According to Evanta, a Gartner company, cybersecurity is CIOs’ top priority. Yet the cloud resources that enterprise teams are briskly provisioning to deliver on their CIO’s other immediate priorities — data and analytics, AI/machine learning, digital business priorities and applications — could, in fact, be introducing systemic vulnerabilities that increase cybersecurity risk. Every resource provisioned across public, private, and hybrid cloud networks is a roll of the metaphorical dice, and can leave enterprises susceptible to ransomware and malware, data breaches, insider threats, DDoS attacks, API vulnerabilities, and more.
This blog presents 7 common mistakes development teams make when provisioning and managing cloud resources over time, and how to avoid them through effective Infrastructure Lifecycle Management (ILM). By adopting tools and techniques to standardize the approach to infrastructure enterprise-wide, CIOs and IT organizations can do more than ease current cyber risks; they can move on to higher levels of cloud maturity that focus on proactive cloud data security, faster innovation, and finding more efficiencies, and reducing the often-surprising costs of cloud computing.

Source: Evanta, a Gartner Company
»1. Manual processes
Solution: Use an infrastructure as code (IaC) solution for infrastructure automation
Organizations relatively new to the cloud, and/or rapidly provisioning resources across the enterprise, typically use an ad hoc approach. Teams will each pick individual solutions and do what works in the moment. Sometimes that results in teams still using legacy methods of infrastructure management, either manually provisioning infrastructure through vendor consoles (often called “ClickOps”) or writing one-off scripts that have limited reusability and visibility, creating a brittle provisioning process.
Successful cloud provisioning starts with a systematic and repeatable approach that can be used by all teams. Many organizations use infrastructure as code (IaC) to codify cloud infrastructure and the underlying system images. Once codified, infrastructure can be easily versioned, tracked, reused, and automatically provisioned across multiple cloud environments, eliminating the need for unscalable manual approaches.
»2. Siloed teams
Solution: Enable and promote cross-functional collaboration with a platform-oriented approach
Organizations typically start with a fragmented approach to cloud migration, letting teams build their own unique, non-standard solutions. Teams are reinventing the solutions for the same problems while also failing to share best practices. The adequate security management of so many fragmented solutions is also impossible and cost prohibitive. The resulting costs and cyber risks in this ‘wild west’ scenario quickly spiral out of control.
The first step in implementing provisioning best practices is to break down organizational silos with access to a central library of shared infrastructure configurations, composed of proven code written by experts. In doing so, teams can avoid reinventing well-established configurations — and avoid the many risks that inconsistency invites.
IT leaders also need to put into place a common platform to access, review, and version infrastructure. IaC workflows can be integrated with a version control system (VCS) such as GitHub or GitLab, giving teams a common code base. This promotes the reuse of best practices and patterns, boosts productivity, increases visibility, and sets the foundation for infrastructure as a shared service across the entire organization.
Finally, as teams begin collaborating, role-based access control (RBAC) can help effectively manage team permissions and facilitate security best practices including least-privilege access.
»3. Inconsistent deployments
Solution: Standardize cloud provisioning with “golden” best practice templates
Without any sorts of templates or consistent provisioning and CI/CD pipelines, teams are still doing manual operations and creating too many unique infrastructure setups. Inconsistency is at the root of many security vulnerabilities, and it’s common across large enterprises.
The solution to inconsistent cloud infrastructure provisioning is a “golden path”. In platform engineering, platform teams create golden images, modules, pipelines, orchestration jobs, and any other software delivery component templates that serve as “golden” standards that can be reused by development teams to automatically follow best practices with every deployment.
To build this set of golden templates, platform teams should create, test, and validate reusable infrastructure modules and images, and then make them easily discoverable throughout the organization. With the proper provisioning platform, platforms should have the ability to:
- Create infrastructure templates: Build infrastructure as code modules and images
- Test and validate the code: Build tests that can validate the functionality of IaC configurations in a safe environment by running tests against specific, short-lived resources.
- Make templates discoverable and manageable: Once modules are ready for use, they can be published in an internal private registry. From there, the platform team needs visibility tools and full module lifecycle management capabilities so that they can see template usage patterns, get versioning information, organize and tag templates, and revoke or deprecate templates when a new replacement is created.
»4. No embedded guardrails
Solution: Use policy as code to meet risk and cost requirements
Rapid provisioning opens up tremendous possibilities for innovation, but without effective guardrails in place, it’s a nightmare for security and finance teams. Security, compliance, and cost policies have typically required manual validation and enforcement through a ticket-ops system. This often meant days or weeks-long bottlenecks as developers and IT waited for their infrastructure changes to be approved.
Like infrastructure as code, policy as code can be used to reduce manual errors, enable greater scale through automation, and accelerate productivity. Cloud provisioning solutions that include policy as code can help users define custom policies that are automatically enforced in the provisioning workflow.
For example, policies can:
- Check if end users are consuming approved modules rather than creating custom code
- Ensure the infrastructure is tagged for visibility
- Confirm that storage buckets are encrypted and not publicly accessible
- And much more — the possibilities are numerous
Platform teams can create and organize policy sets in the same way they would manage infrastructure modules, with a library of trusted pre-written policy sets that can enforce best practices. The best policy engines can even integrate third-party tools from various vendors to enact additional checks.
»5. Insufficient monitoring capabilities
Solution: Monitor infrastructure drift and health over time
Once cloud resources are up and running, teams need to make sure their infrastructure remains performant and healthy. Failure to do so can result in costly outages or security problems due to misconfigurations. Even with a standardized provisioning process and policy guardrails in place, configuration drift can occur, creating vulnerabilities or bugs.
Effective ILM incorporates a system of record to provide visibility and monitoring capabilities, and remediate issues as they arise. A cloud infrastructure management solution with drift detection capabilities surfaces problems to admins as they develop. In addition, continuous monitoring provides health checks to verify that cloud workspaces perform as planned, over time.
»6. No lifecycle management
Solution: Automate infrastructure deletion
Organizations scaling their cloud program often accumulate abandoned cloud instances and unnecessary infrastructure that continues to run, wasting money. These forgotten resources can also open security holes if they haven’t received security updates in a while.
Setting end-of-life dates and automating infrastructure destruction helps to eliminate unnecessary cloud waste and close security gaps. Ideally, resource deletion can be triggered when a predefined date or inactivity period is reached, with artifact revocation scheduled at the image level. Users should be automatically notified of impending deprecation actions and receive follow-up actions to confirm deletion.
»7. Lack of self-service
Solution: Scale efficiently by giving developers freedom and autonomy within the golden path
As organizations ramp up their consumption of cloud resources, an automated self-service provisioning workflow empowers developers to quickly deploy the resources they need without slow, demotivating ticket-based workflows that require many manual approvals.
No-code provisioning can make self-service even faster while preserving all guardrails, especially when it’s integrated with popular self-service platforms such as ServiceNow and AWS Service Catalog, or GitHub Actions. Platform teams can also set up an internal development platform (IDP) to expand self-service, further abstracting the application deployment workflow to the point where developers don’t need to manually trigger a ton of tools at runtime.
Ultimately, the goal of self-service is to give developers a set of golden workflows so they can focus on the application lifecycle while platform teams own the underlying infrastructure and security teams have ownership over designing the guardrails. In this way, innovation can occur freely while automatically mitigating cybersecurity risk and keeping costs down.
»Achieving ILM maturity
Avoiding the most common mistakes in cloud infrastructure management can immediately improve an organization’s cybersecurity posture by preventing vulnerabilities from ever being created. It can also speed up innovation by providing developers with the cloud resources they need faster. By following the 7 solution steps described in this blog, organizations can advance their ILM maturity, setting up a virtuous cycle of continuous improvement by consistently upgrading and sharing new golden templates and workflows.
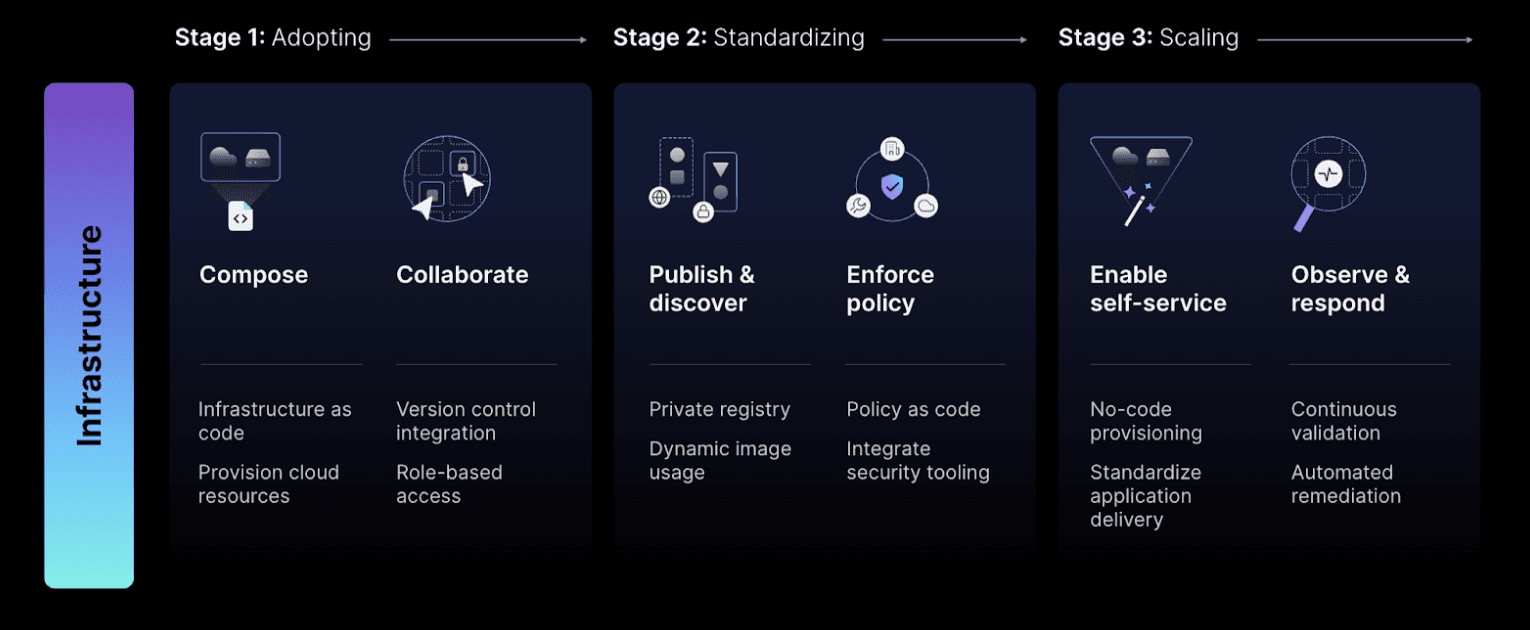
Stages of ILM maturity
To learn more about how ILM maturity can help CIOs achieve all of their Top 5 priorities for 2024 and beyond, get your copy of the HashiCorp white paper, “ILM with the HashiCorp Platform,” and follow HashiCorp on LinkedIn.









