Today we’re pleased to announce the general availability of the Consul API Gateway version 0.2. This release includes an update that allows users to better control how traffic is routed between Kubernetes namespaces. Previously, users could route requests from the API Gateway across various namespaces without providing any sort of explicit permissions. While this meant that any service connected to the service mesh was reachable, it didn’t allow users to set the more granular restrictions or permissions that they may expect. In this blog post, we’ll explain how Consul API Gateway 0.2 solves for this challenge using cross-namespace reference policies.
»Enforcing Cross-Namespace Communication
In the Kubernetes Gateway API specification, an administrator of a namespace needs to create ReferencePolicies in order for their services to receive traffic routed to them from gateway routes in other namespaces. This can help prevent things like accidentally exposing a service externally when it shouldn’t be. As an example, here is a ReferencePolicy that is created in the same namespace that the services are in and allows them to receive traffic from an HTTPRoute in the prod-gw-ns namespace:
apiVersion: gateway.networking.k8s.io/v1alpha2
kind: ReferencePolicy
metadata:
name: allow-prod-traffic
namespace: the-services-ns
spec:
from:
- group: gateway.networking.k8s.io
kind: HTTPRoute
namespace: prod-gw-ns
to:
kind: Service
ReferencePolicies are used in conjunction with the various route types supported by the API Gateway: HTTProutes and TCProutes. One important note: ReferencePolicies can support only one from and to section, so if you intend to create enforcement rules for more than two namespaces, you will need to create policies for each combination of namespaces. This creates a better security model, ensuring that all communication between namespaces is authorized. The diagram below illustrates this architecture:
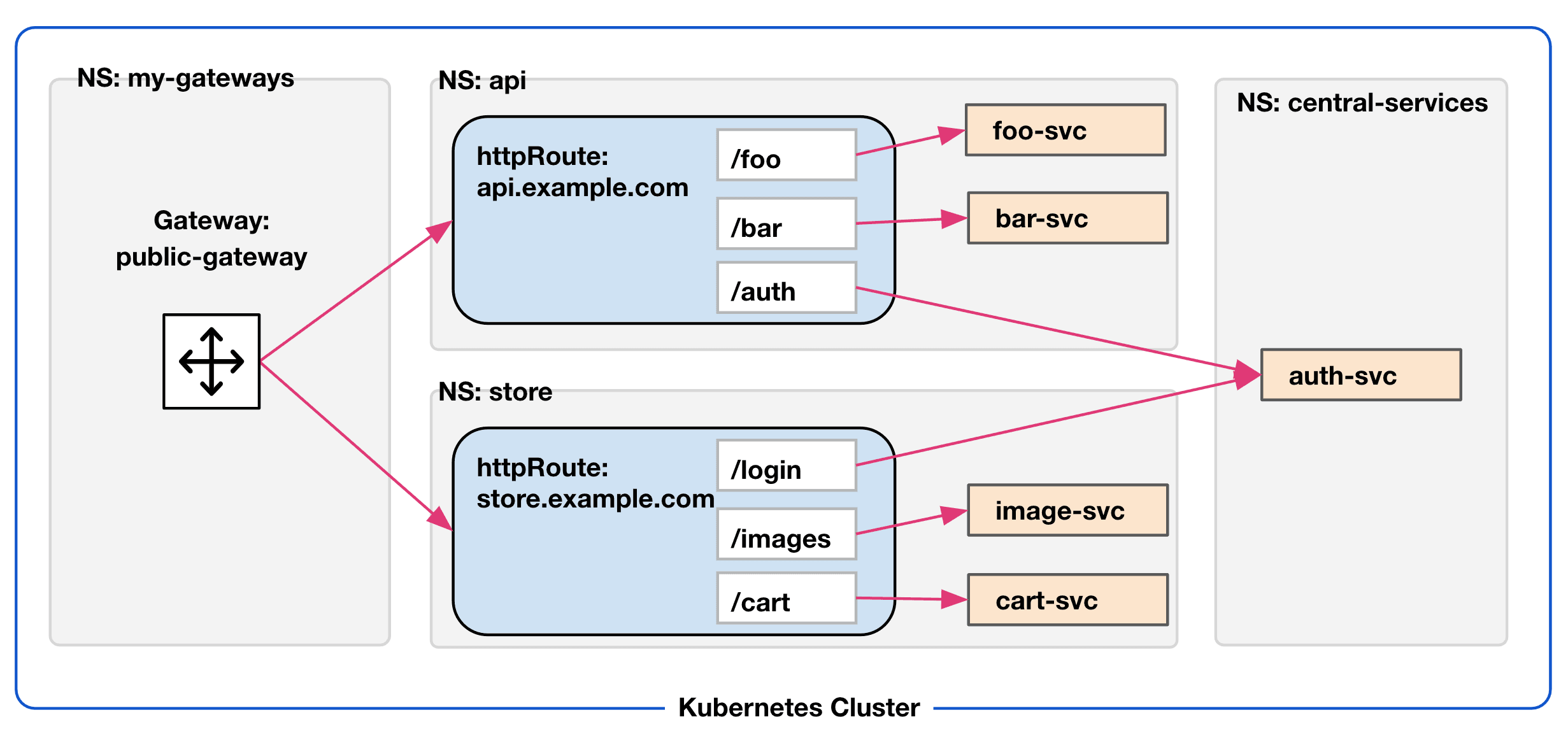
»Next Steps
Version 0.2 of the Consul API Gateway is now generally available for all users. To get started, use the latest Consul Helm chart and be sure to install the most recent version of the Consul API Gateway CRDs. For more information, please visit the Consul API Gateway documentation.









