Sentinel is a policy as code framework that is embedded into the enterprise versions of HashiCorp Consul, Nomad, Terraform, and Vault. Sentinel enables DevOps teams to apply fine-grained, logic-based policy controls against their most critical services.
Today, the Sentinel team is pleased to announce the release of the Sentinel Playground.
We have built the Playground so that new and existing customers have access to a zero-install development environment. Now, practitioners can learn and experiment with policy as code in minutes without having to install and maintain runtime environments on their own machines.
The Sentinel Playground is useful for policy as code users of all skill levels:
- For beginners, it includes a real-world policy example out of the box, which provides a great starting point. We’ve also stripped back the contents of the mock data to make the learning process a little simpler.
- Seasoned Sentinel policy authors can use it to quickly prototype functions and rules by bringing their own policies and mock data.
»Sentinel Playground
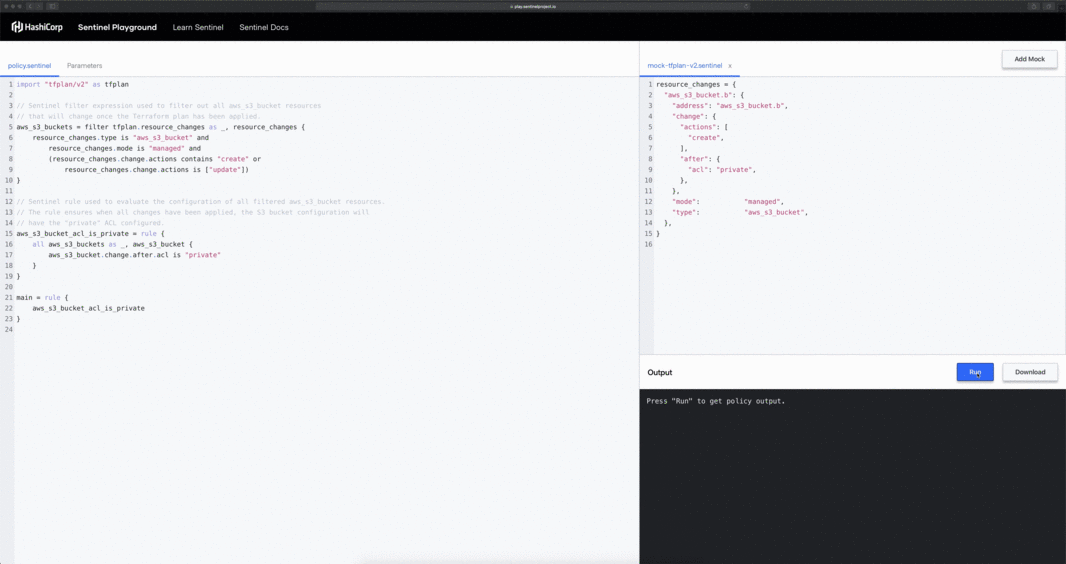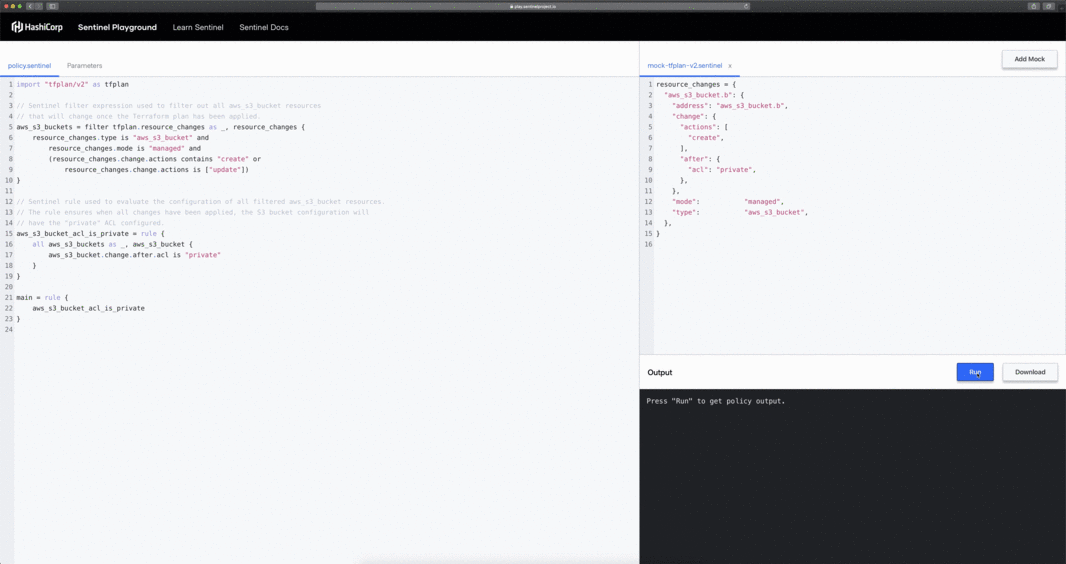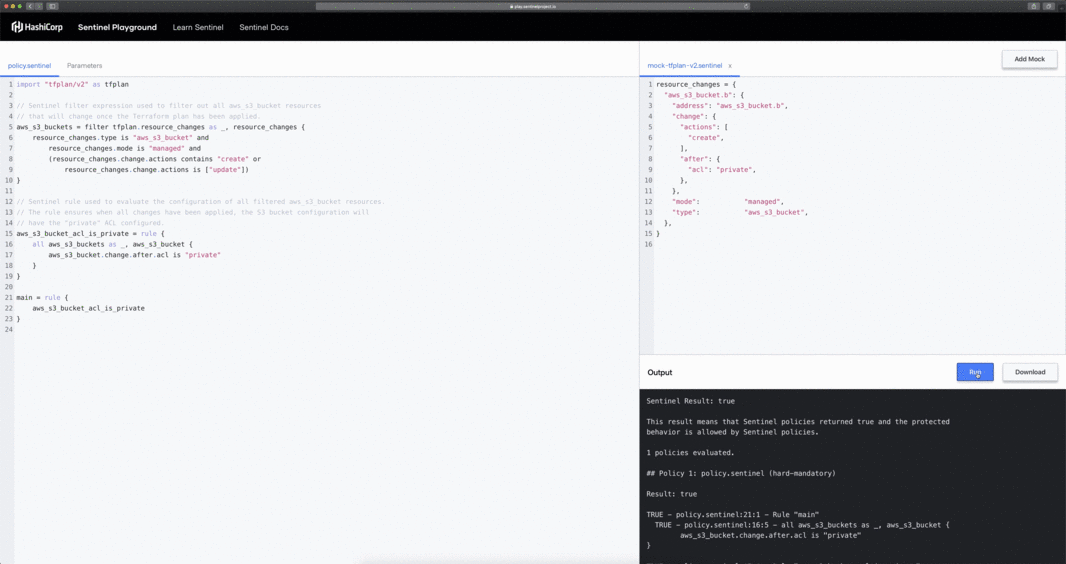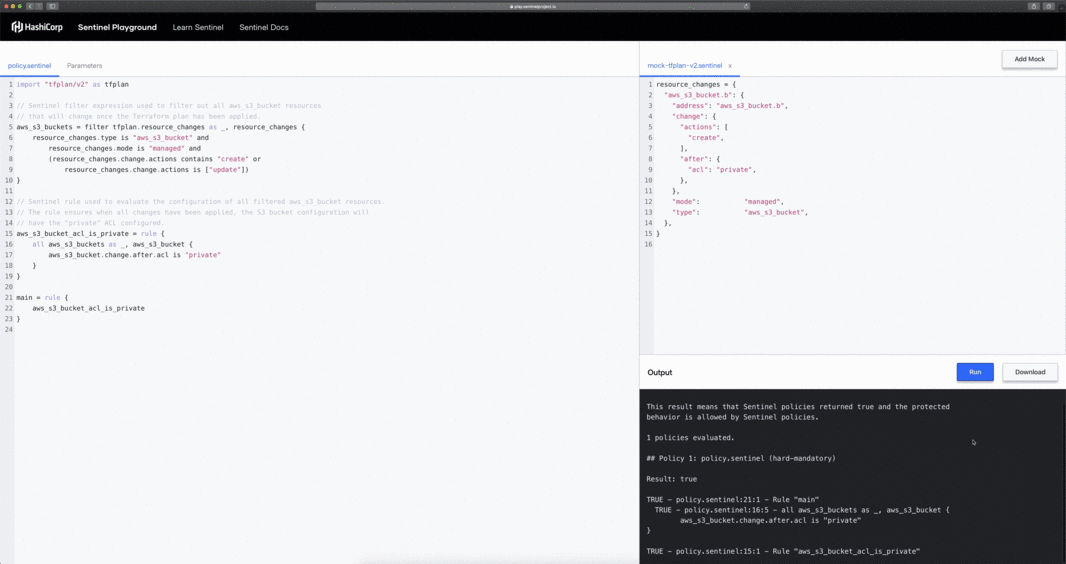
When accessing the Sentinel Playground, you are presented with an example policy definition and all relevant mock data required to successfully evaluate the rules within the policy. As your ability to author policies improves, you can start including more advanced logic-based checks such as those found in the Terraform Foundational Policies Library.
»Hello World!
The Playground comes with an out-of-box policy but you are not limited to using only this policy. You have the freedom to delete all policy contents (including mock data) and start from scratch. This is really useful when you are just trying to familiarize yourself with the Sentinel language and specification.
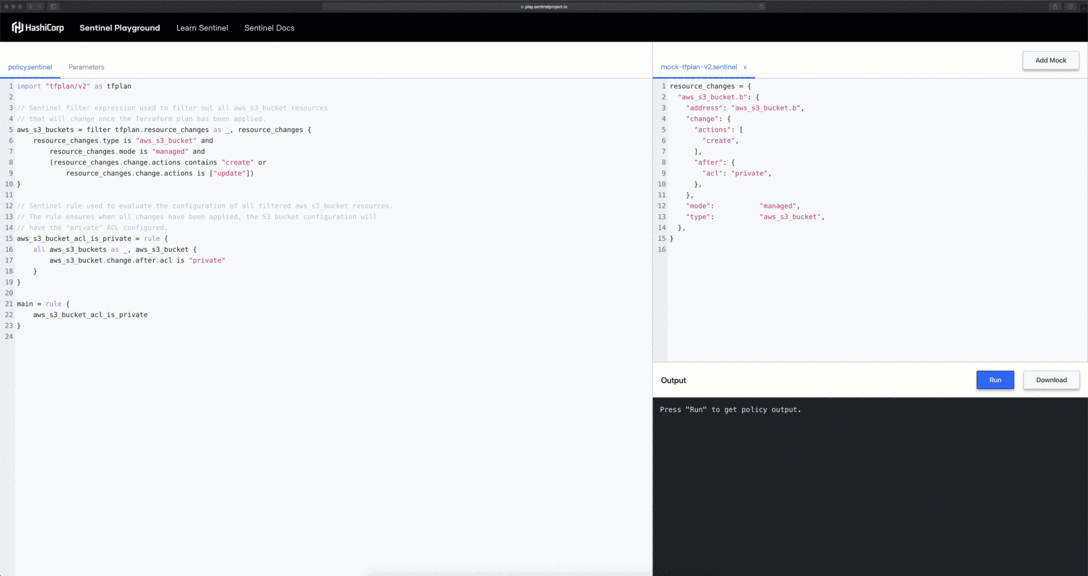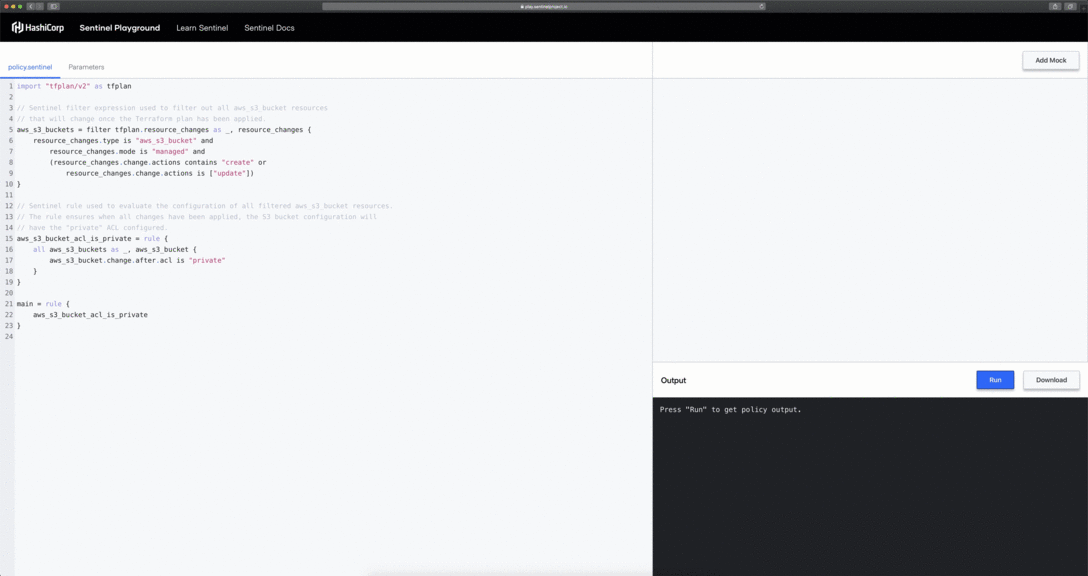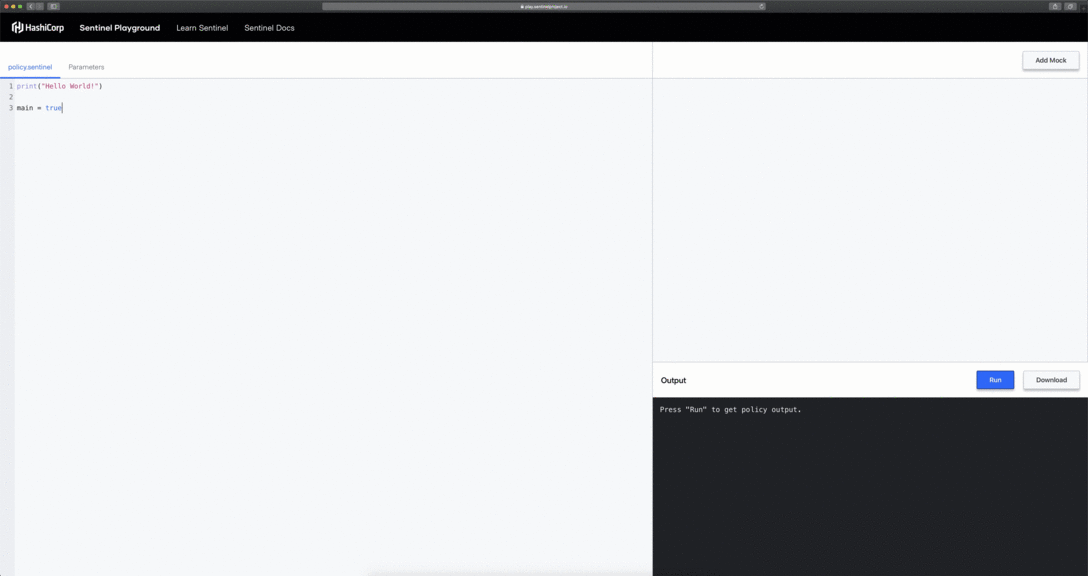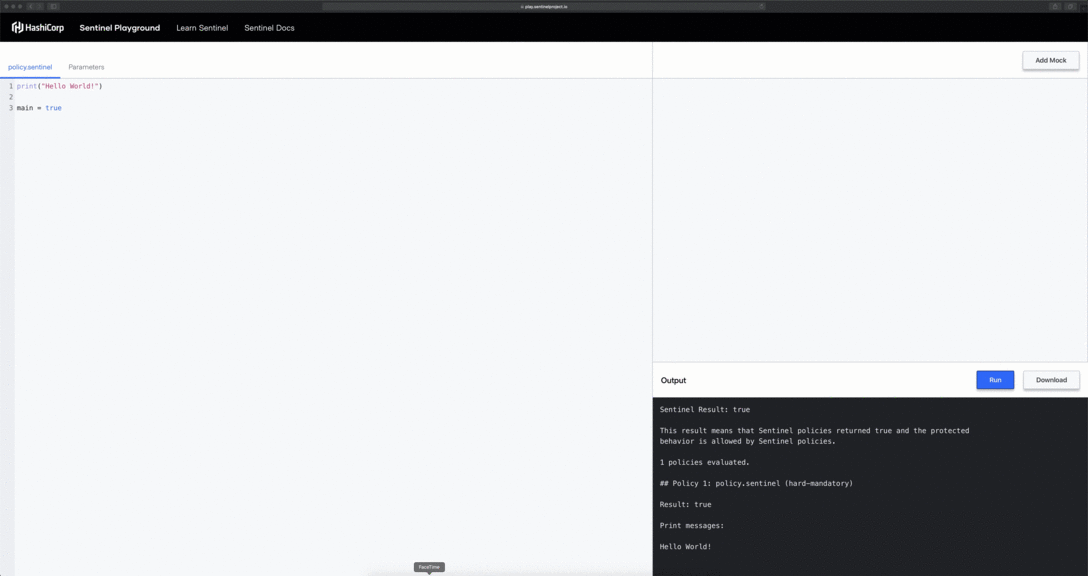
In the above example we have deleted unused mock data and replaced the contents of the policy.sentinel with the following:
print("Hello World!")
main = true
The print function is commonly used to output useful information when debugging policies that may not be behaving in an expected manner.
»Hello Parameters!
The Playground also has first-class support for Sentinel parameters. These help facilitate policy reuse and ensure sensitive values are not hard-coded in a policy.
In the above example, we are parameterizing our “Hello World!” policy.sentinel so that we can dynamically greet an individual by name:
param name
print("Hello", name)
main = true
If you would like to explore Sentinel parameters in more detail, you can do so by referring to the parameters documentation.
»Mock Data
Sentinel has a built-in test framework to validate that a policy behaves as expected. The process of mimicking a production environment is achieved by providing global data and/or imports in the form of a mock. The Sentinel Playground provides the ability to add several mocks so that you can test multiple imports at once.
In the above example, we are adding mock data for the tfrun import so that we can mimic the provisioning operation that is taking place in Terraform Cloud. We do so by adding a mock called tfrun which contains the following:
created_at = "2020-08-01T01:48:37.081Z"
message = "Queued manually in Terraform Cloud"
speculative = false
is_destroy = false
variables = {}
organization = {
"name": "HashiCorp",
}
workspace = {
"auto_apply": false,
"created_at": "2020-08-01T01:48:37.081Z",
"description": null,
"name": "demo-workspace",
"vcs_repo": {
"branch": "demo",
"display_identifier": "hashicorp/demo-workspace",
"identifier": "hashicorp/demo-workspace",
"ingress_submodules": false,
},
"working_directory": "",
}
By amending the imports section of our policy.sentinel to include the following:
import "tfrun"
import "tfplan/v2" as tfplan
And updating main as follows:
main = rule {
aws_s3_bucket_acl_is_private and
tfrun.is_destroy is false
}
We now have the ability to ensure that Terraform Cloud will not perform a destroy operation.
»Available Now
The release of the Sentinel Playground focuses on delivering a core feature set and a single policy example for AWS. In future releases, the Terraform governance team will expand the policies to include Azure and GCP services as well as the ability to share and collaborate with others.
What would you like to see included in the Sentinel Playground? Do you have thoughts on how best to collaborate on policies? If so, please get in touch. We are currently in the early stages of development and are open to any ideas that you may have.
For more information on Sentinel language and specification, visit the Sentinel documentation page. If you would like to engage with the community to discuss information related to Sentinel use cases and best practices, visit the HashiCorp Community Forum.









