As part of our release of HashiCorp Consul Service on Azure, we've released a set of HashiCorp Learn guides for HCS on Azure, as well as a video resource for helping deploy ACL's in Consul. It's highly encouraged to review these resources as you get started.
In this post, we expand on our previous blog by looking at extending our HashiCorp Consul Service (HCS) on Azure service mesh to include more than Kubernetes (AKS) clusters. Virtual Machines continue to be a critical part of most operator infrastructure environments, and knowing that workloads will continue to be heterogeneous, having a service mesh that seamlessly creates a consistent service networking experience between Virtual Machines and Containerized workloads is equally critical.
In the video above, we show how we can take Virtual Machines hosted in Microsoft Azure and bring them into the same Consul service mesh that our AKS cluster joined previously. This configuration currently requires connectivity between the Consul client nodes in the AKS and the Virtual Machine networks. We meet this requirement by peering the workload networks with each other and with the HCS network.
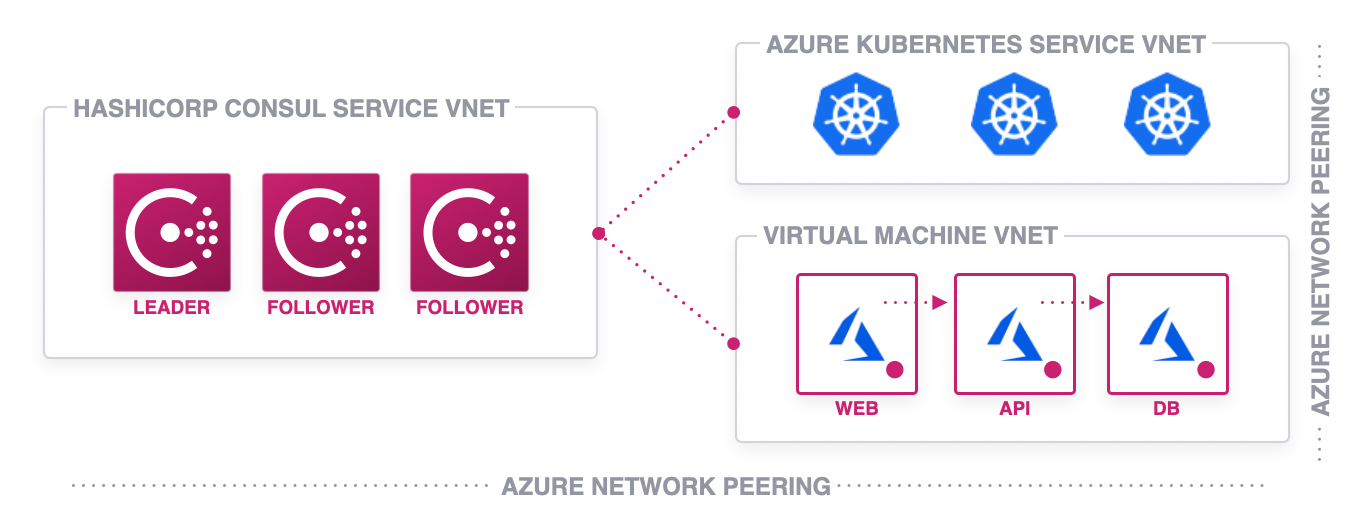
Once these machines are joined to the service mesh, we now have a common control-plane that allows us to consistently apply policies across the environment regardless of the underlying runtime environment. This includes the ability to secure service-to-service communication with mTLS encryption, add Layer 7 routing policies, or expose observability capabilities for both Consul and the workloads running inside it. You can take a look at deploying Consul’s service mesh capabilities in the HashiCorp Learn guide for Consul service mesh.
In this demonstration, we also show how we can use Terraform Cloud to not only deploy additional workloads into our HCS environment with the updated Azure Terraform Provider, but also how we can manage service mesh security policies (intentions) and application configurations “as-code” within Consul using the Consul Terraform Provider. These workload changes are deployed at code check-in leveraging Terraform Cloud’s GitHub VCS integration. To learn more, take a look at the HashiCorp Learn guides for HCS on Azure and Terraform Cloud.








