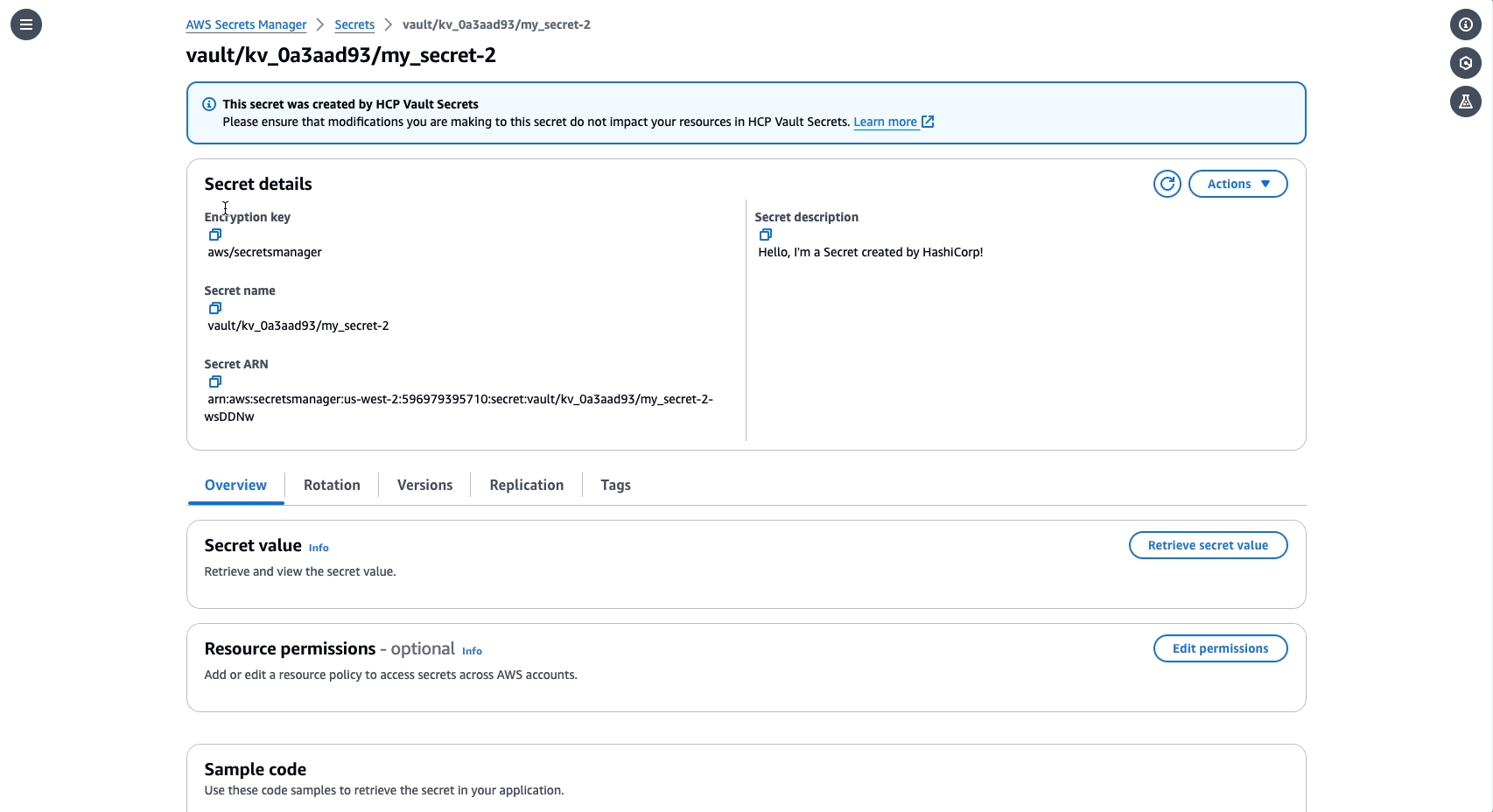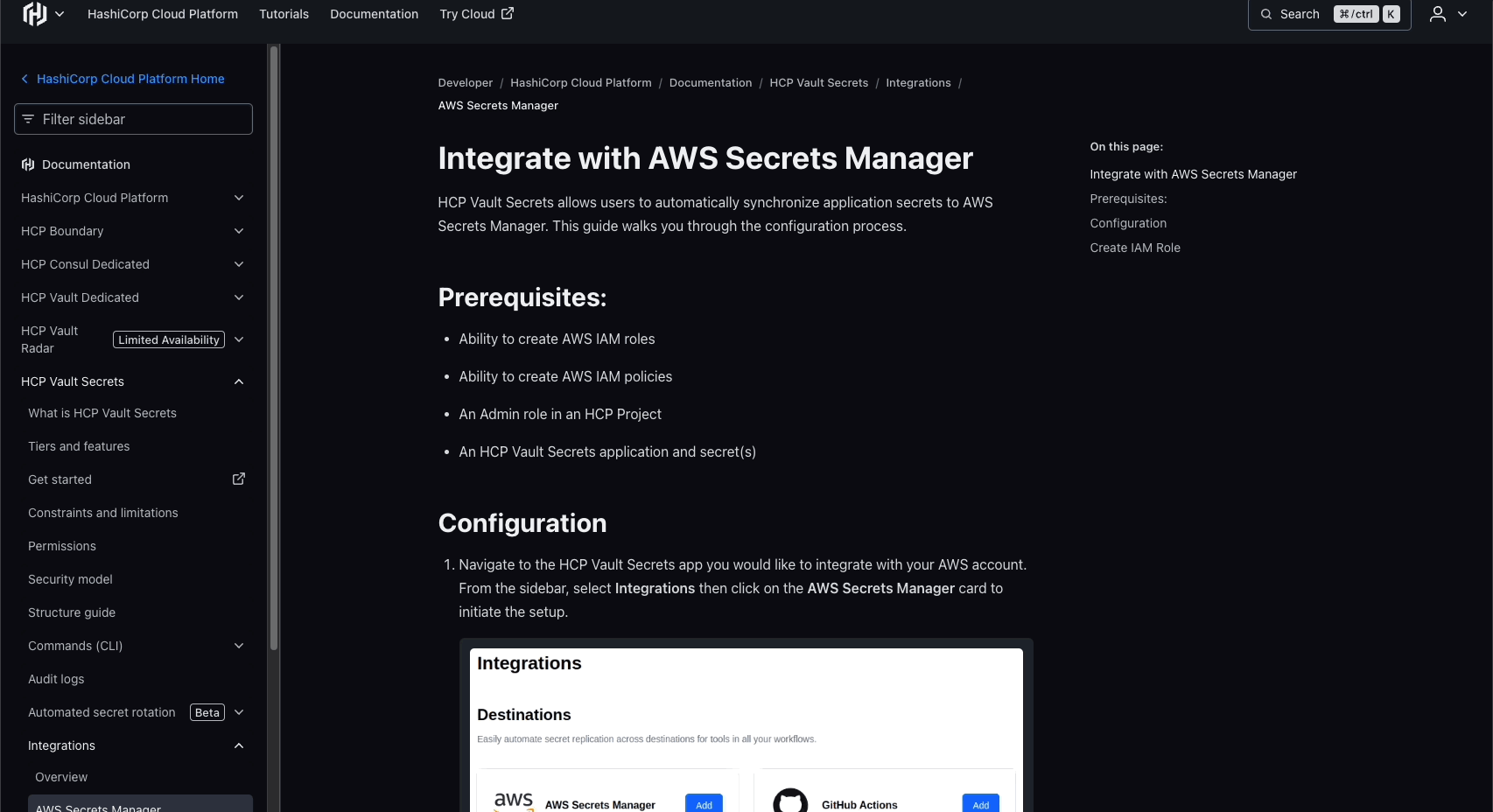
Secrets managed via HashiCorp Vault in the AWS Secrets Manager console
»Workload Identity Federation for AWS
Vault plugins that integrate with external systems require a set of security credentials at configuration, which are often long-lived and highly privileged. This can raise security concerns and be a non-starter for organizations that require ephemeral credentials. Workload Identity Federation (WIF), coming soon to Vault Enterprise in version 1.17, enables secretless configuration for Vault plugins that integrate with external systems supporting WIF, such as Amazon Web Services. By enabling secretless configuration, a Vault-minted identity token can be exchanged for AWS credentials. This helps organizations reduce security concerns that can come with using long-lived and highly privileged security credentials. With WIF, Vault no longer needs access to highly sensitive root credentials for cloud providers, giving operators a solution to the “secret zero” problem.
»Scanning secrets in Terraform using Vault Radar
HCP Vault Radar automates the detection and identification of unmanaged secrets in your code, including AWS infrastructure configurations, so that security teams can take appropriate actions to remediate issues. Radar continuously scans in real-time for the following types of information:
- Secrets
- Personally identifiable information (PII)
- Non-inclusive language (NIL)
Once the scanning is complete, Radar displays the detected risks in your code by categories and ranks.
For DevOps engineers, secret scanning in Terraform is essential for keeping your infrastructure secure. When you write and commit code, it's easy to accidentally include sensitive information like passwords or API keys, especially when experimenting or locally testing your Terraform configs. However, in production, this could lead to disaster. Secret scanning can help you catch these issues before they get saved in your version control system. This not only protects your infrastructure from security breaches but also ensures you're following best practices. Secret scanning offers peace of mind and lets engineers focus on building and maintaining systems without worrying about exposing sensitive data.
For more information on HCP Vault Radar, please join the re:Inforce lightning talk mentioned below, where we will demonstrate how to scan for unsecure secrets and how to get real-time notifications when secrets are being introduced in unsecure places.
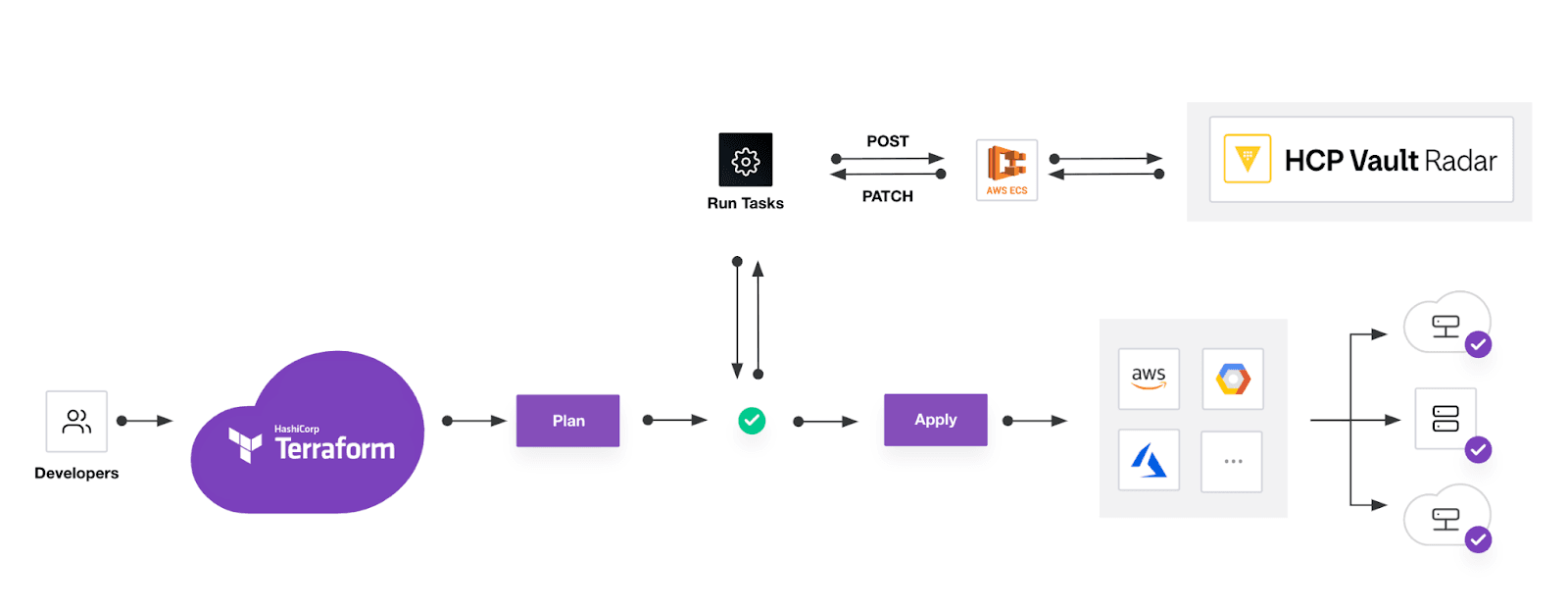
Where scanning secrets fits into a Terraform workflow using Vault Radar
»Security lifecycle management in a multi-cloud world
If you’re attending AWS re:Inforce, please stop by our booth (#1103) to chat with our technical experts, take in a product demo, and learn how companies like yours are accelerating their cloud journey with HashiCorp and AWS.
Join us for a lightning talk at re:Inforce covering how HashiCorp’s Security Lifecycle Management capabilities help organizations continuously protect secrets, certificates, and other credentials; inspect their digital estate for unsecured credentials; and connect authorized machines, services, and people. Please join HashiCorp for: Security lifecycle management in a multi-cloud world (Session ID: APS222-S) on Tuesday, June 11 at 1 p.m. ET.
If you can’t make it to re:Inforce this year, we invite you to join HashiCorp, AWS, and fellow practitioners for a zero trust, identity-based security workshop on how to use HashiCorp Vault on AWS for effective secrets management on Wednesday, June 26 at 12 p.m. PT.








