There are many security challenges to consider when running an infrastructure provisioning workflow based on infrastructure as code. Assessing who has access to what information at every step of the workflow should be a primary focus. For example, state files can contain information such as passwords or private keys and, in many cases, should be considered sensitive. We recommend securely storing state files remotely through a backend, like Terraform Cloud, which offers encrypted transmission and storage. However, users can still obtain and reference state information, even without explicit permission, by using the terraform_remote_state data source.
With a new Controlled Remote State Access feature in Terraform Cloud and Terraform Enterprise, users now have a new way to establish granular controls for state accessibility.
HashiCorp acknowledges two external security researchers, Francisco Oca (offensive security engineer at Cruise) and Mike Ruth (staff security engineer at Brex), whose work around the Terraform Cloud and Terraform Enterprise security models and engagement with our team helped shape this new feature. For information about security at HashiCorp and the reporting of security issues, please see Security at HashiCorp.
»Controlled Remote State Access
The new remote state sharing feature is designed to help manage which workspaces have access to each others’ state files while using the terraform_remote_state data source. This is important because the data source requires access to the entire remote state file.
With Controlled Remote State Access, each workspace in Terraform Cloud and Enterprise will now see a new setting on the General Settings page. The remote state sharing option will allow users to share the current workspace’s state globally within the organization, restrict sharing to specified workspaces, or not allow sharing at all.

The default sharing configuration for all new workspaces is to restrict sharing its state with any other workspaces. All existing workspaces will continue to be globally shared within their organization. HashiCorp does recommend reviewing whether any existing workspace states should be shared and configuring the remote state sharing setting in accordance with the principle of least privilege.
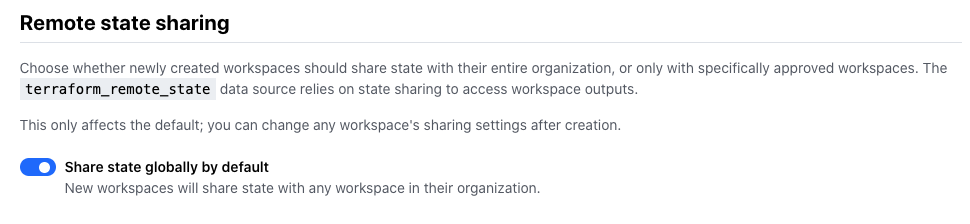
Terraform Enterprise customers will also find a new setting in the admin portal. This separate remote state sharing option will configure the default setting for every workspace in that environment to either be shared globally or not shared at all.
»Terraform Core Updates
The latest release of Terraform Cloud and Terraform Enterprise has one more security-focused update not related to state file accessibility. You’ll notice there are new, incremental versions of many Terraform Core releases. These versions have been added to address security bulletin HCSEC-2021-12. We have taken steps to ensure existing workflows will not break on existing releases of providers, but we do recommend updating to the latest incremental version of Terraform within your workflows. Additional information about Terraform updates for HCSEC-2021-12 can be found in the following link.
»Summary
HashiCorp takes a security-first posture in its commercial product offerings. Our focus is on addressing the concerns of organizations considering our cloud and self-managed offerings to run their business. Controlled Remote State Access builds on this posture by adding a new, more granular way to control accessibility to each Terraform workspace’s state file.
Terraform Cloud is free to try, and organizations can upgrade to the Team & Governance or Business tiers at any time. To get started, sign up for Terraform Cloud and follow our Get Started tutorial or contact HashiCorp Sales if you’re interested in self-managing Terraform Enterprise. For more information on security and compliance, see our Security at HashiCorp page.








