Today we are announcing the release of HashiCorp Boundary 0.17, which improves the management of Boundary tags and roles, enhances the way unhealthy workers are handled, and supports more storage options for session recordings. These upgrades improve the user experience for administrators and end users, and offer more flexibility for customers to use the S3-compatible storage of their choice.
Boundary is a modern privilege access management (PAM) solution that simplifies and secures remote user access with consistent workflows in any cloud or on-premises environment. With its latest release, Boundary continues to evolve into an even simpler, more flexible solution for dynamic resources.
»Improved admin and user experience
As part of an ongoing initiative to continually improve the user experience, we’ve made multiple enhancements to simplify the management for admins. We’ve also automated worker-failure handling which results in an improved experience for end users.
»Centralized tag management for workers
With Boundary 0.17, it’s now easier to add, remove, and update worker tags. We’ve enhanced the Boundary UI to make it easier and more visually intuitive for admins to manage worker tags from a central location.
Workers are a core part of the Boundary architecture, performing several key functions including recording SSH sessions and proxying session connections between end users and target resources. Workers perform these functions based on tags assigned to each worker. For example, if customers have multiple target resources residing in different clouds, they can determine how they’d like the end user sessions to be routed to each target by selecting workers (referred to as “filtering”) with specific tags. Workers with tags that match the target filter will proxy the connection for the corresponding target.
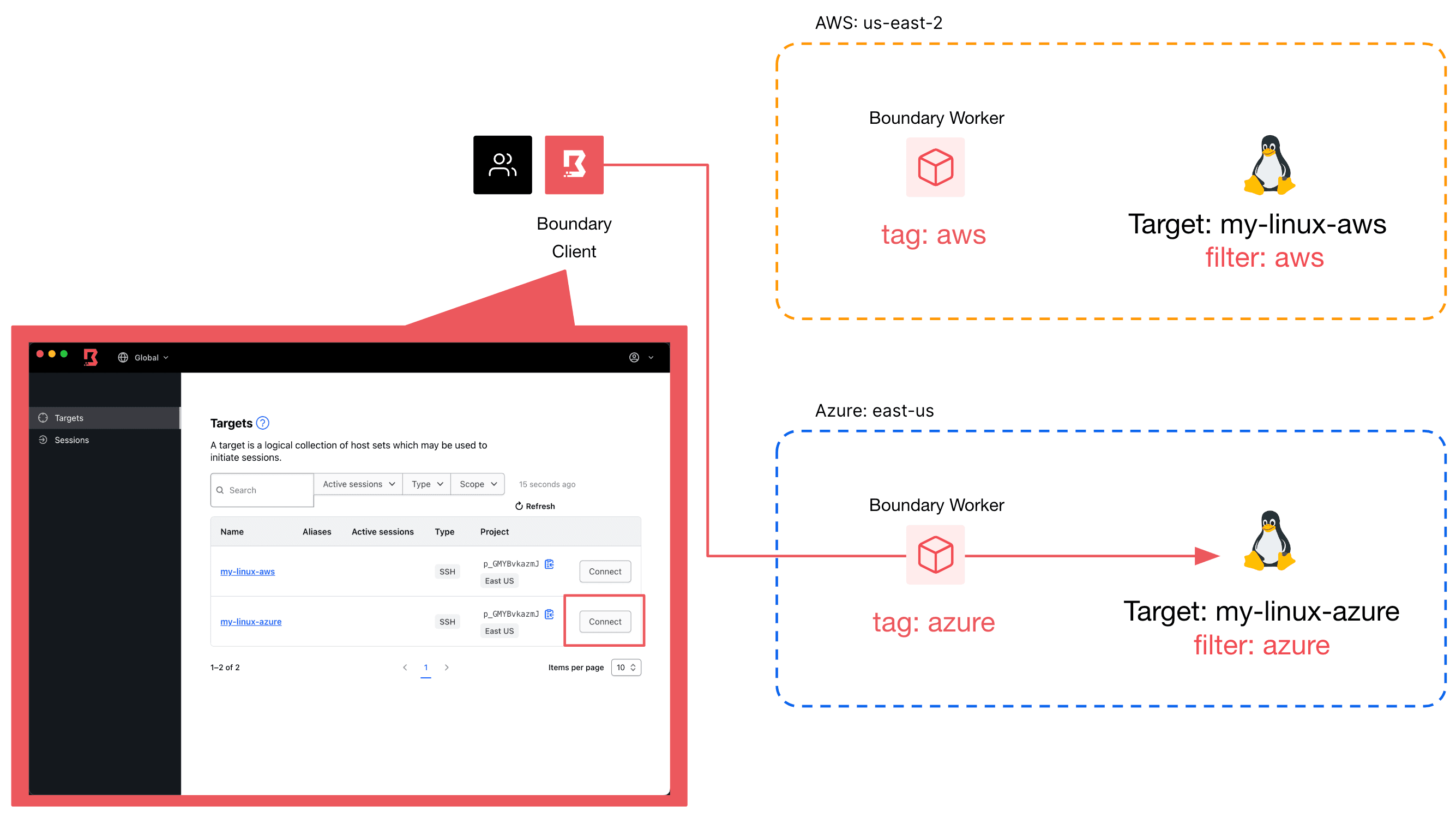
The diagram above shows that when an end user selects a target for their desired connection, traffic is routed through Boundary workers with tags that match the target’s filter.
Prior to Boundary 0.17, admins had two options to add, remove, or update tags for each worker. They could log onto each individual worker and update the worker configuration file. Or they could use the Boundary CLI or API to edit tags. While both options are easy to use, we wanted to streamline the process to be more intuitive.
Now, admins can edit worker tags directly from the Boundary UI. This capability also provides a more consistent user experience for all the Boundary management interfaces, resulting in a more simplified and efficient way to manage tags from a centralized location.
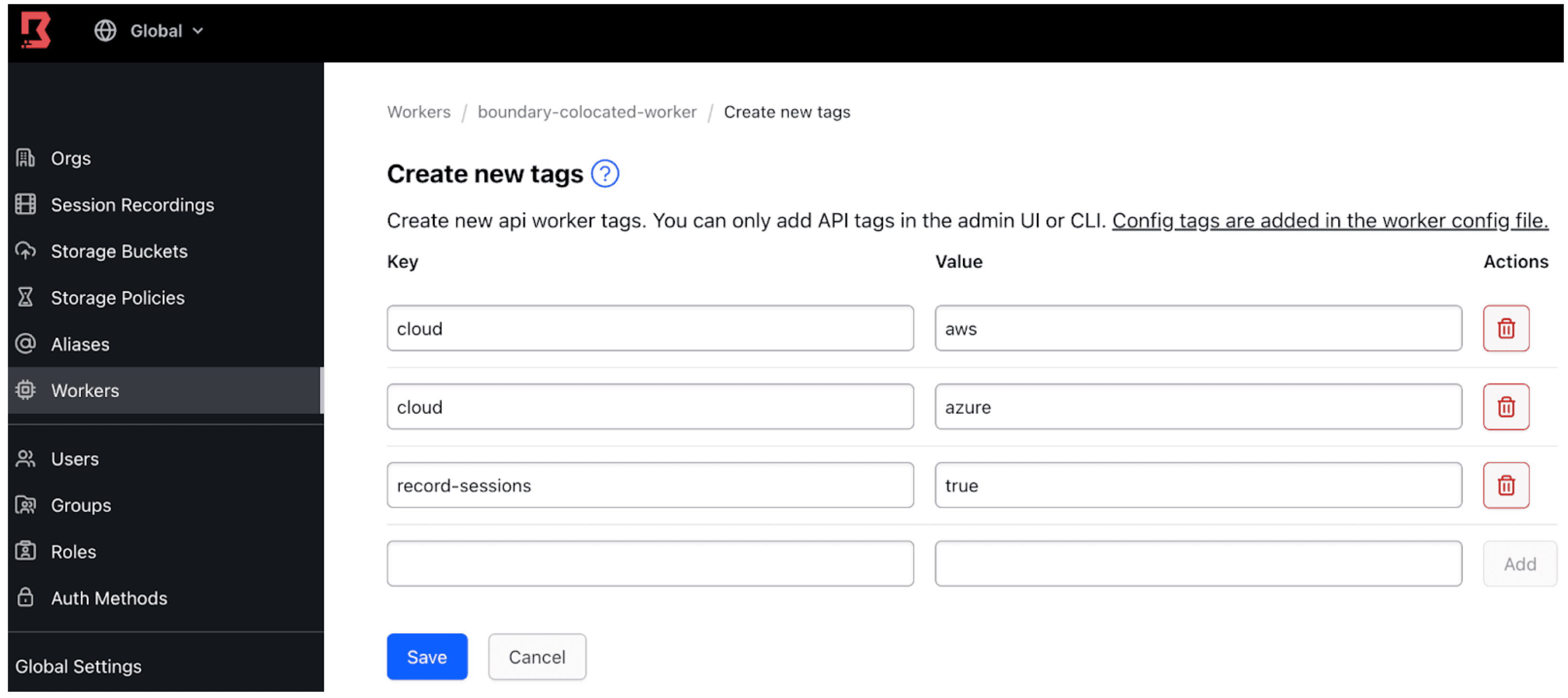
The Boundary UI now allows admins to add, remove, or update tags for Boundary workers.
To learn more, visit our documentation on tags.
»Multi-scope roles and inheritance
Multi-scope roles are a new capability that simplify granting permissions to users. Boundary uses a domain model that includes the concept of scopes, which help organize resources within Boundary. For example, you can place your Amazon Web Service (AWS) target resources — VMs, Kubernetes clusters, databases, or others — into a scope. Similarly, you can organize target resources for Microsoft Azure, Google Cloud, and on-premises datacenters into their own scopes. This makes it easier to organize resources and it reduces the attack surface as each scope has a permission boundary isolated from other scopes, creating a defined blast radius.
Boundary roles contain a collection of permissions granted to any user assigned to a particular role. Prior to the 0.17 release, a role could be assigned to only a single scope. To support users who should be allowed to access target resources in multiple scopes, admins needed to create a role for each scope.
Now, you can assign a single role to multiple scopes, making it much simpler to grant permissions to users who need access to resources across multiple scopes. Boundary 0.17 also adds the option to allow inheritance of child scopes. For example, a global scope can have multiple child scopes called ‘orgs’. A role created in the global scope can be configured to apply to the child org scopes. These enhancements will greatly ease the management of Boundary roles and permissions.

Boundary UI now allows roles to be applied to multiple scopes, including child scopes.
To learn more, visit our documentation on roles and permissions.
»Improved worker-failure handling
We've improved the user experience when errors occur related to failed workers. When a user initiates a session to a target that has session recording enabled, Boundary will randomly select workers (with matching tags) to proxy the connection. Before release 0.17, workers with read/write/delete permissions issues related to external storage providers were still eligible to proxy connections, despite eventually failing. Users had to reinitiate the connection until a healthy worker was selected. We’ve now implemented enhancements to handle failed workers with insufficient permissions by removing them from the selection pool upon failure. This reduces the errors presented to the user, resulting in a smoother experience.
To learn more, visit our documentation on worker health.
»Flexible storage options
Boundary customers have a vast array of storage options. Most customers prefer to consume the storage platform that they have already invested in and standardized around. By adding support for more S3-compatible storage options, we’re offering more flexibility to meet the demands of our different customers.
»More storage options for session recordings
Boundary 0.16 added MinIO as a backend storage option to store session recordings. Since MinIO is an Amazon-S3 compatible object storage solution that is also software defined, it can be deployed in any type of environment. This lets customers store recorded files in any cloud or on-premises location.
We’ve now expanded support to the entire range of S3-compatible storage solutions, addressing our customers’ diverse storage requirements and dramatically increasing flexibility. To keep workflows simple and consistent, we leverage the same MinIO plugin, which results in the same consistent configuration steps for any S3-compatible storage.
To learn more about S3-compatible storage configuration, see the Boundary documentation on session recording configuration.
»Get started with Boundary 0.17
For a full list of changes in Boundary 0.17, please visit the Boundary changelog.
Boundary 0.17 is now generally available on all of our offerings: HCP Boundary, Boundary Enterprise, and Boundary Community edition. We’d love for you to try out the new features yourself. Whether you are a seasoned Boundary user, or new to the world of modern PAM, we have plenty of tutorials, videos, and other resources to help you get up to speed.
For experienced Boundary users:
- For self-managed versions, download Boundary 0.17.
- Watch this tutorial to learn how to upgrade self-managed versions of Boundary
- HCP Boundary users will be notified and admins can start the update to release 0.17 immediately. Updates are automatic after 30 days of release. For Boundary 0.17, updates will be automatically installed on August 30, 2024.
For new Boundary users:
- Watch this Getting Started with HCP Boundary video.
- Watch this Introduction to Self-Managed Workers with HCP Boundary video.
- Sign up for a free HCP Boundary account.
- Download the free Boundary Desktop client.
- Go through our tutorial to get started with HCP Boundary.
- To request a Boundary Enterprise trial, contact HashiCorp sales.







