We are pleased to announce the general availability of Consul-Terraform-Sync (CTS) 0.6. This release marks another step in the maturity of our larger Network Infrastructure Automation (NIA) solution.
CTS combines the functionality of HashiCorp Terraform and HashiCorp Consul to eliminate manual ticket-based systems across on-premises and cloud environments. Its capabilities can be broken down into two parts: For Day 0 and Day 1, teams use Terraform to quickly deploy network devices and infrastructure in a consistent and reproducible manner. Once established, teams manage Day 2 networking tasks by integrating Consul’s catalog to register services into the system via CTS. Whenever a change is recorded to the service catalog, CTS triggers a Terraform run that uses partner ecosystem integrations to automate updates and deployments for load balancers, firewall policies, and other service-defined networking components.
This post covers the evolution of CTS and highlights the new features in CTS 0.6.
»CTS 0.1 Through 0.5
- The 0.1 and 0.2 CTS releases enabled a publisher-subscriber (pub-sub) paradigm for updating your network infrastructure based on changes in the HashiCorp Consul catalog, leveraging the Terraform CLI on the local node. These releases focused on establishing core networking use cases for practitioners, including applying firewall policies, updating load balancer member pools, and more.
- The 0.3 release of CTS marked a major milestone by adding support for Consul-Terraform-Sync Enterprise. This release featured regex support for service triggers and Terraform Enterprise integration.
- The 0.4 release of Consul-Terraform-Sync enabled integration with Terraform Cloud and support to trigger a Terraform workflow based on Consul key-value (KV) changes. The integration with Terraform Enterprise and Terraform Cloud allowed organizations to dynamically manage their Day 2 applications’ networking delivery lifecycle and oversee infrastructure with governance and security functionality.
- The CTS 0.5 release in February improved task lifecycle APIs and CLIs to reduce friction while streamlining configuration management workflows.
»Service-Registration, Health Checks, and CLI Discoverability
Our goal has been to provide our users with a smooth and consistent experience for configuring and operating CTS. But we learned from our users that, as they scale out their CTS deployments, there is not an easy way for them to keep inventory and monitor the health of their CTS instances.This release adds two new capabilities designed to address these issues. CTS 0.6 release supports a new configuration block that auto registers CTS as a service with Consul as soon as the CTS is instantiated. This eliminates the manual step of registering CTS as a service within the Consul catalog. This service registration also enables health checking on CTS using the newly added health API endpoint.
The snippet below shows the configuration to register CTS as a service within a Consul cluster:
id = "cts-01"
port = 8558
consul {
address = "localhost:8500"
token = <consul_acl_token>
service_registration {
enabled = true
address = "127.0.0.1"
service_name = "cts"
default_check {
enabled = true
address = "http://localhost:8558"
}
}
}
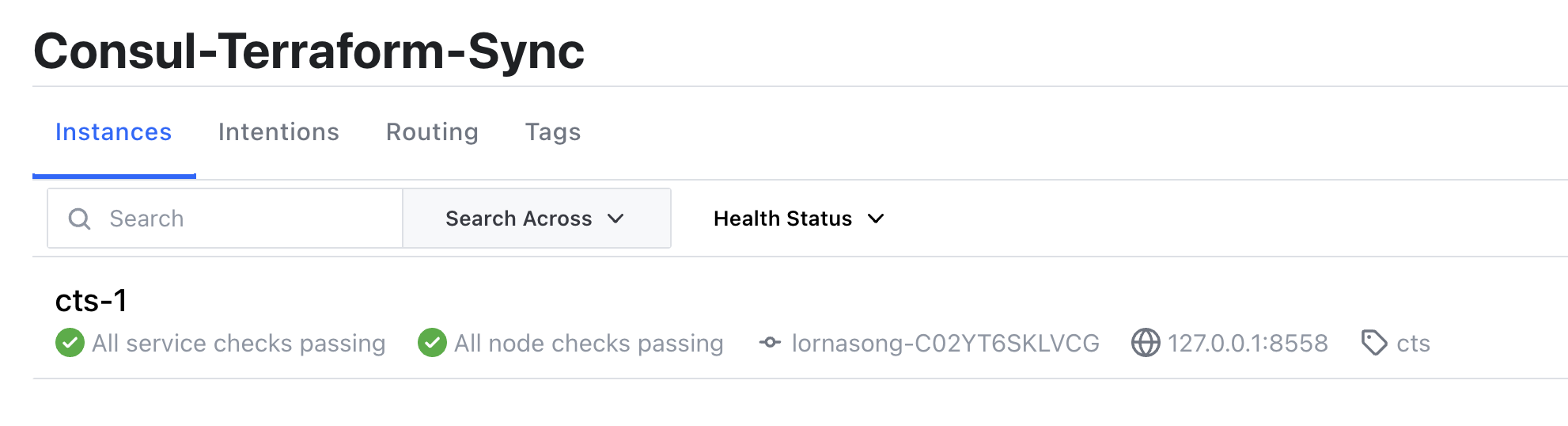
CTS instance registered as a service within Consul catalog.
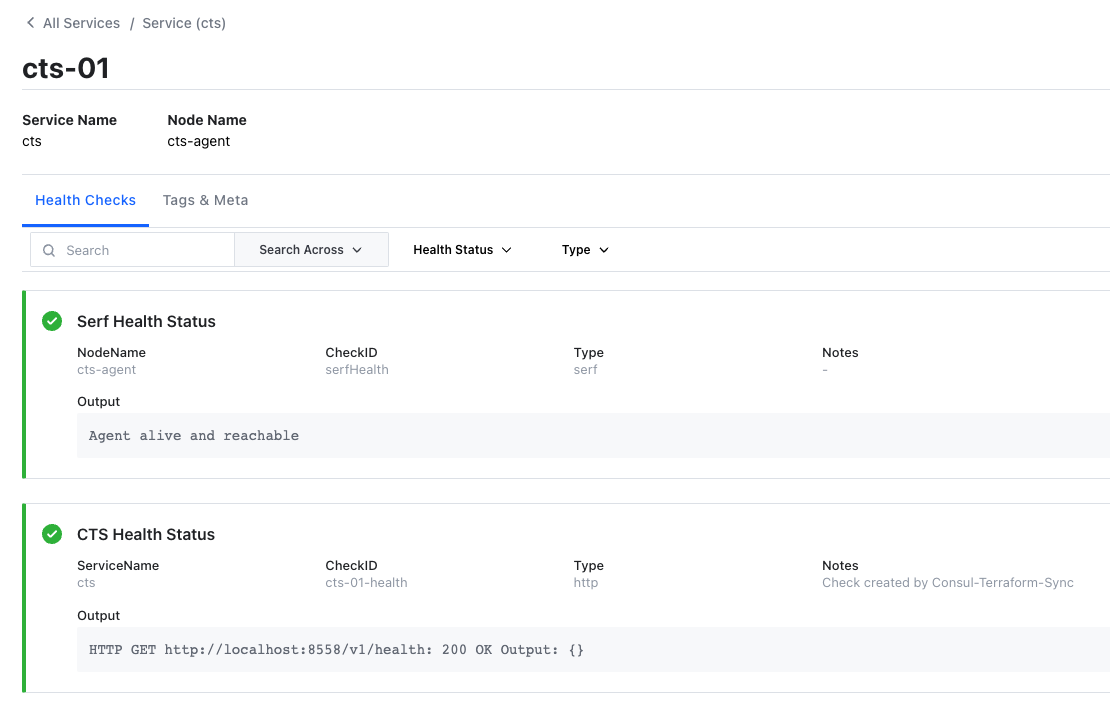
CTS service health check based on the newly introduced Health API endpoint.
Additionally, we are improving CTS discoverability in the CLI. The ‘consul-terraform-sync’ command features opt-in autocompletion for flags, subcommands, and arguments.
»Per-Task Execution Mode with Support for Terraform Cloud Agent
Consul-Terraform-Sync Enterprise is introducing a new capability that enables users to select the Terraform Execution mode per CTS Task, including the “agent” mode for Terraform Cloud Agents.
Terraform Cloud Agents are lightweight agents that establish a simple connection between the user’s environment and Terraform Cloud, which allows for provisioning operations and management. The agent polls Terraform Cloud or Terraform Enterprise for any changes to CTS-managed workspaces and makes the changes locally.
With this capability, users do not need to allow public ingress traffic to their on-premises infrastructure resources when executing a CTS-driven workflow with Terraform Cloud.
Users can now enable Terraform Cloud Agent support by configuring the Terraform execution mode per CTS Task to “agent”, as shown here:
task {
name = "terraform_cloud_agent_task"
module = "mkam/hello/cts"
condition "services" {
names = ["api", "web"]
}
terraform_cloud_workspace {
execution_mode = "agent"
agent_pool_name = "test_agent_pool"
}
}
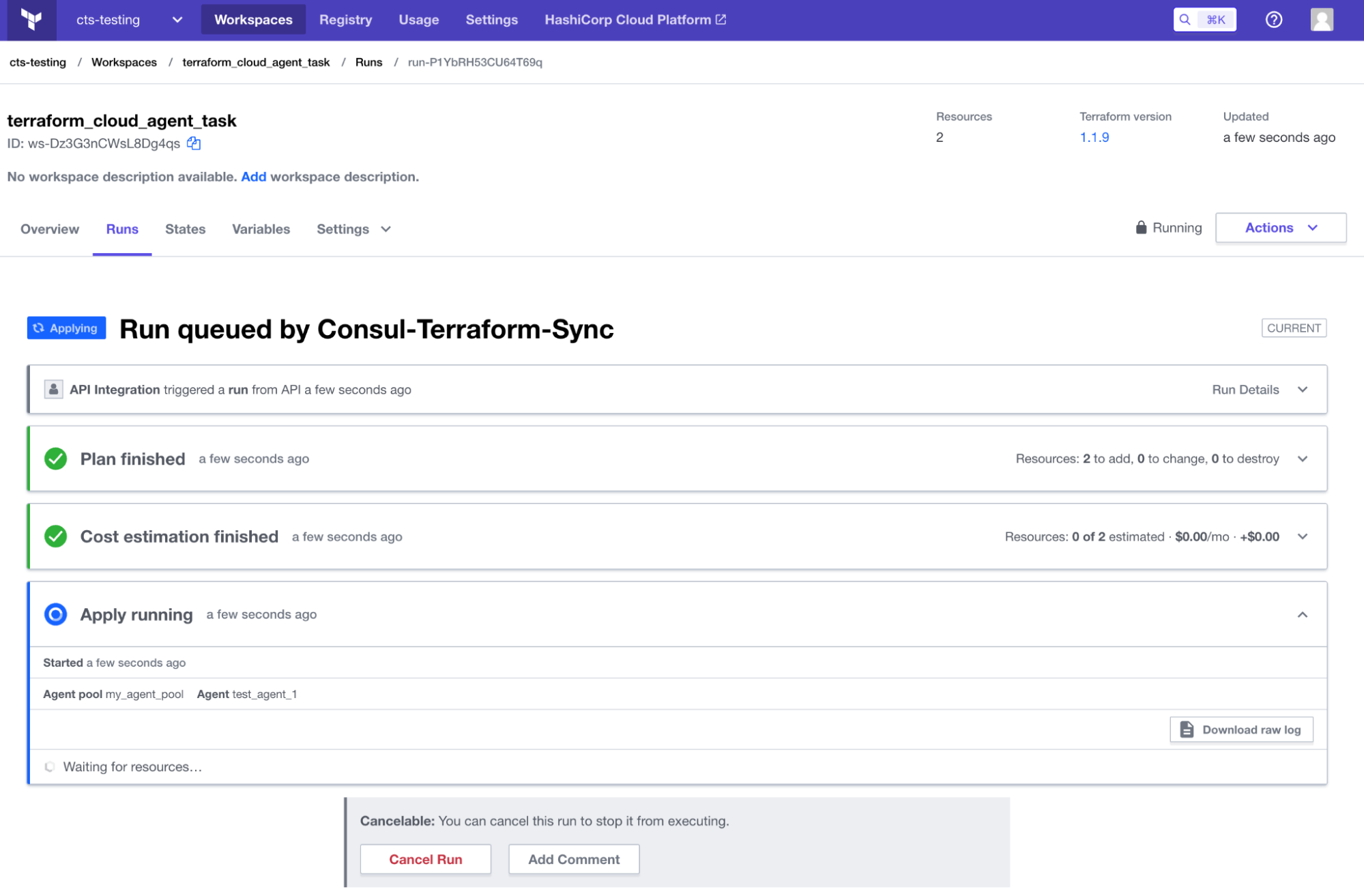
Terraform Cloud run on a cloud agent, triggered by Consul-Terraform-Sync.
»Now Supporting HCP Consul
Consul-Terraform-Sync Enterprise now also supports HCP Consul. With this support, CTS users can subscribe to services and key-value stores on their cluster managed by HCP Consul. CTS Enterprise will also perform license management to keep users’ licenses in sync with their HCP Consul or Consul enterprise deployment. Please check out this Learn guide to enable CTS enterprise with HCP Consul.
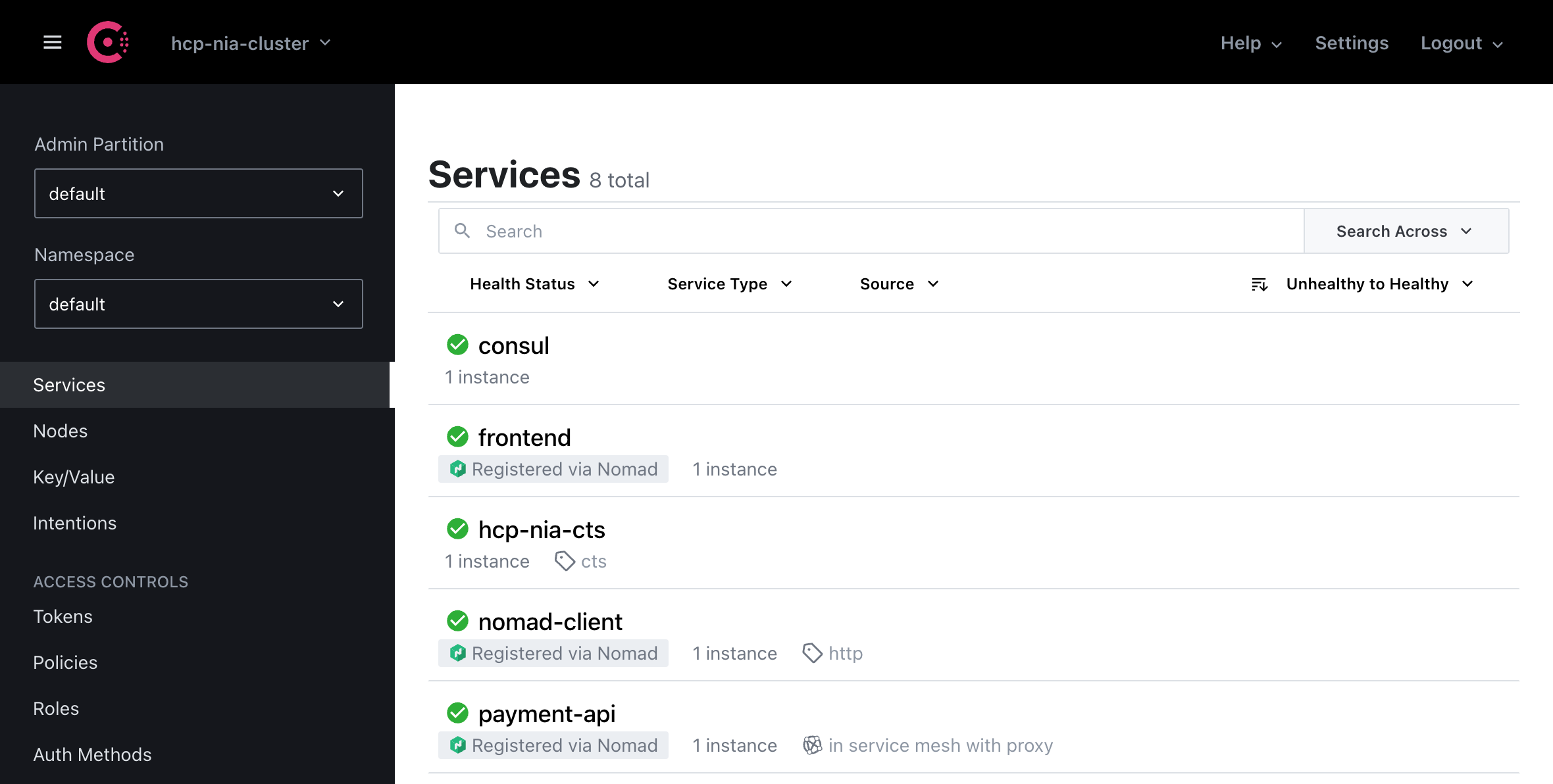
CTS registered as a service with an HCP Consul cluster.
The Secure Consul-Terraform-Sync tutorial shows how to integrate HCP Consul with CTS v0.6.0.
»CTS Ecosystem Integrations
Our growing practitioner and partner ecosystem play a critical role in helping users automate manual networking tasks. We are pleased to announce new additions:
»Partner Ecosystem
DNSimple provides essential services for every internet-connected system: domain registration, managed DNS, a powerful automation API, one-click DNS services, and SSL certificates. With the DNSimple Network Infrastructure Automation (NIA) Consul integration, operators can automate DNS records provisioning that reacts to changes in the service mesh. When a service is registered or updated, a DNS A record with the service IP address is created or updated in the domain specified by the operator. Similarly, when a service is removed from the mesh, the associated DNS records are also removed from the domain.
»Practitioner Ecosystem
We are seeing CTS used in a variety of use cases, from dynamic load balancing for public cloud networking services to automated firewalling with on-premises technologies. Leverage these community-built CTS modules, or let them inspire you to build your own:
- Manage Policy groups on NSX-T Distributed Firewall
- Listener Rules and Target Groups Updates to AWS ALB
- Manage AWS Tags Automatically Based on Values from the Consul KV Store
- Dynamically Create and Update Cisco ACI Endpoint Security Groups
»CTS 0.6 Demo Video
In this 14-minute video, HashiCorp’s Hariram Sankaran shares important details about the new features in Consul-Terraform-Sync 0.6:
»Learn More
Check out these HashiCorp Learn tutorials to help you get started with CTS:
- Network Infrastructure Automation with Consul-Terraform-Sync Intro
- Secure Consul-Terraform-Sync for Production
- Consul-Terraform-Sync and Terraform Enterprise/Cloud Integration
- Build a Custom Consul-Terraform-Sync Module
You can find more CTS tutorials by visiting the CTS tutorial collection at learn.hashicorp.com.
We invite you to try out CTS 0.6 and give us feedback in the issue tracker. You can also stay up to date on CTS by following our public roadmap or checking the release notes. For more information about Consul, please visit the Consul product page.









