We are excited to announce the HashiCorp Terraform Enterprise Module Registry, a service catalog that provides organizations with a self-service workflow to provision any infrastructure.
As organizations deploy more workloads in cloud, operations teams have to ensure that every team in the organization follows safe and efficient provisioning practices. This is best addressed with a service catalog with hardened infrastructure modules. This service catalog allows IT operators to codify, collaborate, and publish modular templates for provisioning cloud infrastructure that can be used by developers or other operators across large organizations. Organizations using the Terraform Enterprise Module Registry can have IT operators serve as experienced “producers,” who create the infrastructure templates, and developers or less experienced operators as “consumers,” who can easily provision infrastructure following best practices with pre-built modules.
At HashiConf 2017 HashiCorp introduced the Terraform Module Registry — a public service catalog for users to publish and use community and verified modules. The Terraform Module Registry has hundreds of available modules across over 80 providers with some of those modules being downloaded tens of thousands of times.
The Terraform Enterprise Module Registry gives organizations a workflow to build, publish, and share their customized, validated, and versioned modules through a private service catalog. This workflow enables every team within an organization to safely and efficiently provision infrastructure. With the new registry, you can:
- Build, validate, version modules with VCS integration
- Publish modules
- Discover modules
- Combine modules using graphical Configuration Designer
»Build, validate, version with VCS integration
Version control systems (VCS) are often the first tools developers reach for when working on code projects. Iterating on a Terraform module is no different. The module source, like any other code, can be stored in a VCS system, and ingressed by Terraform Enterprise automatically when a new version is created.
Terraform Enterprise Module Registry supports a broad set of VCS types and providers — BitBucket Server, GitHub Enterprise, and public GitHub. Support is planned for GitLab and BitBucket Cloud as well.
The Terraform Enterprise Module Registry will automatically create and publish new versions of modules as new tags are pushed to their repositories. Versions in tags are processed as a semantic version, encouraging sound and consistent versioning practice across all modules.
»Publish modules
Publishing a Terraform module in the Terraform Enterprise Module Registry makes that module discoverable and consumable by other members within an organization. Part of the process of publishing a module is specifying the VCS repo it should be sourced from. Terraform Enterprise allows you to specify which configured VCS provider the module exists in, as well as the repository name.
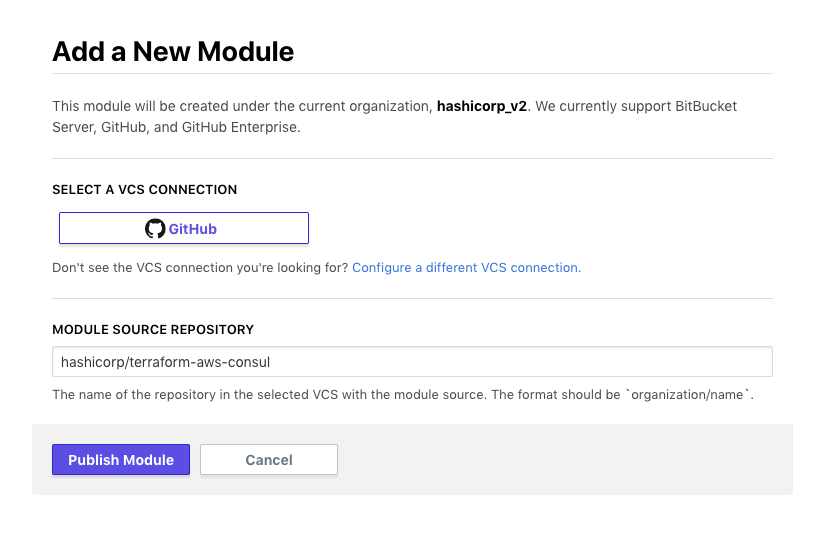
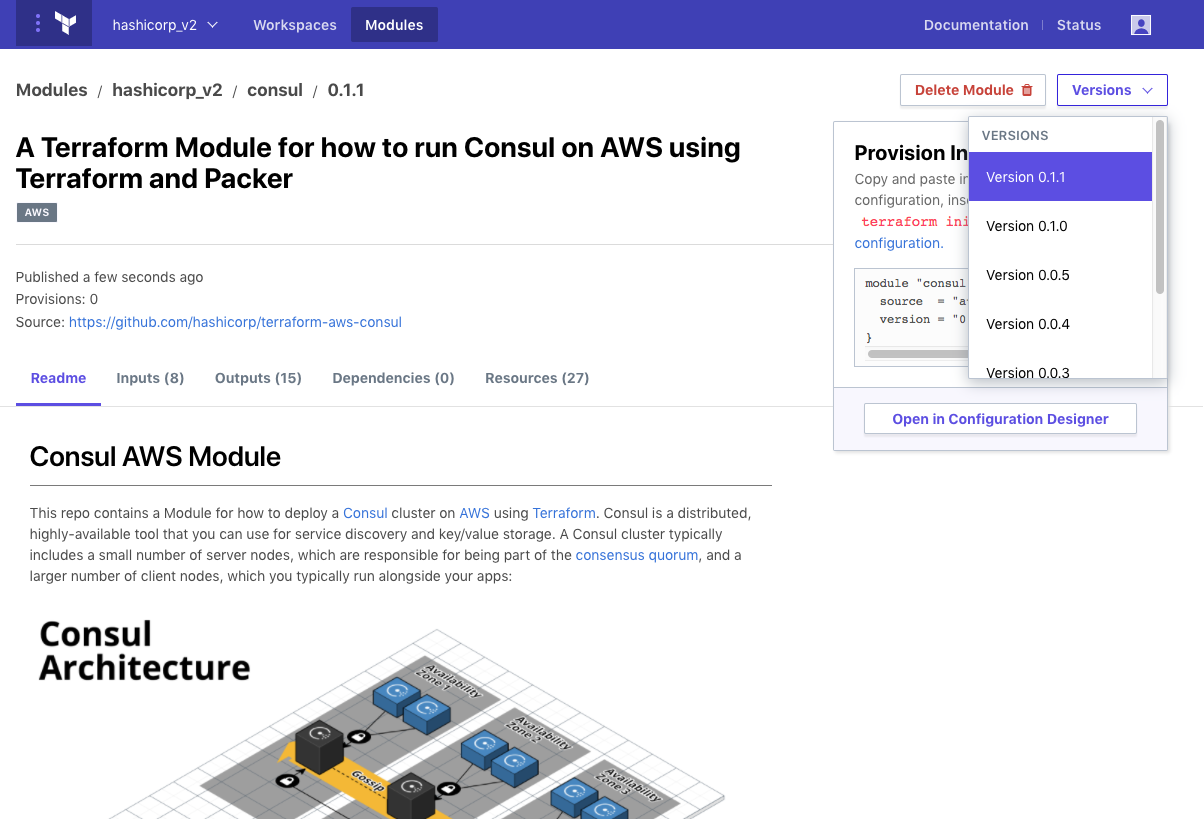
Pressing the “Publish Module” button registers the new module in the registry, and initiates the process of cloning, storing, and parsing the module source code at each tagged version found in the repository. Upon completion the new module will appear in the module list in Terraform Enterprise with its parsed documentation, usage instructions, and a list of all available versions.
»Discover modules
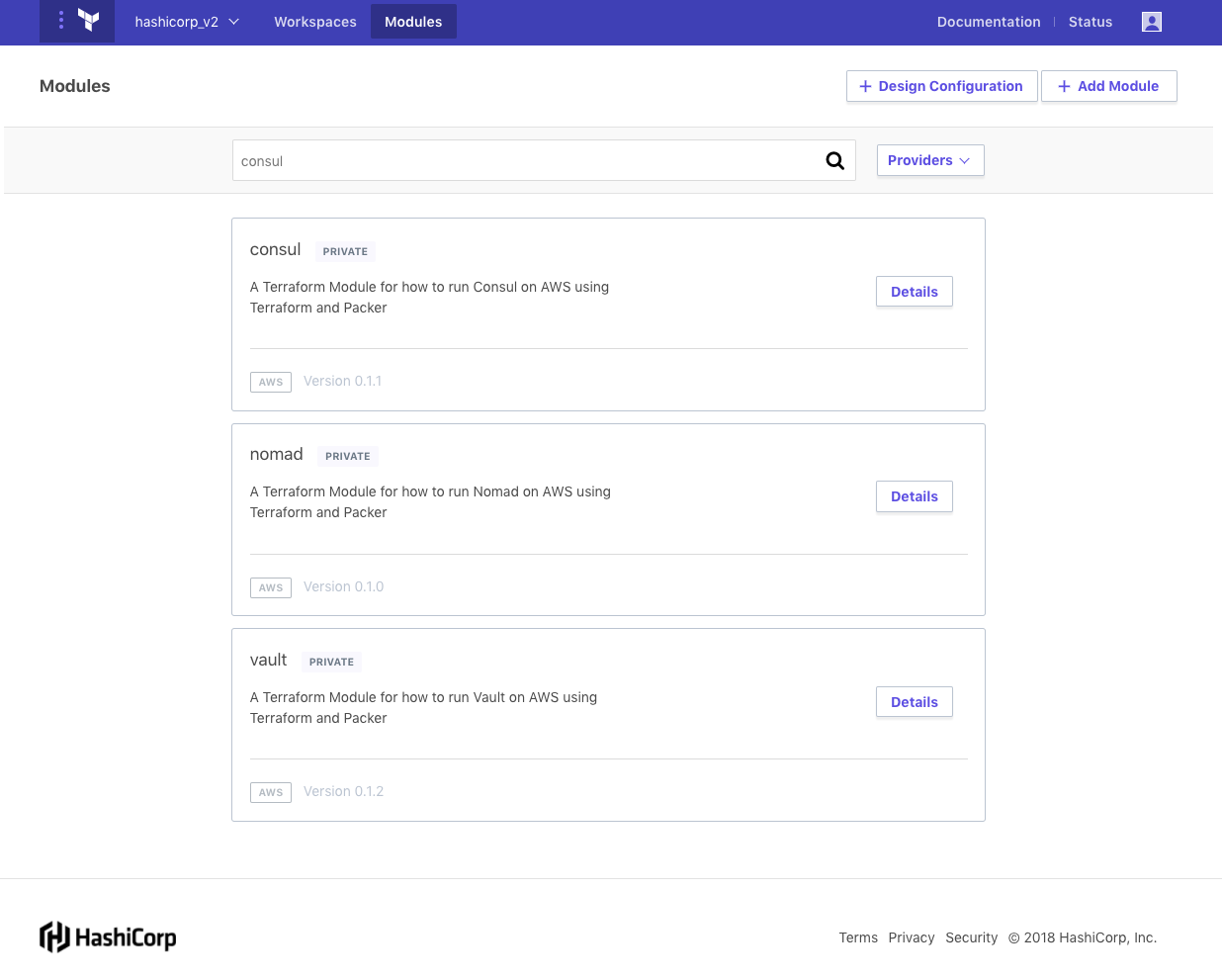
Users often need to provision new infrastructure following standard practices. For example, a developer might want to deploy an application on AWS. The organization can define an auto-scaling group module that codifies the recommended practices for deploying an application at the company. Then a developer just uses that module to create new infrastructure for their application without needing to learn the intricacies of the cloud provider.
Clicking on the “Modules” tab when logged in to Terraform Enterprise brings up an index of published modules within an organization. This list can be filtered down by provider and by a search term.
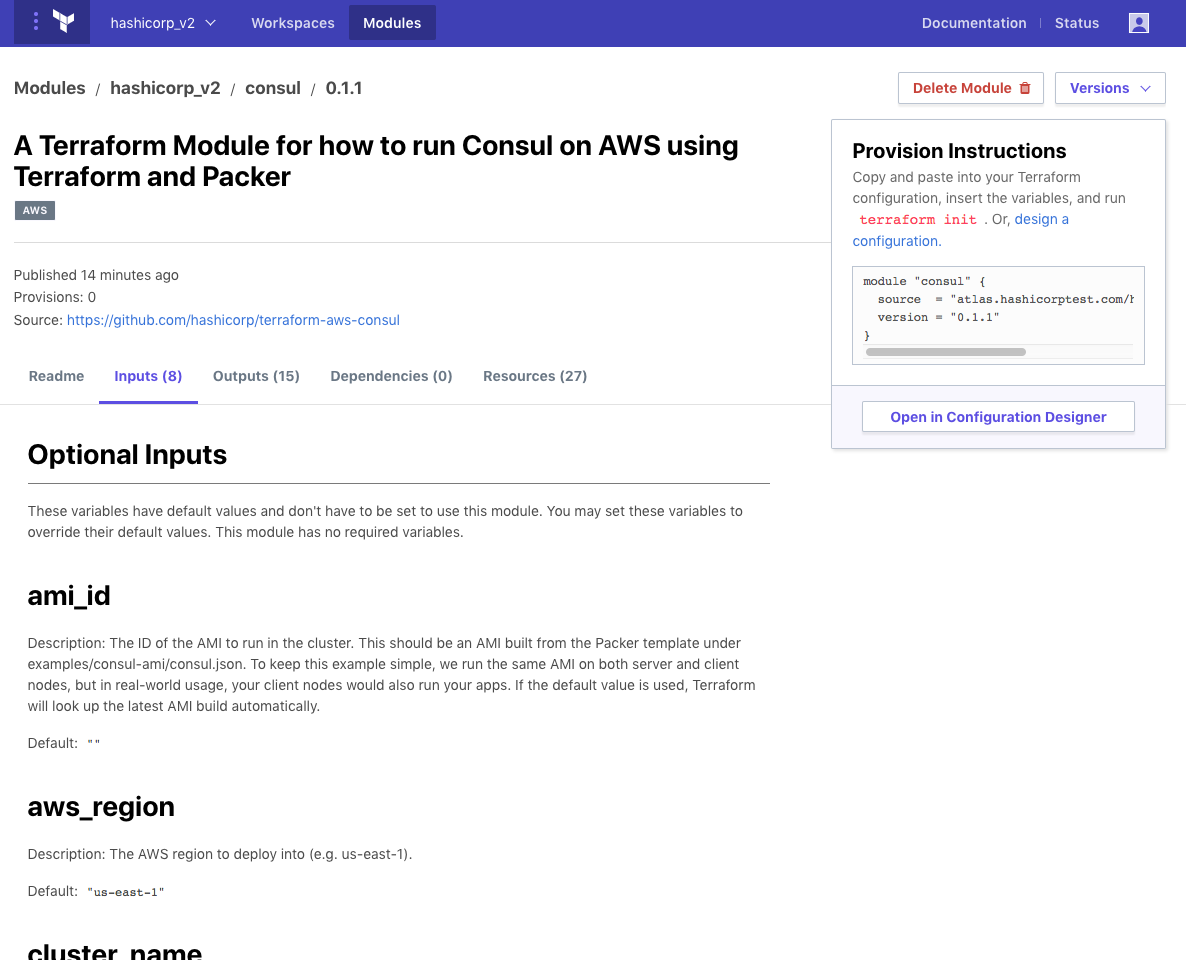
Clicking “Details” on a given module brings up the details page, which includes generated documentation for usage, inputs and outputs, module dependencies, and the types of resources deployed by the module. All of this documentation is automatically parsed and generated at module creation time. This makes a very useful reference for module consumers.
»Combine modules using graphical Configuration Designer
The process of bootstrapping a new infrastructure using Terraform modules is simplified further by a graphical, module-aware Configuration Designer. The primary goal of the Configuration Designer is to make the process of creating the basic Terraform code which imports modules and assigns variable values easy and interactive. Clicking “Design Configuration” from the Modules page brings up the Configuration Designer and displays a list of modules registered within the organization. The user can add or remove modules from the configuration— similar to the user experience of an online shopping cart.
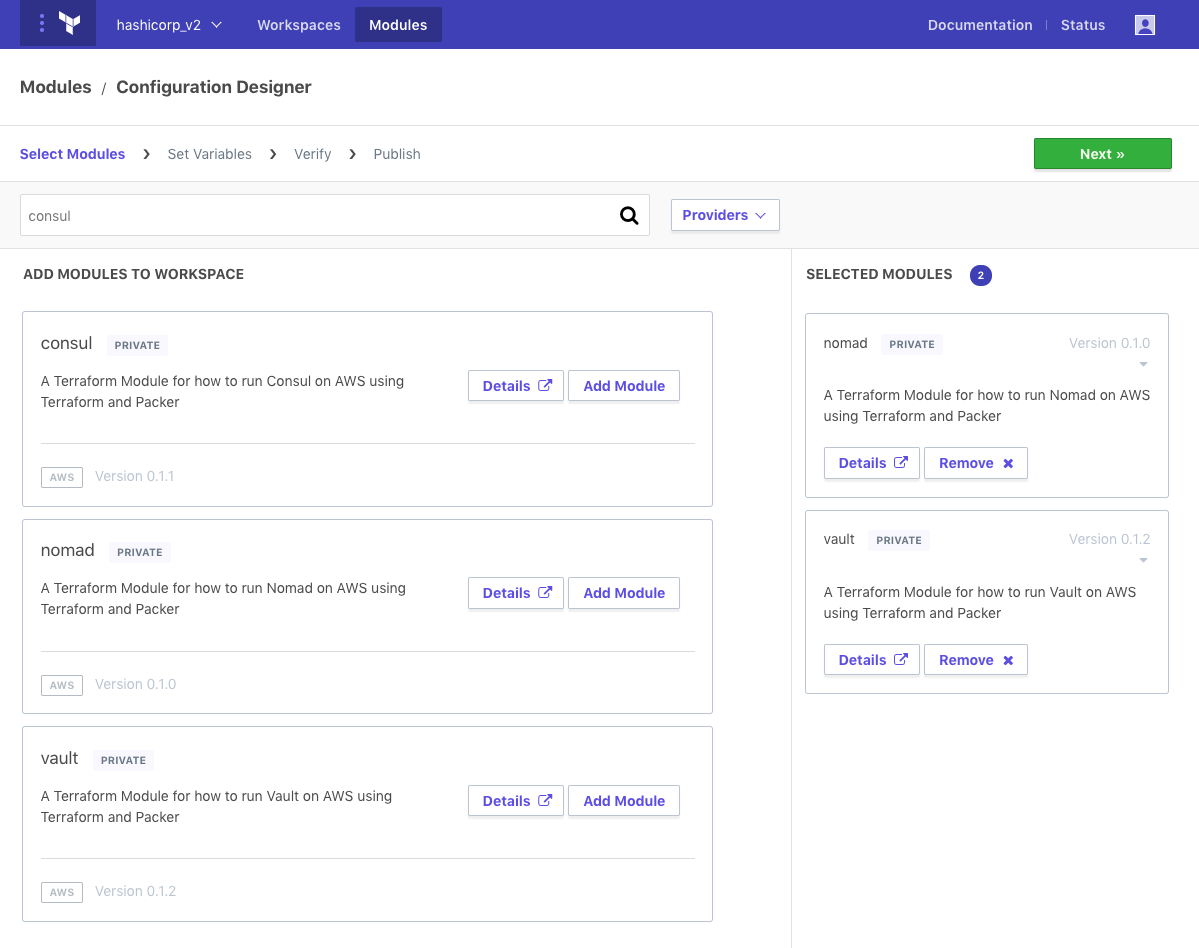
Setting variables is the next step in the Configuration Designer. This step allows the user to specify values as the inputs for each module, and it also goes a step further to allow referencing the outputs from other modules. This enables the user to connect modules together in an intuitive and understandable way. It is also possible to reference outputs from external workspaces which already exist. Both module and workspace outputs can be auto-completed in the UI— the user simply begins typing “${module.” or “${data.” (the Terraform interpolation syntax), and the UI will load and display a list of possible reference values to select from.
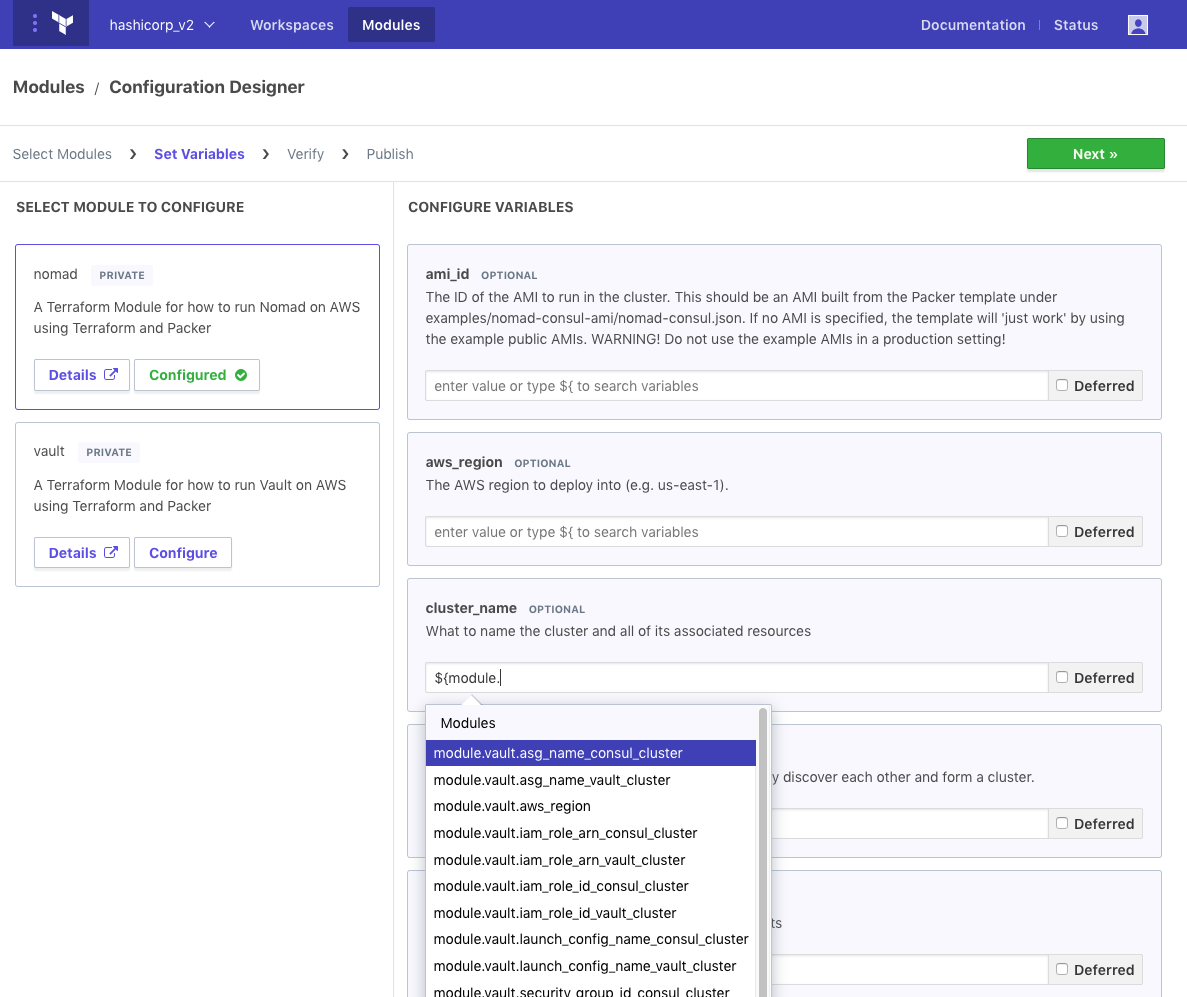
The Configuration Designer takes care to ensure the user has filled all required variables. The user can also opt to defer setting the value of a given variable to runtime. This allows setting the values within a workspace configuration later.
Once all variables have been filled, the user can continue to the final step in the Configuration Designer, which is the actual code generation. The user is presented with a simple text box containing the contents of a “main.tf” file, which imports all of the modules requested in the Configuration Designer and sets all inputs to the requested values.
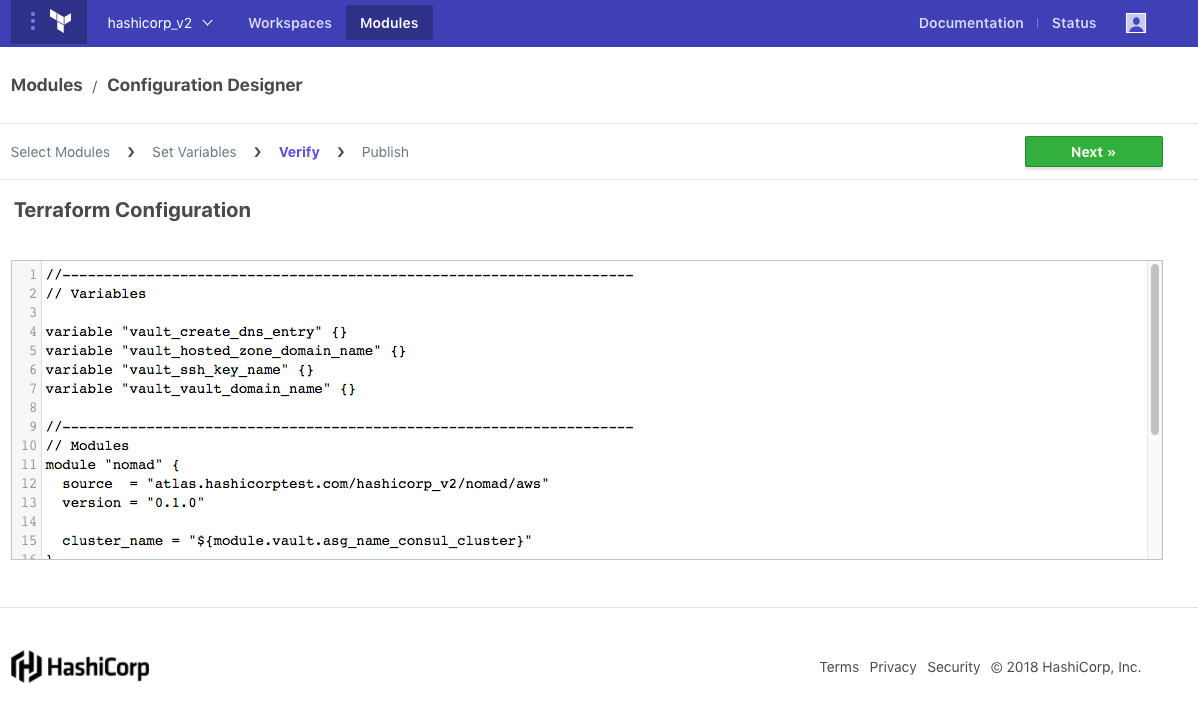
This code can be checked into version control and configured as the source for a workspace configuration.
»Documentation
For more information on the Terraform Enterprise Module Registry workflow, refer to the technical documentation available at https://www.terraform.io/docs/enterprise/registry/index.html.
»Availability
The Terraform Enterprise Module Registry is available to existing customers who are using the SaaS or private install versions. Customers using Terraform Enterprise (legacy) will not have access to Terraform Enterprise Module Registry. To learn more about migrating from Terraform Enterprise (legacy) visit, https://www.terraform.io/docs/enterprise/upgrade/index.html.
»Conclusion
Terraform Enterprise is focused on providing capabilities for organizations to enable safe and efficient provisioning of any infrastructure at scale. This means every team within the organization can be empowered to provision their infrastructure within the constraints required by the business. For more information or to request a free trial, visit https://www.hashicorp.com/products/terraform.








