Today we are announcing the release of HashiCorp Boundary 0.19, now available for HCP Boundary, Boundary Enterprise, and Boundary Community Edition. This release further expands automatic host discovery and simplifies Boundary worker filter configuration. Coupled with our recent announcement of transparent sessions, these features reinforce our continued commitment to make the user experience as simple as possible for both administrators and end users.
»What is HashiCorp Boundary
HashiCorp Boundary is an identity-based secure remote access platform that makes it easier and more secure for end users to remotely access infrastructure resources (Linux/Windows hosts, databases, web applications, Kubernetes clusters, etc) compared to traditional methods using VPNs and bastion hosts. In addition to creating access connections for end users, Boundary also centrally handles credential retrieval and injection into sessions, resulting in a passwordless experience. Boundary helps organizations meet ISO, SOC 2, and several other compliance standards by improving their overall security posture with least-privilege access to infrastructure resources and detailed user activity logging. Activity logging includes recording detailed commands executed by each user during an SSH session.
»Boundary auto-discovery for Google Cloud
The dynamic host catalog is a Boundary feature that automatically discovers virtual machine resources in the public cloud and syncs the latest information (i.e. names, IP addresses, etc.) with Boundary’s own catalog. This feature is already supported for EC2 instances on Amazon Web Services (AWS) and virtual machines on Microsoft Azure, but is now extended to support Compute Engine VM instances on Google Cloud Platform (GCP).
In the public cloud, resources are constantly being deployed, destroyed, or changing IP addresses. This makes it challenging for administrators to manually keep their privileged access management (PAM) tools up-to-date with the latest changes. Some PAM tools have agents installed on virtual machine resources that help reflect the latest changes, but that still requires a non-trivial amount of effort for administrators to install, maintain, and upgrade agents.
Fortunately, Boundary was developed specifically for modern environments where resources are dynamic and ephemeral. Boundary dynamic host catalog takes a different approach to maintaining an up-to-date catalog of virtual machines running in AWS, Azure, or GCP. Instead of requiring agents, Boundary automatically discovers virtual machines based on cloud-native tags or labels configured within a given cloud service provider’s environment. This drastically reduces the burden on administrators by removing the task of managing agents or manually updating catalogs.
This is useful throughout the lifecycle of virtual machines because Boundary will also automatically remove virtual machines from its catalog when the virtual machines are destroyed or when tags/labels are removed.

GCP is now an option in the HCP Boundary UI when creating a dynamic host catalog.
»Worker filter configuration improvement
In the latest 0.19 release, the admin UI has made it significantly easier to select the desired Boundary workers to route traffic for any given target resource. This reduces the potential human error when configuring Boundary, especially for new administrators.
»What are workers?
When end users connect to their desired target resource, behind the scenes, Boundary is performing the connections by routing traffic through one or more Boundary proxies called workers. An organization may have target resources in different availability zones, regions, networks, or even clouds, and therefore would have multiple workers to route traffic to each respective target. Boundary’s admin UI allows administrators to configure which worker(s) should be used to route the connection for each target resource.
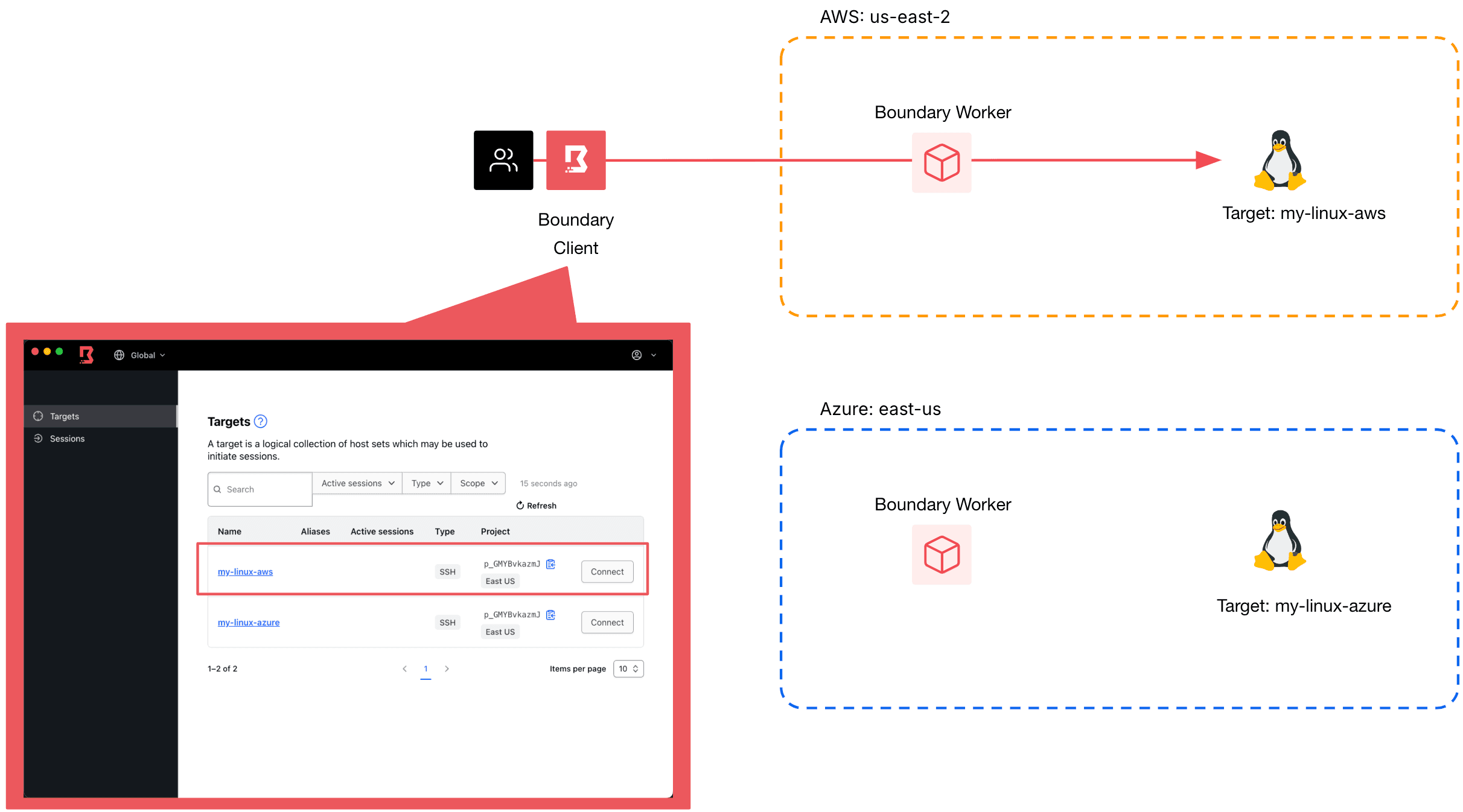
User connecting to Linux host in AWS is routed through a worker that is also in AWS.
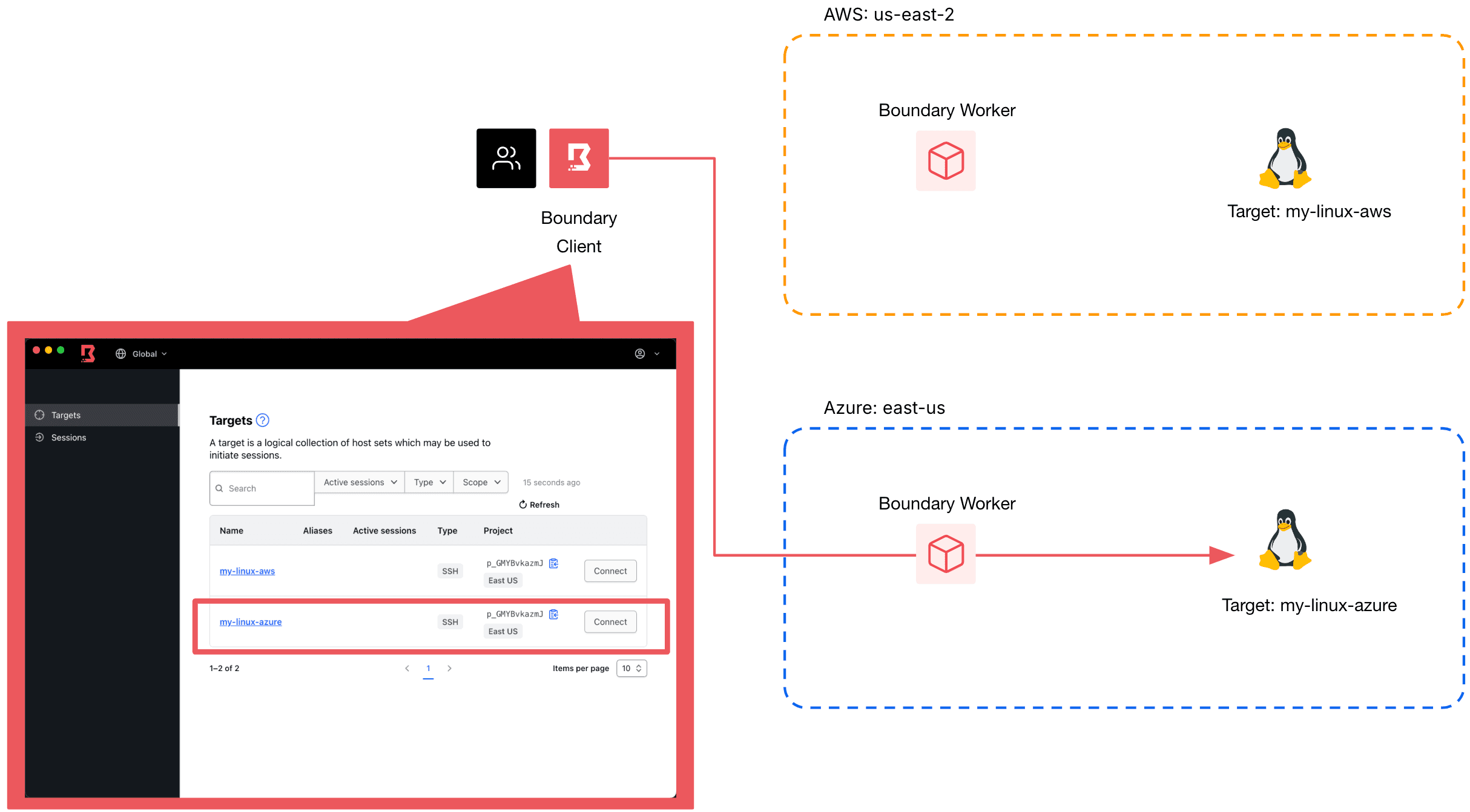
User connecting to Linux host in Azure is routed through a worker that is also in Azure.
Prior to this latest release, the way workers were selected (aka “filtered”) was not as intuitive and required administrators to use a specific boolean expression that was susceptible to human error. A similar challenge exists when workers are selected to proxy connections between Boundary and a private Vault instance, or when workers are selected to connect to storage buckets to store session recordings.
»Worker filter generator
The latest admin UI addresses these challenges by providing a worker filter generator to help administrators create the correct boolean expression when workers need to be selected for various functions. The administrator simply provides a name or tag that matches their desired worker(s), and the boolean expression will be generated for them. The new worker filter generator is available when configuring:
- Targets: Generate boolean expression to select desired workers to proxy end user connections to targets.
- Vault credential store: Generate boolean expression to select desired workers to proxy connection between Boundary and Vault.
- Storage buckets: Generate boolean expression to select desired workers to connect to storage buckets for session recording storage.
This new worker filter generator simplifies the configuration process in the admin UI, reducing administrative time and the potential for human error.

The Boundary admin UI shows a Boundary worker with multiple tags.

The Boundary admin UI shows a target worker filter generator with key and value fields populated with corresponding tags for the desired Boundary worker. A boolean expression is generated to select a Boundary worker that routes to a target.
»Try dynamic host catalog yourself
Boundary 0.19 is generally available today for Boundary users on HCP Standard, HCP Plus, Boundary Enterprise, and Boundary Community. To learn more about dynamic host catalog, visit our documentation.
For existing Boundary users:
- For self-managed versions, download Boundary 0.19.
- Watch this tutorial to learn how to upgrade self-managed versions of Boundary.
- HCP Boundary users will be notified and admins can start the update immediately. Updates are automatic after 30 days of release.
For new Boundary users:
- Sign up for a free HCP Boundary account.
- Download the free Boundary Desktop client.
- Go through our tutorial on getting started with HCP Boundary.
- To request a Boundary Enterprise trial, contact HashiCorp sales.
If you’d like to try a quick self-managed test run of basic Boundary features, you can also download and use Boundary Community for free. For a full list of changes in Boundary Community, read the GitHub changelog.








