When it comes to the successful deployment and management of multi-cloud infrastructure there are many important considerations, but none are more important than security. HashiCorp’s second annual State of Cloud Strategy Survey (commissioned by HashiCorp and conducted by Forrester Consulting), found that 89% of respondents see security as a key driver of their cloud success.
Let’s take a closer look at this shift, including why multi-cloud raises complex new security challenges and the role automation and zero trust security plays in implementing and maintaining a strong security posture.
»Why Is Cloud Security So Important?
Moving to multi-cloud is helping IT decision makers accomplish their business goals (90% of survey respondents said multi-cloud helped them advance or achieve their company’s business goals) but the complexity of managing multiple technologies and processes creates real operational challenges, including:
- Managing access by IP addresses: In cloud-based environments, IP addresses are dynamic and ephemeral, which makes managing access at scale brittle and complex. Securing infrastructure, data, and access becomes increasingly difficult across multiple clouds and on-premises datacenters, requiring lots of overhead and expertise.
- Securing machine connectivity: Machine-to-machine access is a core element of a cloud-first organization and legacy security approaches are typically too brittle to manage the numerous connectivity requirements of a dynamic environment. With digital transformation initiatives and the introduction of cloud-based infrastructure, environments are more susceptible to credential abuse and operators have to mitigate the inevitable secret sprawl in dynamic environments.
- Scaling security posture with demand: Traditional access and identity management with manual processes are slow, inefficient, and ineffective. Security measures like tokens, key cards, and passwords require direct IT intervention and can consume significant resources and time, especially when required for hundreds or thousands of individual users and machines.
When the shift to the cloud occurs without enhancing security protocols, organizations are left vulnerable to breaches that can cost millions of dollars to remediate. In fact, in 2021, the average cost of a data breach was $4.24 million, according to a recent IBM report.
The complexity of managing and securing multi-cloud environments is already top of mind for decision-makers — our survey found that organizations ranked security as the most significant challenge to the success of their cloud strategy.
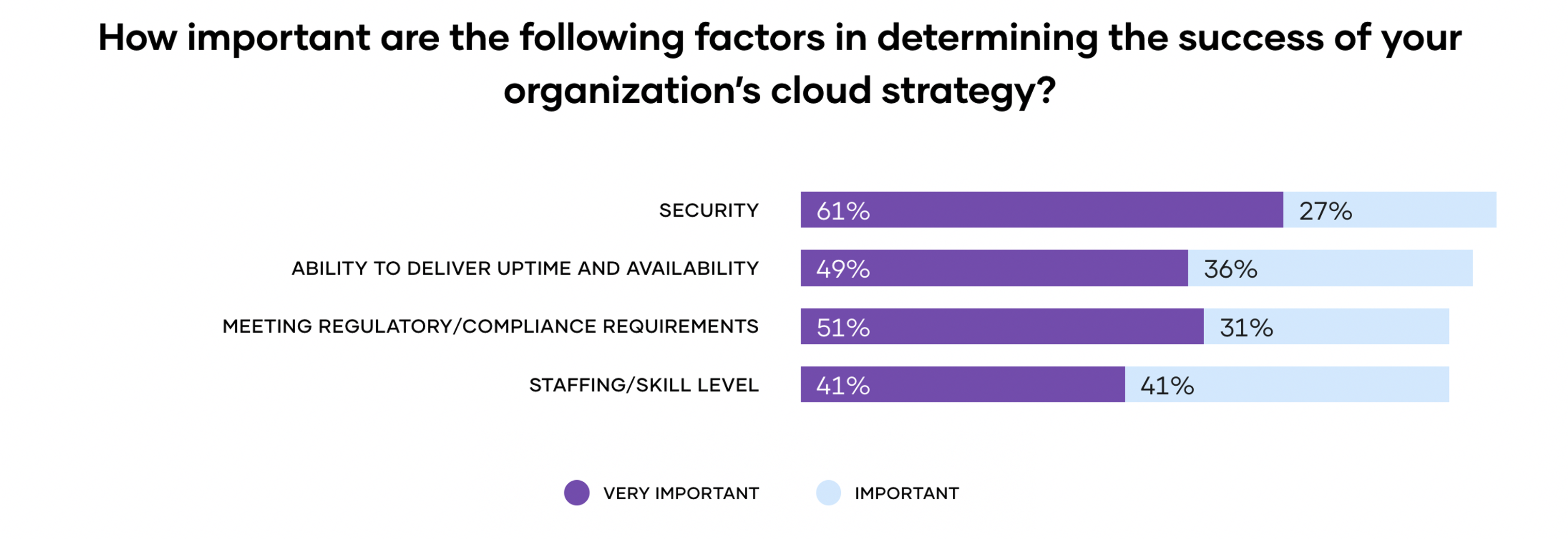
Security vulnerabilities and the associated costs mean organizations are rethinking how to best secure their applications and infrastructure. So how can organizations protect themselves while still taking advantage of the multi-cloud opportunity?
»Automated Security Tools Are Key
It’s not surprising that our study found that the complexity of managing a multi-cloud environment was ranked as the most significant internal challenge to cloud security. But there is hope: 46% of respondents say that consistent and automated tooling would improve their security and governance posture.
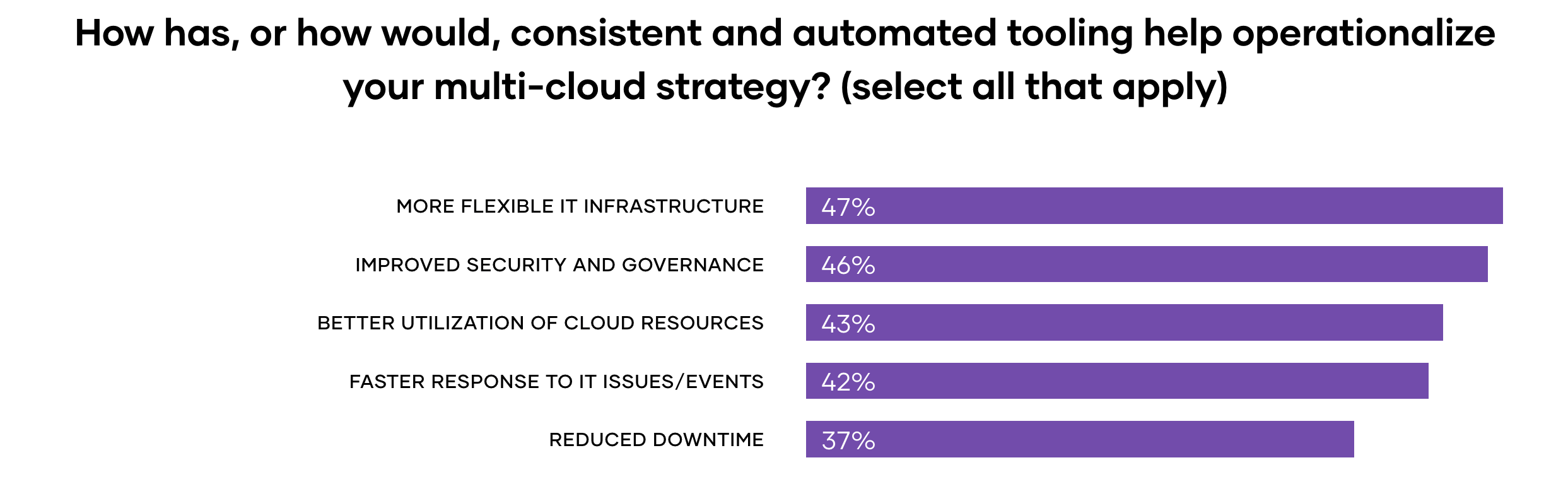
To mitigate risk and protect their environments, organizations are choosing to leverage automated security tools. Survey respondents are realizing the benefits of automated tools and 61% say that they already have or will benefit from automated security tooling to implement zero trust security.
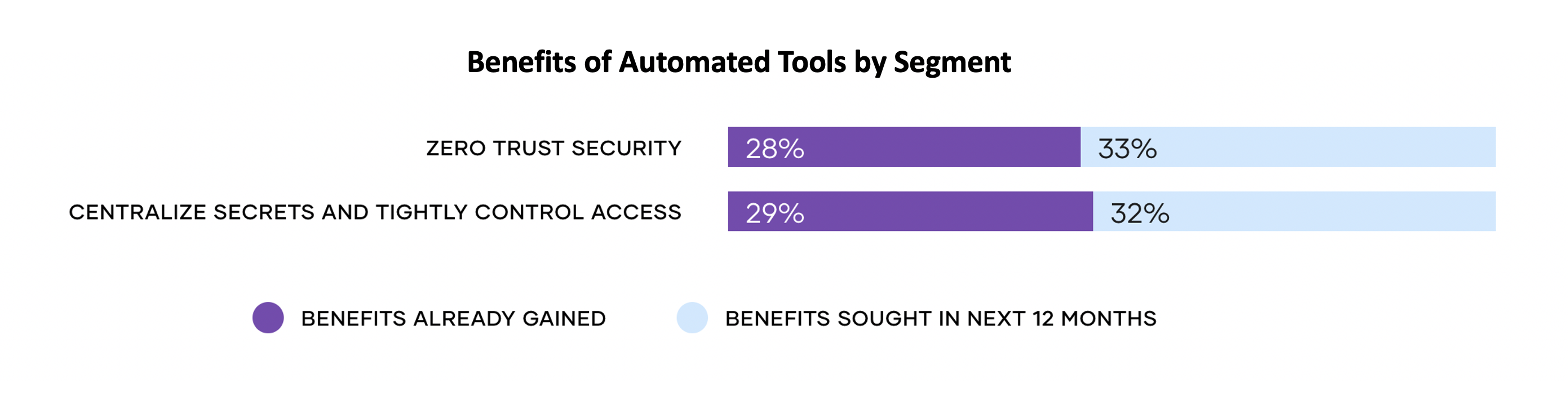
»Zero Trust Security Is King
Zero trust security addresses the new requirements presented with securing the adoption of multi-cloud infrastructure. It is based on the idea that anything or anyone trying to gain access to the network needs to be authenticated and authorized. Access is granted based on a specific set of pre-determined policies, such as user role, location, or device type. By implementing identity-based access controls, granting only least-privilege access, and issuing dynamic credentials, organizations can work towards a zero trust environment.
HashiCorp’s zero trust security solution combines the power of HashiCorp Vault, Consul, and Boundary to provide an automated approach for organizations migrating their infrastructure, applications, and data to multi-cloud. Implementing zero trust security can:
- Improve security posture with the implementation of identity-based authorization and access controls. By granting only just-in-time access with dynamic controls, organizations can help ensure that only those who are authorized have access to only the things they need for only the amount of time necessary.
- Reduce the likelihood of a breach by eliminating secret sprawl. With HashiCorp, users can authenticate and authorize everything for machine and human-to-machine authentication, authorization, and access.
- Accelerate multi-cloud adoption by securing all clouds with centralized secrets management. Centrally storing and accessing secrets (tokens, passwords, certificates, encryption keys, etc.) decreases the surface area eligible for an attack. Users can streamline actions and access one tool instead of various secrets management tools across their stack.
By implementing a comprehensive zero trust security approach, organizations can work to improve their security posture. HashiCorp’s zero trust solution does just that, helping ensure that organizations have the tools and controls they need to authenticate and authorize users and machines at all layers of a dynamic network, based on identity.
The shift to multi-cloud and its complex new security challenges is inevitable. Organizations can work to protect themselves by incorporating an automated zero trust security framework. This security strategy helps detect and remediate security vulnerabilities while also protecting businesses from expensive breaches.
For the full story on multi-cloud security and more, including the charts and graphs that make it easy to visualize the numbers, visit the HashiCorp State of Cloud Strategy Survey site. You'll find links to the Forrester Consulting “Unlocking Multicloud’s Operational Potential” study based on the survey, which is free to download. And for more on zero trust security, be sure to attend HashiConf Global, Oct. 4-6 in Los Angeles and online. Register today.








